VIPRE Server provides flexibility over the deployment of agent software and definition updates. In this article, we show you the options available and how to select the right amount of control for your needs.
Types of Updates and Distribution
There are two different types of updates:
| Type of Update | How it's Distributed |
|---|---|
| Threat Definition Updates | Identify and remediate malware in your environment and are updated several times each day, as often as hourly. The full threat definitions are approximately 70 MB and reside on each machine that contains a VIPRE Agent. The average update chunk size is approximately 67 KB. |
| Software Updates | Pertain to the Agent software and can occur a few times a year. These software updates can include patches, version releases, or Beta releases (Beta releases are only made available by request) for VIPRE Antivirus Business, VIPRE Business Premium, and VIPRE Endpoint Security Server. |
How are updates distributed to Agents?
When an agent is first installed, it immediately gets threat definitions updates. The Agents receive ongoing updates based on the policy they are assigned. Both definitions and software updates are sent from VIPRE Site Service (VSS) on port 18082. If you enable “Download via the Internet if local updates are unavailable,” Agents will obtain their definition updates from VIPRE Security’s update server on port 80 - if they are unable to contact the update server specified in the policy. Note that updates are NOT delivered from the VIPRE Admin Console or by a request over the Internet from the Agent.
Configure Updates for Your Environment
In order for VSS to get the updates for distribution, it is required that both Simple Object Access Protocol (SOAP) headers and Internet access be allowed from the machine that is hosting VSS to the external Internet.
Set SOAP via port 80 outbound and inbound for the following:
- updates.sunbeltsoftware.com checks for software updates and allows software and definition updates to be distributed.
- ne.edgecastcdn.net allows software updates and definition updates to be distributed.
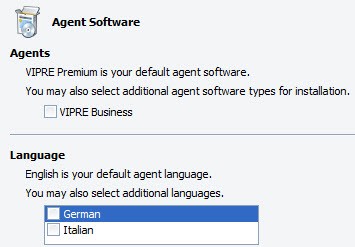
Specify Agent Software Editions
Select the agent software that is appropriate for your business. The Agents selected will be downloaded according to your Site Updates settings and then applied according to the Agent Updates policy settings.
To select agent software for the Site:
- In the Site Properties, open the Agent Software screen
- In the Agents area, select the applicable version of Agent
- If applicable, in the Language area, select the languages
- To accept changes, click Apply
Manage Site Updates
Manage updates for Sites from the Updates screen in the Site Properties. Updates are checked at VIPRE Security and require an Internet connection. If your Site requires a proxy to reach the Internet, configure the Site's Proxy Settings.
Configure automatic updates for the Site:
Set VIPRE to automatically retrieve updates at either a regular interval or at specified times.
- In the Site Properties, open the Updates screen
- In the Update server area, configure the following:

- HTTP: if enabled, Agent software updates will be transferred over HTTP using the specified port. Agents prior to version 11.0 require HTTP to receive updates.
-
HTTPS: if enabled, Agent software updates will be transferred over HTTPS using the specified port. This is the default setting for Agents version 11.0 and later.
Note! When using HTTPS, you can also view or change your Certificate information.
Network address: The address(es) that the web server listens on. The default is All, or you can enter specific IP addresses.
- In the Automatic Updates area, configure the following:
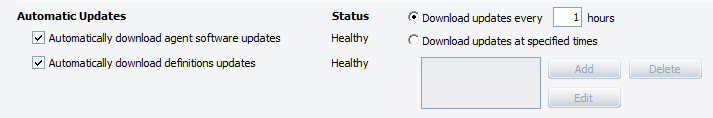
- Automatically download agent software updates: if disabled, Agent software updates for this site will NOT be automatically checked; you will have to get agent software updates manually from the "Updates Override" area below.
- Automatically download definitions updates: if disabled, threat definition updates for this site will NOT be automatically checked; you will have to get definitions updates manually from the "Updates Override" area below.
- Download updates periodically: select to receive updates at regular intervals.
- Updates check interval in hours: enter a number between 1 and 72 hours.
- Download updates at specified times: select to receive updates at the times that you create.
- To accept changes, click Apply
Manually update software and definitions for the Site:
- In the Site Properties, open the Updates screen
- In the Updates Override area, configure the following:
- To check for agent software updates, click Agent
- To check for definition updates, click Definitions
- To accept changes, click Apply
Check version status for software and threat definitions:
The Software and Threat Definitions Version Status area displays the following information. The table below describes the meaning of each column.

| Column Name | Description |
|---|---|
| Agent Product | Displays the product name of the agent |
| Language | Displays the language of the update |
| Agent | Displays the last version number of the agent software that is available |
| Last Software Update | Displays the date and time for this version of the agent software |
| Definitions | Displays the last version number for Definitions that is available |
| Last Definitions Update | Displays the date and time for the version listed in the Definitions column |
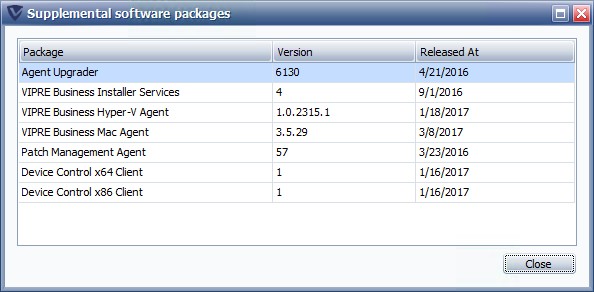
Supplemental package updates
Version information is also available for VIPRE's "supplemental packages", the sub-components included with VIPRE. This information is intended for use by VIPRE Support.
- Click View version for supplemental packages to display the version information.
The Status column under Automatic Updates displays the following status types:

- Healthy indicates that automatic updates have no errors and that it is operating normally; not actively doing anything.
- In progress indicates that updates are being downloaded.
- Warning indicates that there is an intermittent error of no Internet connectivity, and will automatically try again. Check the VSS logs for more information.
- Task pending indicates that VSS is waiting to pick up the task.
- Work in progress indicates that VSS is actively performing the task.
- Error indicates that an error is in a continuous state. Check the site logs for more information.
The bottom Status area displays the following information:

- Last update check at displays the date and time that updates were last checked, whether it was done automatically or manually.
- Next update check at displays the date and time that updates are scheduled to be automatically checked.
Manage Agent Updates for Policies
Updates are distributed to machines based on the Agent Updates settings for each Policy. Agent update settings help you manage the impact to network traffic and machine performance when Policies distribute updates to Agents.
To manage the distribution of updates per policy:
- Open the Agent>Updates screen in the Policy Properties for each Policy.
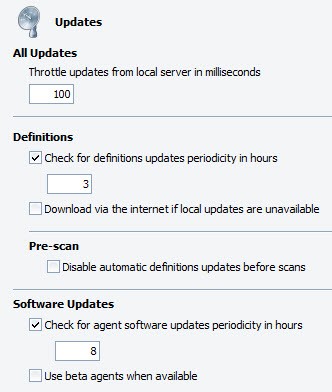
- Set Throttle updates from local server in milliseconds to cut down the load on the update server when distributing updates to the machines under the selected policy. The default value for throttling is 100 milliseconds but can be set as high as 60,000 milliseconds (or 1 minute) for networks with extreme bandwidth constraints. The average update chunk size is approximately 67 KB. A general guide:
- 1 MBPS network: 1000 milliseconds
- 10 MBPS network: 200 milliseconds
- 100 MBPS network: 50 milliseconds
- 1 GBPS network: 20 milliseconds
- Configure automatic Definition Updates for Agents under this policy:
- Select Check for definitions updates periodicity in hours to turn on automatic definition updates and then enter a number in hours for the update interval. The default is to automatically check at 1-hour intervals.
The interval values are 1-72 hours. Best set between 1 and 3 hours. The default start time for updates is when the computer first boots up.
For example, if the computer boots up at 7:43 a.m. and checks for updates every 3 hours, it will check at 10:43 a.m., 1:43 p.m., 4:43 p.m., and so forth. - The Disable automatic definitions updates before scans setting:
- Best Practice! To ensure the Agent automatically gets the latest definitions before running a scan, Unselect this option
- If the interval for definitions updates is set to be frequent (1-3 hours) or for older model hardware that runs slower, select this option
- Select Check for definitions updates periodicity in hours to turn on automatic definition updates and then enter a number in hours for the update interval. The default is to automatically check at 1-hour intervals.
Note! This setting should be done in conjunction with the Scan setting "Randomize scheduled scan start times in minutes."
- To have Agents on laptops (or remote users) connect to VIPRE Security over the Internet if the agent fails to contact VSS or the update server, select Download via the Internet if local updates are unavailable.
- If machines require a Proxy to access the Internet, ensure that you configure Policy proxy settings.
- You may also specify that all updates come directly from VIPRE Security, instead of an update server.
Note! If this is used for agents over your network, this could put a strain on the WAN
- Configure Software Updates for Agents under this policy:
-
Best Practice! To turn on automatic software updates, select Check for agent software updates periodicity in hours, and then enter a number in hours for the update interval.
The default setting is on and at 8-hour intervals. The interval values are 1-72 hours. - To turn off automatic software updates, unselect Check for agent software updates periodicity in hours.
- To participate in Beta releases, select Use beta agents when available.
This is best used under policies with a limited number of agents and non-production machines.
Note! Use this option with care. If you need to rollback to a previous version, a manual uninstall and reinstall of each agent may be required.
-
Best Practice! To turn on automatic software updates, select Check for agent software updates periodicity in hours, and then enter a number in hours for the update interval.
- To accept your changes, click OK
All changes are applied to the Agents assigned to the Policy the next time the Agent communicates to the Site.
Create Remote Update Servers
Additional update servers are beneficial for companies operating at more than one physical location and trying to manage loads on Internet traffic. For example, let's say your primary location is in New York and you have a secondary office in San Diego. Having an update server in San Diego would put less burden on bandwidth—the agents in San Diego would not have to connect over the Internet to get updates; instead, they can get them locally from the secondary update server.
Basically, run the Full VIPRE installation on a secondary machine, which will be used as the “Update Server.” Then, download the latest updates and assign policies to the new update server.
Important! Use Static IP Addresses only.
To create a remote update server:
Set VIPRE to automatically retrieve updates at either a regular interval or at specified times.
- Download your product installer.
- Run the installer on the machine that will be the update server, ensuring that "Full Installation" is selected. Follow all default settings.
- Configure the following in the Site Properties:
- On the Registration screen, use your main license key
- On the Updates screen, ensure that the threat definitions and agent software updates have been downloaded, as indicated in the “Status” column. Please be patient, as this may take a few minutes
Note! Installing additional update servers does not require a new key or the purchase of additional software licenses. However, entering your existing key is required in order for the update server to receive updates.
- From the primary machine where VIPRE(this is also known as the "main policy server") is installed, change the update server settings for the desired policies:
- In the Policy Properties, open Agent>Communication.
- Under Update Server, enter the IP address and port number of the machine you just installed on, which will be the update server.
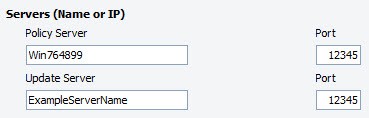
- Click Apply
- To create additional update servers, repeat Steps 1-5
- To assign additional policies to the update server, repeat Steps 4-5
Tip! You can copy the update server setting to other policies.
The remote update server is now configured. Agent polices will still be administered via the main policy server, while updates will be handled via the update server.
Using VIPRE Security for Updates
In older versions of VIPRE Endpoint Security Server (prior to 9.5), entering a fake update server address was one method of reducing traffic from agents to VSS. When the server connection to the fake address failed, agents would then attempt to seek updates directly from VIPRE Security.
Using this method, only definitions (and not software updates) were available as updates to agents. Now, both software updates and threat definitions may be downloaded directly from VIPRE Security. You may also select VIPRE Security as your preferred update server.
To use VIPRE Security as a (non-local) update server:
- In the Policy Properties, open Agent>Communication
- Check Use VIPRE Security as Update Server for definitions and software updates
- Click OK.
Note: Using VIPRE Security as your update server may increase your internet traffic.