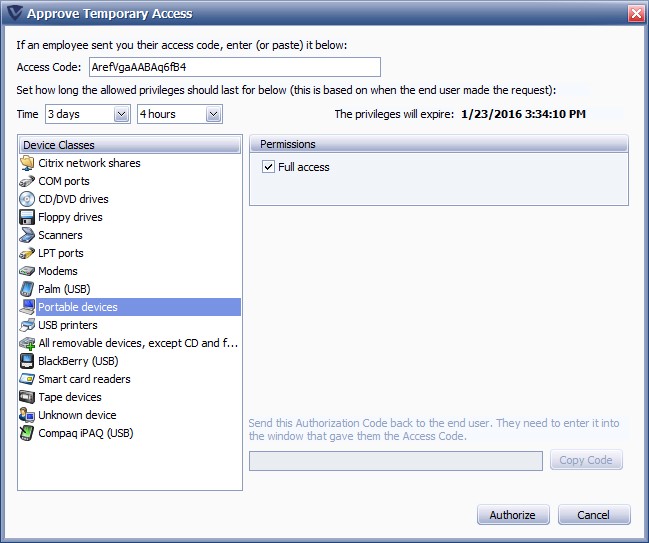
In this section, you will find information on configuring device control through policy settings.
Device Control for Windows endpoints allows for the administration of external devices interacting with remote agents. This option is useful for limiting how users may transmit sensitive information to third-party devices, as well as protecting the endpoint from potential third-party threats.
Configure Device Control for Windows Devices
Important
Device Control is a powerful feature that requires low-level access to device drivers. Because of this integration, Device Control can be incompatible with certain device drivers, particularly older versions. We recommend testing Device Control carefully on target systems before production deployment.
A reboot is required if:
- If your devices with VIPRE Agent v12.2 or older have Device Control enabled
- If you've enabled Device Control within a policy that has existing agents v12.2 or older
- If Device Control was previously disabled and the agent machine(s) haven't rebooted since Device Control was disabled
- If you've disabled Device Control within a policy that has existing agents v12.2 or older
A reboot is not required if:
- If your devices with VIPRE Agent v12.2 or older have Device Control disabled
- If you're performing a clean install of VIPRE Agent v12.3 with Device Control disabled
- If you're performing a clean install of VIPRE Agent v12.3 with Device Control enabled
- If you've enabled Device Control within a policy that has existing agents v12.3
- If you've disabled Device Control within a policy that has existing agents v12.3
Device Control allows you to manage the following features:
- Recover a user password
- Allow end-users to request temporary access
- Approve temporary access
- Port blocking
The Enable Device Control checkbox acts as the "master switch" to enable/disable Device Control for the current policy. Unchecking Enable Device Control turns off all Device Control options for the current policy (though you may still recover user passwords as needed).
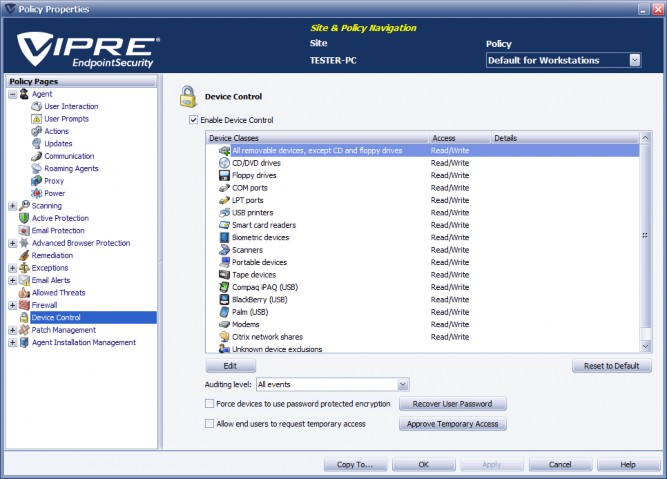
Legacy Media Password Recovery
When an encrypted device is inserted into a machine, the user will be prompted to enter a password in order to access the device. If they do not know their password, they may click the Recover Password button to initiate the recovery process.
If the user fails to enter the correct password within 5 attempts, they will be locked out of accessing the device, and presented with instructions to contact their Administrator. Clicking on the device in Windows Explorer at this point will result in an "Access denied" message. To unlock the device, the user should remove and then reinsert the device. This will also initiate the Recover Password process.
To recover a password for an encrypted device:
- When a user clicks the Recover Password button, they will be presented with an Encrypted Medium ID and Security Code, which they should send to you.
- In the Policy Properties, select Device Control, and then Legacy Media Password Recovery
- Key in (or copy and paste) the Encrypted Medium ID and Security Code from the user into the appropriate fields; then, click Generate Passphrase.
- Provide the passphrase to your user.
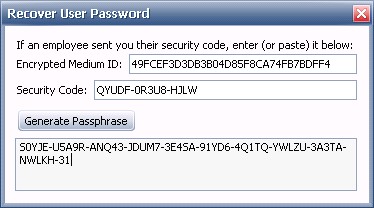
Allow End-users to Request Temporary Access
When enabled, a user may request temporary access for a device that is otherwise universally blocked based on the policies affecting the user. The user will provide you with an access code, which you use to approve and define the limits of the temporary access with.
When granting temporary access, you specify the device type, the read/write capability, and the time until the temporary privileges expire.
Approve Temporary Access
When a user requests temporary access, you must manually approve the request. A separate request is required for each device.
To approve a temporary access request:
- In the Policy Properties, select Device Control. Click the Approve Temporary Access button
- Enter the Access Code that the user has provided
- Select the Device Type from the drop-down, and click the appropriate Read/Write or Read Only checkboxes
- Select the Time until the privileges expire using the Time drop-downs
Note! The time remaining starts from when the agent generates the access request. - Click Authorize. You will receive an authorization code
- Provide this authorization code to your user
Port Blocking
You may select Deny Access or Read Only for specific device ports across an entire policy.
To manage device ports:
- In the Policy Properties, select Device Control
- Double-click on a Device Class
- Select the appropriate permissions for the device, and click OK
- Click OK or Apply

You may also adjust port blocking for specific devices, certain types of devices, and Users or Groups via Device Exclusions.
View Device Control Events
An additional Device Control tab has been added to the Site Navigator grid for each policy which allows Device Control. This tab displays an overview of Device Control related information.

The Device Control tab displays audit trail information for all devices affected by the currently selected policy. Information is presented for Time, Event Type, Device Type, Device Name, Model ID, Hardware Serial Number, Agent Name, and Policy.
From this tab, you may quickly create a User Exclusion or a Device Exclusion.
Device Exclusions
You may exclude devices from the current policy by creating device exclusions. Excluded devices are exempt from policy settings that would otherwise affect them.
Exclusions fall into these categories:
- Specific devices – A single device identified by its Windows device ID
- Device types – A selection of device types, chosen from the Allowed Privilege list
- Users - All devices belonging to an Active Directory user
- Groups - All devices belonging to an Active Directory group
Note! Users and Groups are only available if your machine is part of a domain environment.
Create a Device Exclusion
To exclude devices by type
- In the Policy Properties, select Device Control
- Double-click on a Device Class
- Click Add
- Enter a name for the exclusion.
- Select the appropriate permissions for the device, and click OK
- Click OK; then, click OK or Apply
To exclude a specific device
- In the Site Navigator, select the policy that controls the device; then, click the Device Control tab
- Right-click the device and select Create Device Exclusion...
- Enter a name for the exclusion
- Select the appropriate permissions for the device, and click OK
- Click OK; then, click OK or Apply
Or
- In the Policy Properties, select Device Control
- Double-click on a Device Class
- Click Add
- Enter a name for the exclusion
- Select the appropriate permissions for the device
- Enter the Model ID and Hardware serial number for the device, and click OK
- Click OK; then, click OK or Apply
To exclude devices belonging to a connection
- In the Policy Properties, select Device Control
- Double-click on a Device Class
- Click Add
- Enter a name for the exclusion
- Select the appropriate permissions for the device
- Click Add
- Select the Group(s) you wish to exclude and click Add..., then click OK
- Click OK; then, click OK or Apply
Edit or Remove Device Exclusions
To remove a device exclusion
- In the Policy Properties, select Device Control
- Double-click on a Device Class
- Select an exclusion and click Remove
- Click OK; then, click OK or Apply
To edit a device exclusion
- In the Policy Properties, select Device Control
- Double-click on a Device Class
- Select an exclusion and click Edit
- Make your changes, then click OK
- Click OK; then, click OK or Apply
Best Practices!
Test Device Control before deployment
Device Control is a powerful feature that requires low-level access to device drivers. Because of this integration, Device Control can be incompatible with certain device drivers, particularly older versions. We recommend testing Device Control carefully on target systems before production deployment.
Device Control policies and agent reboots
When a policy with Device Control is enabled, agents with this policy need to be rebooted. If Device Control is disabled before that first reboot can occur, the agents may request a second reboot.