File Analysis allows you to upload any file to be analyzed by VIPRE then shows the result within a table that is filterable by date/time, status, risk, or user. This article will walk you through how to use VIPRE's File Analysis.
Upload your file for Analysis
There are several ways to submit your file for analysis.
Option 1: From the File Analysis screen
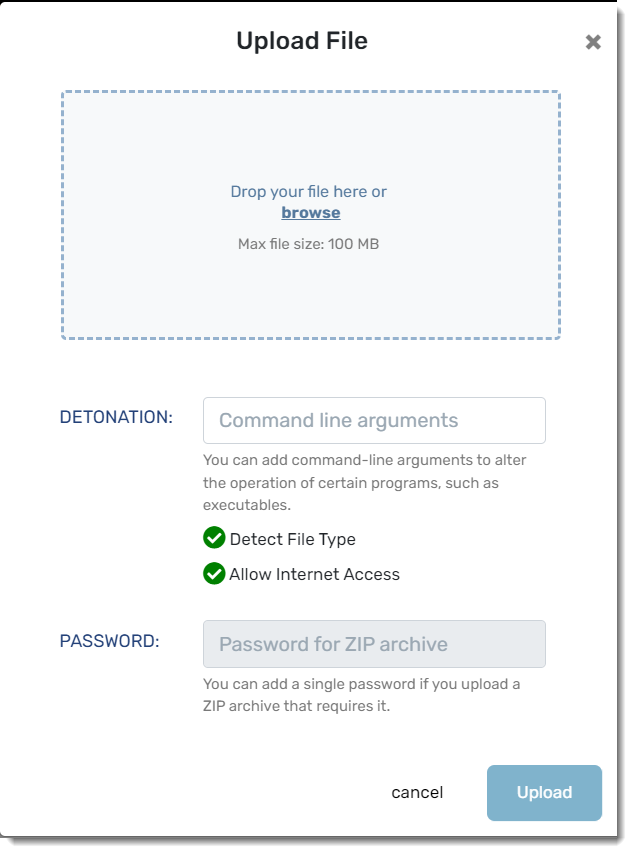
- Click the Upload File button in the top-left corner of the screen
- The Upload File window will pop up; add your file by dragging it from the directory folder or select browse to navigate to the file
- Maximum file size is 100MB
- If the file requires any command line arguments (such as an executable), you can add those in the text box next to Detonation
- Detect File Type and Allow Internet Access are checked by default; to disable these options, uncheck them
- If you're uploading a .ZIP file that requires a password, you can include that password in the text box next to Password
- Click the Upload button
Option 2: From the Shell History Report
If any files were saved as ‘evidence’ during a remote session, it will show on the Shell History Report in the Evidence column as a clickable link. Click on the desired session files to see file details and select Submit to Sandbox. In fact, anywhere within the VIPRE EDR console you see the Submit to Sandbox icon, you can submit a file for analysis.

Review the Analyzed File Summary
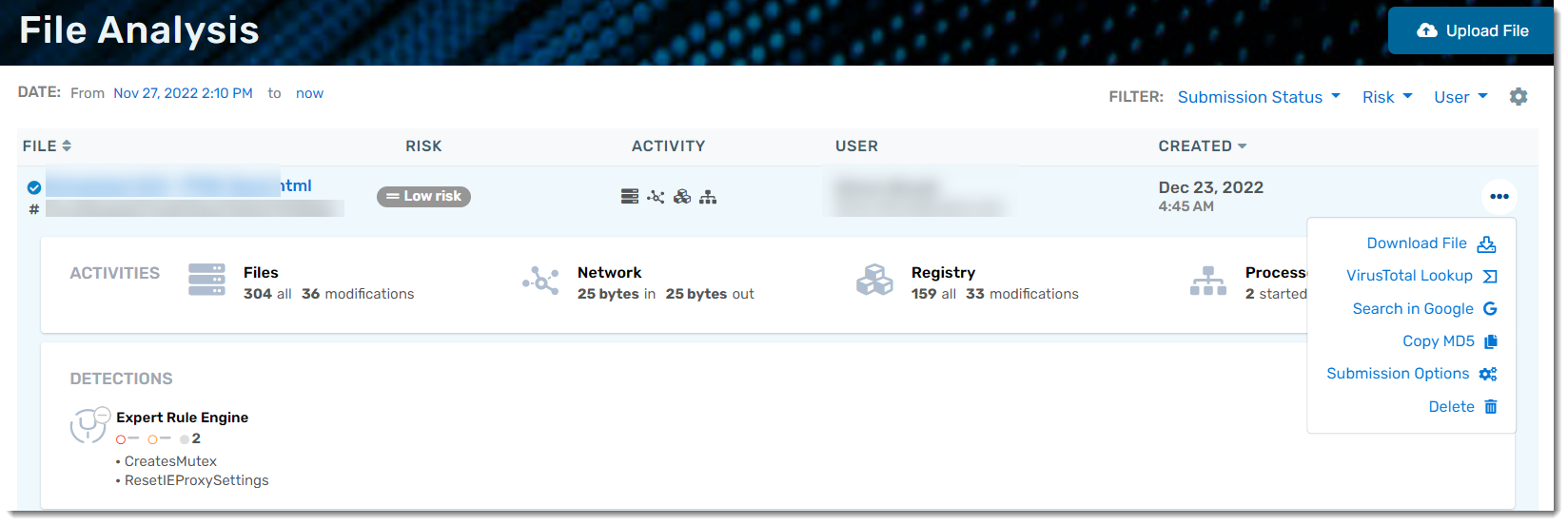
- Once a file has been analyzed, the details can be found by navigating to Investigate > File Analysis
- A table shows the file name, the risk level, activities performed during the analysis, the user who loaded the file, when the file was originally analyzed, and available actions
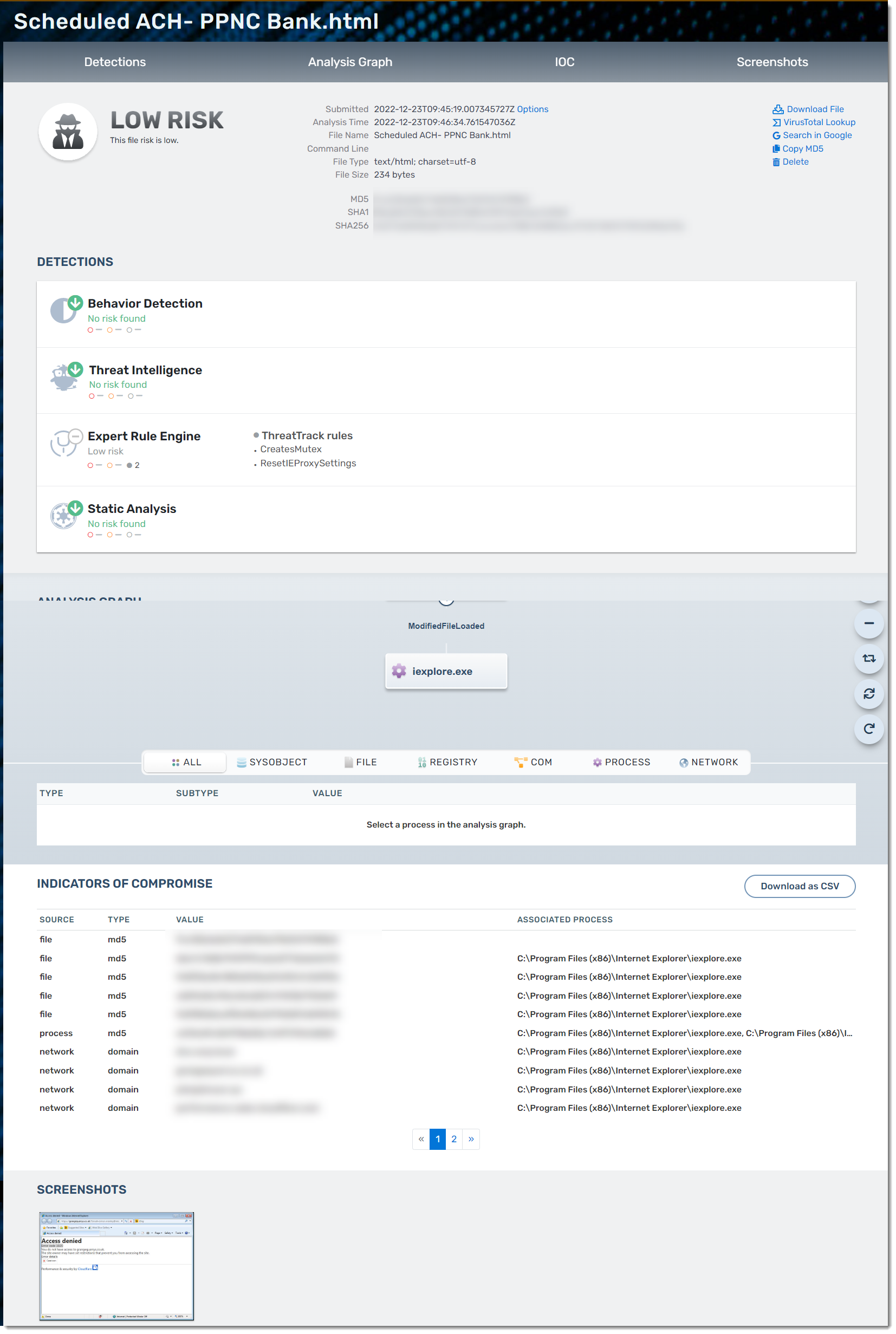
Review the Analyzed File Details
- You can drill down and find more details by clicking on the file name link under the File header of the File Analysis table
- Details on this screen include:
- Specific file details including risk level, available actions, etc
- Whether any threats were found and by which detection engine
- Analysis Graph
- IOC (Indicators of Compromise) helps explain what makes this file appear as a threat (if it is)
- Screenshot of the file which can be clicked on to see a larger version