Product release information for VIPRE Email Security Cloud, released on November 10, 2022.
What's New
We're excited to announce the launch of Email Analytics as part of VIPRE Email Security Cloud! Email Analytics is made up of two parts - Link Click Analysis and Threat Explorer.
Important
- Link Click Analysis requires the Link Isolation add-on or the Advanced Threat Protection package
- Threat Explorer requires the Attachment Sandboxing add-on or the Advanced Threat Protection package
Select a topic below to learn more!
Link Click Analysis
Link Click Analysis provides details relating to links within received emails that users in your organization clicked. This content explains the data presented in this view.
Important
Link Click Analysis is only available for VIPRE Email Security Cloud customers with the Link Isolation add-on or the Advanced Threat Protection (ATP) package.
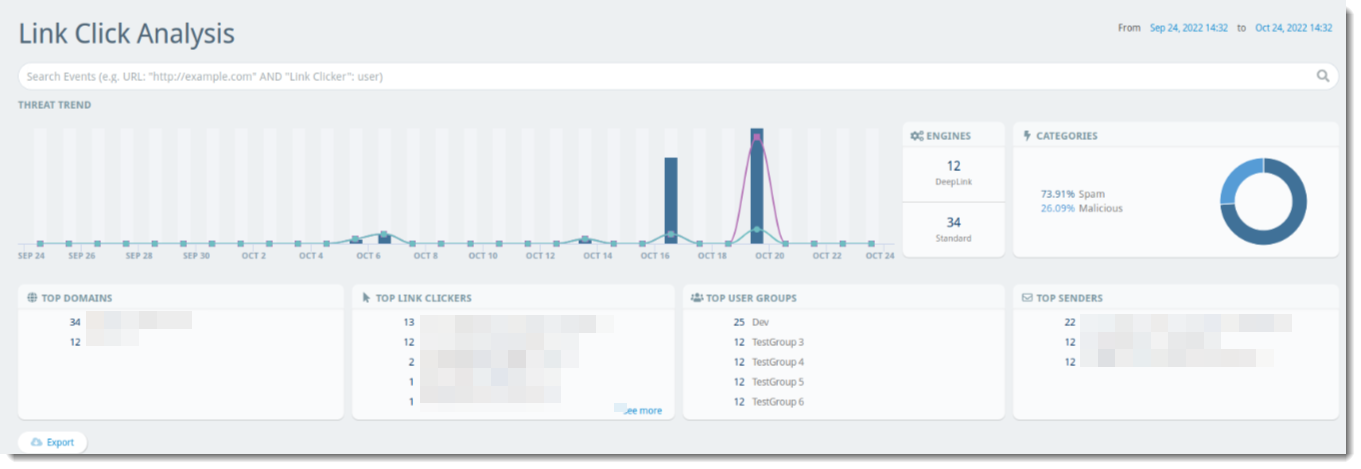
Threat Trend
The Threat Trend bar graph shows dates and times when users within your organization may have clicked potentially harmful links. You can filter the table by clicking on a specific point on the bar graph to show only that date/time based on the Time column.
Engines (TDE)
- DeepLink - Items in the threat table labeled with DeepLink should be given special consideration as these could potentially indicate a new, unknown threat or a targeted attack
- Standard - Items found with the Standard Threat Detection Engine are known to be malicious
You can filter the table by clicking on the desired engine (Standard or DeepLink) in the widget to show only that category.
Categories
Links that are clicked are categorized in one of the following ways:
- Malicious - Items categorized as Malicious are known malicious sites
- Suspect - Items that have been identified as suspicious sites, possibly unknown threats
- Spam - Items that have been identified as spam based on your configured policies
In cases of items marked as Malicious, Suspect, or Spam, you can select that line item for more details such as the affected URL, the user who clicked the link, their IP and browser version, as well as the sending email address and when the email was received. You can filter the table by clicking on the desired category (Malicious or Suspect) in the donut chart to show only that category.
Top Domains
A list of the top 5 domains with suspicious or known malicious URLs sent to emails within your organization. You can filter the table by clicking on the desired domain in the Top Domains list to show only that domain under the URL column.
Top Link Clickers
A list of the top 5 users who click suspicious or known malicious URLs within their email. You can filter the table by clicking on the desired user in the Top Link Clickers list to show only that user under the Link Clicker column. Clicking "See More" expands the list of Top Link Clickers in a drill down report.
Top User Groups
A list of the top 5 user groups who click suspicious or known malicious URLs within their email. You can filter the table by clicking on the desired user group in the Top User Groups list to show data specifically for that group.
Top Senders
A list of the top 5 email addresses that send suspicious or known malicious URLs via email to your organization. You can filter the table by clicking on the desired email address in the Top Senders list to show only that address under the Sender column. Clicking "See More" expands the list of Top Senders in a drill down report.
Threat Explorer
Threat Explorer provides details about all types of threats within emails that users in your organization received. This content explains the data presented in this view.
Important
Threat Explorer is only available for VIPRE Email Security Cloud customers who have the Attachment Sandboxing add-on or the Advanced Threat Protection (ATP) package.
You can choose date ranges by clicking on the dates in the top-right corner.
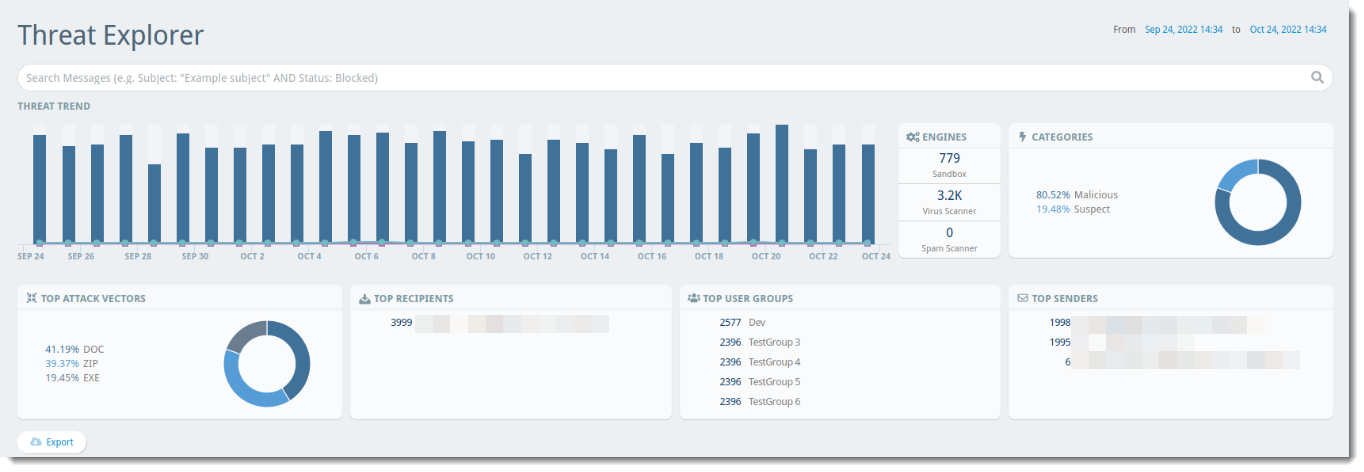
Threat Trend
The Threat Trend bar graph shows dates when potentially threatening mail was received within your organization. You can filter the table by clicking on a specific point on the bar graph to show only that date/time based on the Time column.
Engines
- Sandbox - Attachment Sandboxing Add-on is required for this; indicates the percentage of potentially harmful attachments that were caught and quarantined
- Virus Scanner - Indicates the percentage of emails with potential viruses caught and quarantined
- Spam Scanner - Indicates the percentage of spam emails caught and quarantined
You can filter the table by clicking on the desired engine (Sandbox, Virus Scanner, or Spam Scanner) in the widget to show only that category.
Categories
Emails that are received are categorized in one of the following ways:
- Suspect - Items categorized as Suspect are suspicious but not confirmed threats
- Malicious - Items categorized as Malicious are known threats
- Spam - Items categorized as Spam are based on your configured policies
- Bulk - Items categorized as Bulk are based on the bulk email filter and are generally “newsletter” type messages
- Phishing - Items categorized as Phishing are based on the Spam scanner and your configured policies
In all cases, you can select that line item for more details such as the sending email address and when the email was received, and more. You can filter the table by clicking on the desired category in the donut chart to show only that category.
Top Attack Vectors
A list of the top 5 types of attacks sent via email. (For example, 29.74% EXE, 24.03% ZIP, 13.04% URL would indicate 29.74% of the attacks were in the form of an executable file, 24.03% were in the form of a .zip file, and 13.04% were in the form of a malicious link.) You can filter the table by clicking on the desired vector in the Top Attack Vectors list to show only that category.
Top Recipients
A list of the top 5 email addresses in your organization that receive suspicious or known malicious messages. You can filter the table by clicking on the desired email address in the Top Recipients list to show only that address under the Recipient column.
Click on “See More” to expand the list of Top Link Clickers.
Top User Groups
A list of the top 5 user groups in your organization that receive suspicious or known malicious messages. You can filter by clicking on the desired group in the Top User Groups list to show data for that specific group.
Top Senders
A list of the top 5 email addresses that send suspicious or known malicious messages to your organization. You can filter the table by clicking on the desired email address in the Top Senders list to show only that address under the Sender column.
Clicking "See More" expands the list of Top Senders in a drill down report.
You can find these reports within the VIPRE Email Cloud console on the left-side menu under the heading Analytics.
New to VIPRE Labs
With this release, we've also created a new addition to VIPRE Labs called Reports.

Under VIPRE Labs > Reports, you'll find four new reports:
-
Top Link Clickers shows you the users who most often click suspicious or known malicious URLs within their email, sorted by frequency
- This is associated with Link Click Analysis mentioned above
-
Top Link Click Senders shows you the email addresses that send the most suspicious or known malicious URLs via email to your organization, sorted by the total number of incoming threats detected
- This is associated with Link Click Analysis mentioned above
-
Top Targeted Users shows you the email addresses in your organization that most often receive suspicious or known malicious messages, sorted by frequency
- This is associated with Threat Explorer mentioned above
-
Top Threat Senders shows you the email addresses that send the most suspicious or known malicious messages to your organization, sorted ny the total number of incoming threats detected
- This is associated with Threat Explorer mentioned above
We want to hear from you!
Whether something is still in VIPRE Labs and you have thoughts to improve it, something that was previously in VIPRE Labs disappeared and you miss it, or you have an idea for something you'd like to see in VIPRE Labs, we want to hear about it! Visit VIPRE Ideas to submit your ideas about this or any other VIPRE product. When submitting your idea, make sure to mention that it is/was a VIPRE Labs feature!
Known Issues
This section lists issues that are known at the time of release. In some cases, these are bugs that we are working to resolve with a subsequent release. Other items may be due to causes outside of our control, such as bugs with other vendors' software. Where possible, we have tried to provide a workaround for you to consider, should you experience an issue.
If you have questions about a specific issue, please provide the issue ID (if applicable) when contacting our Technical Support team.
| Ticket Number | Description |
|---|---|
| AP-8479 |
The total in the Top Recipients widget of Threat Explorer does not match the total in the Top Targeted Users report under VIPRE Labs > Reports. Workaround: The value found in the Top Targeted Users report is correct. |
| AP-8478 | “Export Limit reached" warning message is not displayed when exporting events under Link Click Analysis or Threat Explorer that exceed the 10k limit. |