This article explains the benefits of using LDAP sync for user management and how to enable in Email Security.
What is LDAP sync?
For ease of user management with Email Security, use Lightweight Directory Access Protocol (LDAP) Sync. User information that updates in LDAP will automatically replicate to VIPRE Email Security. This lets you continue to use the LDAP system as a single point of user management.
When LDAP Sync is enabled, Email Security considers LDAP the system of truth. Thus, new users in LDAP are automatically added to Email Security. Disabled or deleted users are automatically deleted from Email Security once the deletion delay interval expires. Email aliases are automatically mapped from LDAP secondary email address data.
The sync process can be scheduled to run every 6, 12, or 24 hours, every three days, or weekly. If immediate sync is needed, such as in the case of offboarding an employee, the Email Security administrator can use the Sync Now action to immediately sync the LDAP changes over to Email Security. Network traffic for the sync process is minimized by Email Security, which places a directory service sync agent local to the LDAP directory service. The data that is transmitted back to Email Security is a subset of the LDAP data.
Summary of benefits
Use LDAP sync to enjoy these benefits
- Quickly add users to a new (or existing) Email Security account
- Keep users' account details updated (e.g., name, phone, notes)
- Easily add email aliases to users' accounts
- Ensure disabled, or deleted users cannot access Email Security
Supported directory services
The Email Security LDAP sync feature has been certified with Microsoft Active Directory Services. Since LDAP is a standard protocol, the feature should work with any standard directory that supports LDAP. However, not all directory implementations use the same attributes to store the same types of information; in some cases, this may cause mismatches in data interpretation. If you are attempting to connect Email Security to some other directory, let us know of any issues so that we can account for different schema mappings.
LDAP sync and manual account management
If desired, user management through LDAP sync can be used in conjunction with manual account management. When used in this manner, the LDAP sync process uses a supplemental approach to reconcile user accounts. For example, an email address that has been manually added to Email Security will have its name, phone number, and notes updated from the directory service data. This also means when the user is disabled or deleted in LDAP, that action will not be recognized in Email Security.
LDAP sync processing considerations
Review the information in this section for an understanding of how LDAP sync works with user management in Email Security.
Synchronization rules
The synchronization process uses these rules when scanning LDAP for updates to make in Email Security. If the rules are not met, then the user is not added to the Email Security account.
- System of truth - when LDAP sync is enabled, it is the system of truth for user management within Email Security
- Primary email address - the domain of the primary email address must match a domain that is managed by the Email Security account
-
Secondary email address (aliases)- the domains of secondary email addresses must match a domain that is managed by Email Security AND the primary email address domain is managed by the same Email Security account.
- list of users - when viewing the list of users, you will see secondary email addresses grouped under the users' account for the primary address
-
Domain changes in Email Security- if a domain is removed from management under Email Security, this results in:
- when the removed domain matches a Primary email domain - the user is immediately removed from Email Security and will not appear under LDAP -> Conflicts
- when the removed domain matches a Secondary email domain - the secondary email address is removed from the primary user, as long as Email Security still manages the primary domain
- LDAP attributes - these attributes sync to Email Security: mail, proxyAddresses, member, givenName, sn (Surname), homePhone, mobile, company, department, and notes
Enabling / Disabling of LDAP sync
Take note of the following points when enabling or disabling LDAP sync. The information in this section assumes the synchronization rules (above) are met.
- Single LDAP source - at this time, LDAP sync supports connecting to just one LDAP source
- Enable for new Email Security account - set up LDAP sync connection and use the Sync Now action to quickly add users
-
Enable for existing Email Security account - upon for the first sync event; Email Security will
- Add users - LDAP users that are not found in Email Security will be added
- Update users - user metadata from LDAP will be added to existing users. Qualifying secondary email addresses will be added.
- Delete users -Unless managed manually or by SMTP, Email Security users that are not found in LDAP are flagged for deletion and will be listed under LDAP -> Conflicts
-
Disable LDAP sync - users will stay in Email Security, and you must now manage manually
- User conflicts - no further action will occur for users identified as conflicts at the time of disabling LDAP sync. However, users flagged for deletion will be automatically deleted when the delay interval expires.
Synchronization frequency
The Email Security Administrator controls the frequency at which the LDAP process runs.
- Frequency - Email Security polls LDAP for changes as frequently as every 6, 12, or 24 hours; every three days, or weekly
- Adjusting frequency - polling interval is adjusted through the Poll LDAP Every setting that is located on the Connect tab under Service Settings -> LDAP
- On-demand synchronization - use the Sync Now action to force immediate sync from LDAP to Email Security. This is especially useful when there is an urgent need to add or remove a user.
User Deletion
- Users deleted from LDAP - upon the next sync polling event, newly deleted users will be flagged for deletion in Email Security
- Users disabled in LDAP - are flagged for deletion in Email Security
- Deletion delay interval - LDAP connection setting Delete Users After controls the delay interval, which can be set to 7, 14, or 30 days; or never
-
Physical deletion- users deleted from LDAP are delayed by a minimum of 7 days before Email Security automatically deletes them
- Accidental deletion - the delay interval protects against unintentional removal, or temporary disablement, of accounts that sync over from LDAP
-
When a user is flagged for deletion
- User access disabled - during the delayed deletion interval, users registered for deletion can no longer access Email Security
- User-level rules - user-specific Email Security rules, such as Allow & Deny, are retained during the delete delay interval. Once the user is automatically deleted when the interval expires, the related user rules are deleted.
- User's Archived emails - for a user that is automatically deleted after the delete interval and later activated in LDAP, they will be automatically synced to Email Security. At that time, the user's email archive will be restored.
- Immediate deletion - during the delete delay interval, a user can be manually deleted from Email Security through the User Conflicts tab within the LDAP section of Service Settings
- Ignore deletion - users deleted from LDAP can be retained in Email Security by using the Ignore action (User Conflicts tab) during the deletion delay interval
- Manual deletion - A user that is manually deleted in Email Security will be added back upon the next sync event with LDAP. The user must be deleted from LDAP for them to be permanently deleted in Email Security.
How to enable LDAP sync for user management
LDAP discovery allows VIPRE to scan your network directory for users and automatically add them to the user list.
Step 1. Prerequisite - Firewall permissions for LDAP
To use LDAP sync, you will need to ensure your firewall permits access from the Email Security data centers to your LDAP server.
- Open one of these LDAP ports, based on your use of SSL (recommended) or non-SSL
- SSL: 636
- Non-SSL: 389
- Permit these server IP addresses
Email Security Data Center Network Ranges
192.162.216.0/22 (192.162.216.0-192.162.219.255)
208.70.128.0/21 (208.70.128.0-208.70.135.255)
72.35.12.0/24 (72.35.12.0 - 72.35.12.255)
72.35.23.0/24 (72.35.23.0 - 72.35.23.255)
Step 2. Set up the LDAP connection
- Login to https://email.myvipre.com/ using your Administrator credentials
If you have multiple accounts to administer, you will be presented with your list of accounts.
- From the Administrator Dashboard, expand the Customers menu, then select Customer List
- From the displayed Customer List, select the Customer to which you are adding users
- From the customer dashboard, expand the Service Settings menu. Then, select LDAP
- On the Connect tab of the LDAP Configuration screen, click the Enable LDAP box
- In the Host field, enter the IP address of the LDAP server
- Ensure the SSL option is selected (highly recommended). Deselect if your environment does not support SSL.
- In the Username and Password fields, enter the user account credentials to be used for the sync process
- Enter the Base DN (Domain Name) information using standard LDAP notation, e.g.; ou=myOU,dc=example,dc=com
- In the Poll LDAP Every drop-down, select the frequency at which you would like the sync process to run
- In the Delete Users After drop-down, select the number of days for the deletion delay interval
- Click Show advanced options to specify the LDAP port (if not using the default 389/636)
- Click Test to verify the connection settings
- Click Save to store the configuration changes
If the connection test has failed, double-check the setting provided, revise as necessary and test again
Step 3. Add users
- To immediately discover and add users, select Sync Now. Otherwise, users will sync at the next polling cycle.
The initial sync may take up to an hour, depending on the number of users to be created.
Important Information
Sync: Disabled/deactivated users and public folders are not synced by default in LDAP. Enable the checkboxes to sync disabled/deactivated users and/or public folders.
Custom Filter: Filters are applied to user and group syncs; LDAP search filters are supported
How to disable LDAP Sync
Email Security retains all users when LDAP Sync is disabled. If any users are flagged for deletion, they will still be deleted at the expiration of the deletion delay interval.
Disable LDAP sync
- Login to https://email.myvipre.com/ using your Administrator credentials
If you have multiple accounts to administer, you will be presented with your list of accounts.
- From the Administrator Dashboard, expand the Customers menu, then select Customer List
- From the displayed Customer List, select the Customer to which you are adding users
- From the customer dashboard, expand the Service Settings menu. Then, select LDAP
- On the Connect tab of the LDAP Configuration screen, uncheck the Enable LDAP box
- Click Save to store the configuration changes
LDAP sync is now disabled.
Managing LDAP in Email Cloud
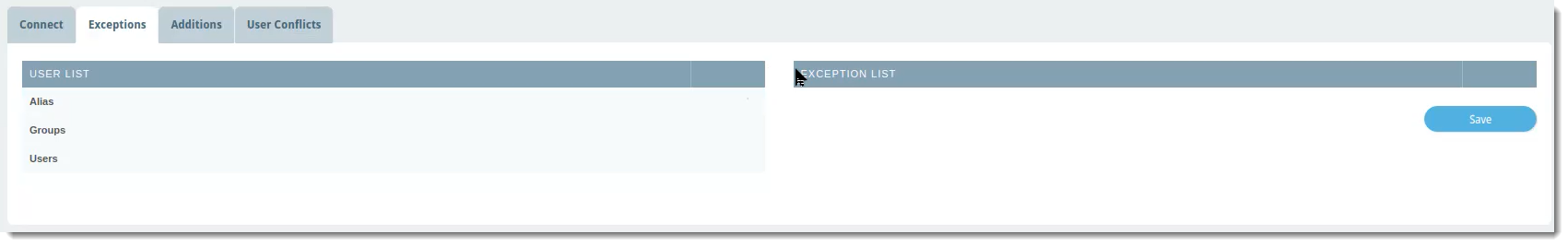
Exceptions
The Exceptions tab is where you can select any name from the User List that you want to exclude from the LDAP sync with VIPRE Email Cloud. This means any exceptions will also be excluded from any custom filters you set up on the Connect tab.
 VIPRE Email Security Cloud - LDAP Sync Exceptions
VIPRE Email Security Cloud - LDAP Sync Exceptions
To exclude a user, group, or alias from the LDAP sync:
- In the User List column, which shows a complete view of your directory server, locate the row with the name of the user, group, or alias you want to exclude
- Click the blue arrow in the same row as the name to add that name to the Exception List
- Click Save
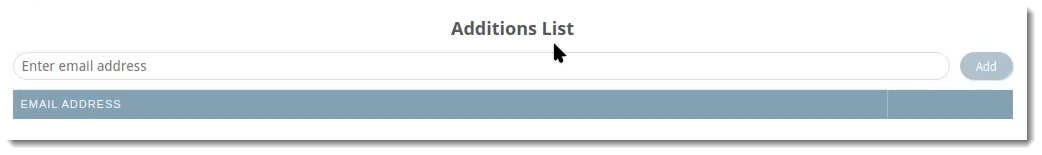
Additions
The Additions tab allows you to manually add users to include in the LDAP sync. For example, this would be useful for adding any new employees that may need to be added in between syncs.
 VIPRE Email Security Cloud - LDAP Sync Additions
VIPRE Email Security Cloud - LDAP Sync AdditionsTo include an additional user to your LDAP sync:
- Type the email address of the user you want to include
- Click Add
Users added to your LDAP sync via this method will be listed on this tab. They will also show up in the list under Users in the left-side menu with the source as LDAP.
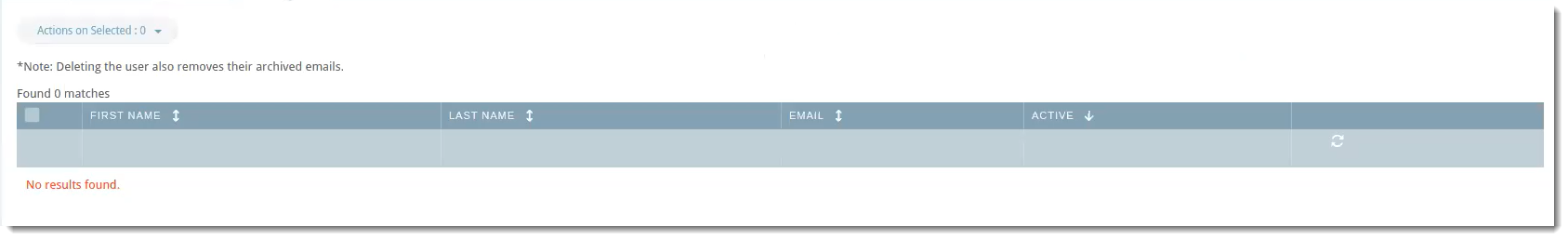
User Conflicts
The User Conflicts tab will show users that previously synced in the portal but are no longer in the directory server.
 VIPRE Email Security Cloud - LDAP Sync User Conflicts
VIPRE Email Security Cloud - LDAP Sync User Conflicts
Example Use-Case
You notice there are two users showing in User Conflicts. Let's say that when you were first setting up LDAP sync, under the Connect tab, you set Delete Users After to 7 days. You're fine with one of the users being deleted because the employee no longer works for your company. The other user, however, is on maternity leave and will be coming back in 12 weeks.
- Click the checkbox next to the user and select your desired action.
In the example above, you could use Ignore so that the user will not be deleted after 7 days.
Troubleshooting
Firewall settings - Verify the Email Security IP addresses have been allowed through the network and domain controller firewall. Verify that your Directory Service is reachable through your firewall.
Account credentials - Confirm the correct user account credentials for Username and Password have been provided and are accurate.
Connection successful but users not populating
When the sync process runs, users will begin to appear in the Users view of the Admin portal. Follow the suggestions below if you do not see the users populating in this view as the sync process runs. After allowing up to 30 minutes for the initial sync process to complete, if many users are missing, then please reach out to our Support team for assistance.
Sync Now - Click the Sync Now button on the Connect tab of the LDAP Configuration screen. You should receive a notification message indicating the sync process has been started.
Managed domain - Verify domain is a managed domain for this Email Security account. From the Email Admin portal, navigate to Domains. The domain(s) shown here must match the domain of the LDAP users' primary email addresses.