Product release information for VIPRE Endpoint Security Cloud Agent v12.3.8160, released on June 9, 2022.
What's New
This update to the VIPRE Endpoint Server Agent for Windows fixes known issues with the previous version that were causing the following issues:
- Business agents were initiating system reboot when software updates failed
- Firefox opened to a blank page when the VIPRE plugin was enabled
- Microsoft Outlook crashed when the VIPRE, HP Sure Click, and/or Mimecast add-ins were enabled
- VIPRE plugin was crashing Microsoft Outlook when Litera plugin was enabled
You can find additional details below under Bugs Fixed in this Version.
Special Instructions
Click here to manage Agent Software Updates
Manage Agent Software Updates
VIPRE Cloud provides flexibility over the deployment of agent software updates, w...
VIPRE Endpoint Security provides flexible control over how agent software updates are delivered to your environment via the VIPRE Cloud web console. You can choose a fully automated hands-off approach, a gated manual approval process, or a hybrid of both.
What are agent software updates?
Agent software updates are packages pushed to each of your endpoint devices. These updates can range from minor patches to full version releases with new functionality. VIPRE Security releases agent software updates as needed, from every few months to a few times a year.
Software Updates vs Definitions
Definitions are used by the VIPRE Cloud agent to identify and remediate malware and are automatically updated multiple times per day, whereas software updates are updates to the agent software and can be gated by VIPRE Cloud before being pushed to your endpoint devices. This gated process gives you the ability to review the available update first, and either a) immediately approve for production, or b) try in a test environment first and then approve for production.
Production vs Test Environments
We understand that administrators often prefer to test software updates in a secluded environment before deploying the changes to their production devices. The VIPRE Cloud agent software update process is built around this potential need for a test environment vs. a production environment.
The Update Process
Scenario: VIPRE Cloud Agent version 1.2 currently exists on your production devices, but as the VIPRE Cloud Administrator, you've received an email notification that an update to VIPRE Cloud Agent version 2.1 has been released.
At this point, you have two options: deploy it to your test environment or skip the test process and deploy to your production environment.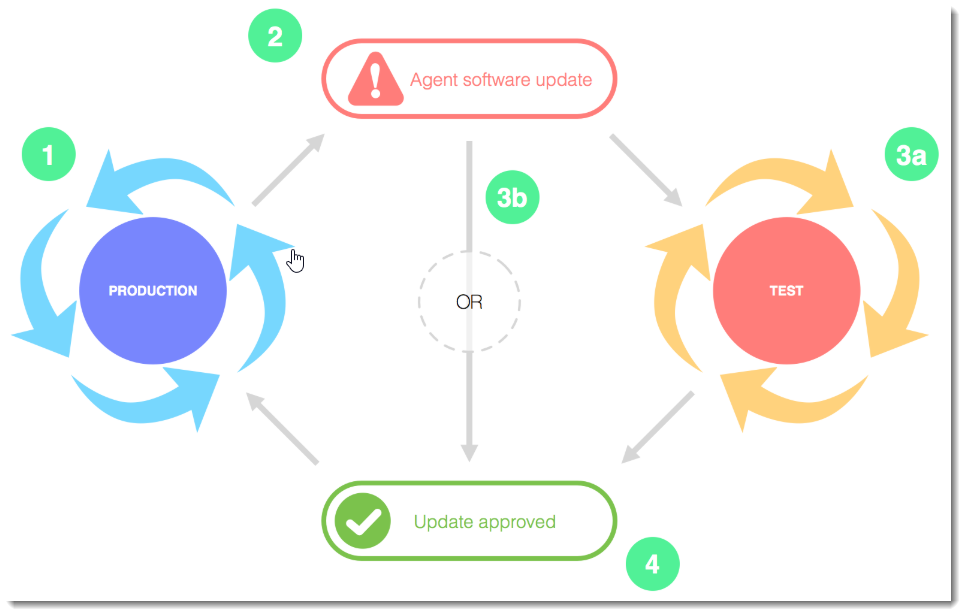
VIPRE Recommends
Use policies to separate your production devices from your test devices. By creating a specific "Test Policy" for a small group of non-critical devices (e.g., IT workstations or a test server), you can safely deploy new agent versions to this group without affecting your broader network.
How Updated Agent Software Gets to Endpoints
The agent update consists of two parts: Approval and Deployment.
Part 1: Approval
Admins choose whether to manually approve the new software or auto-approve it for use in production via VIPRE Cloud's Update Agent settings.
- Notify (aka Manual Approval): VIPRE Cloud displays a notification on the SETUP > Deploy Agents page each time an agent software update is available; before any devices can receive the updated agent software, you must click Approve Version in the console
 |

|
- Auto Approve: VIPRE Cloud automatically approves the new agent version as soon as it is released; depending on how you've configured your policies, the updated software could then be automatically deployed on your devices
To configure your Update Agent settings:
- From within the VIPRE Cloud web console, navigate to SETUP > System > Settings
- Scroll down to Update Agent, then select Auto approve or Notify
- Click Update Settings in the top right corner

Part 2: Deployment
Admins can configure whether to enable automatic installation of the updated VIPRE Cloud Agent on endpoints via policy settings, located in MANAGE > Policies > [Your Policy Name] > Agent > Updates & Communication.

- When Software Updates is selected, devices in this policy will automatically download and install the update as soon as it is approved
- If not selected, devices in this policy will not receive updated agent software until manually updated
Setting the Right Amount of Control
There are two sets of options that work together to control the amount of automation used to deploy agent software updates.
- The option Auto approve or Notify first (manual approval) is set in System > Settings > Update Agent.
- The option to control the deployment of automatic updates to all, some, or none of your agents is set in Policy > Agent > Updates & Communication.
| Goal | System Setting - Update Agent | Policy Setting - Automatically update VIPRE agent software |
|---|---|---|
| Fully automated: New agent software is approved and deployed to all devices immediately upon release | Auto Approve | Enabled |
| Gated: Nothing happens until you click "Approve Version" in the console; once you do, all devices update immediately | Notify | Enabled |
|
Full manual control: Nothing happens until you click "Approve Version" and devices won't update until you either:
|
Notify | Disabled |
| Staged: New agent version is approved and ready for use, but devices in this policy will remain on their current agent version until you manually install the updated agent | Auto Approve | Disabled |
Troubleshooting & FAQ
Troubleshooting the most common issues typically starts with verifying that you are using the latest version of the VIPRE Cloud Agent on your endpoints.
Verify Agent Version
From within the VIPRE Cloud web console, you can check the Agent column in the Devices list

Review the Latest Release Notes
When updating the VIPRE Cloud Agent, always review the most recent release notes. If you encounter unexpected behavior, such as missing features or performance issues, the release notes provide critical information on Known Issues and Workarounds, as well as any Special Instructions for manual actions, such as enabling a new feature within a policy, to ensure the agent functions as intended.
I've approved the updated VIPRE Cloud Agent version. Why are my devices are still showing the older version?
Check the policy those devices are assigned to to ensure Automatically update VIPRE agent software is enabled. If it is not enabled, and you want your devices to automatically install updated agent software, enable this setting.
If it is enabled, check the device status by ensuring your endpoints have an active heartbeat with the console to receive the update command promptly by going to MANAGE > Devices
Example:
| This screenshot shows an endpoint that hasn’t been seen in approximately one week and is running the previous version of the Linux agent. This endpoint likely is not online and would not be able to receive the Update Devices command. |  |
| This screenshot shows an endpoint with an active heartbeat and is running the previous version of the Linux agent. This endpoint should be able to receive the Update Devices command. |  |
| This screenshot shows an endpoint with an active heartbeat and the updated version of the Linux agent. |  |
System Requirements
This section contains all of the system requirements for VIPRE Endpoint Security Cloud.
| Product or Component | Minimum Requirement |
|---|---|
Web-Based Console |
We support the latest release of the following browsers:
|
VIPRE Update Proxy |
VIPRE Update Proxy is a supplemental application tool that works with your existing deployment of VIPRE Endpoint Security - Cloud Edition. For more information, refer to Related Articles for details on the VIPRE Update Proxy Guide. |
VIPRE Agent for Windows |
OPERATING SYSTEMS
HARDWARE
MISCELLANEOUS
SUPPORTED EMAIL APPLICATIONS
SUPPORTED WEB BROWSERS FOR HTTPS URL PROTECTION
|
Bugs Fixed in this Release
- VPBAGENT-8642: VIPRE Agent unable to download VIPRE definition updates
- VPBAGENT-8613: VIPRE Agent was prompting to reboot after attempt to uninstall legacy version of Device Control fails
- VPBAGENT-8632: VIPRE Agent was prompting to reboot after failed attempt to update software via Patch Management
- VPBAGENT-8681: Mozilla Firefox was opening to a blank page when the VIPRE plugin was enabled
- VPBAGENT-8713: VIPRE Agents being upgraded manually were not updating to the latest definitions after upgrading from v11.0 or v12.0
- VPBAGENT-8706: Microsoft Outlook was randomly crashing when using the "Send to Mail Recipient" feature in Microsoft Windows explorer