What are devices to VIPRE Cloud? A device, also known as an endpoint, is protected and managed by VIPRE. Examine the monitoring views and actions available for devices.
Devices and how they relate to agents
Devices, or endpoints, are protected by VIPRE with agent software. When first implementing VIPRE in your environment, the VIPRE agent software needs to be deployed to each of your devices in order to protect them.
Throughout VIPRE Cloud, devices refers to your endpoints and their health; agents refers to the VIPRE software on your endpoints and the health of that software.
View devices protected by VIPRE
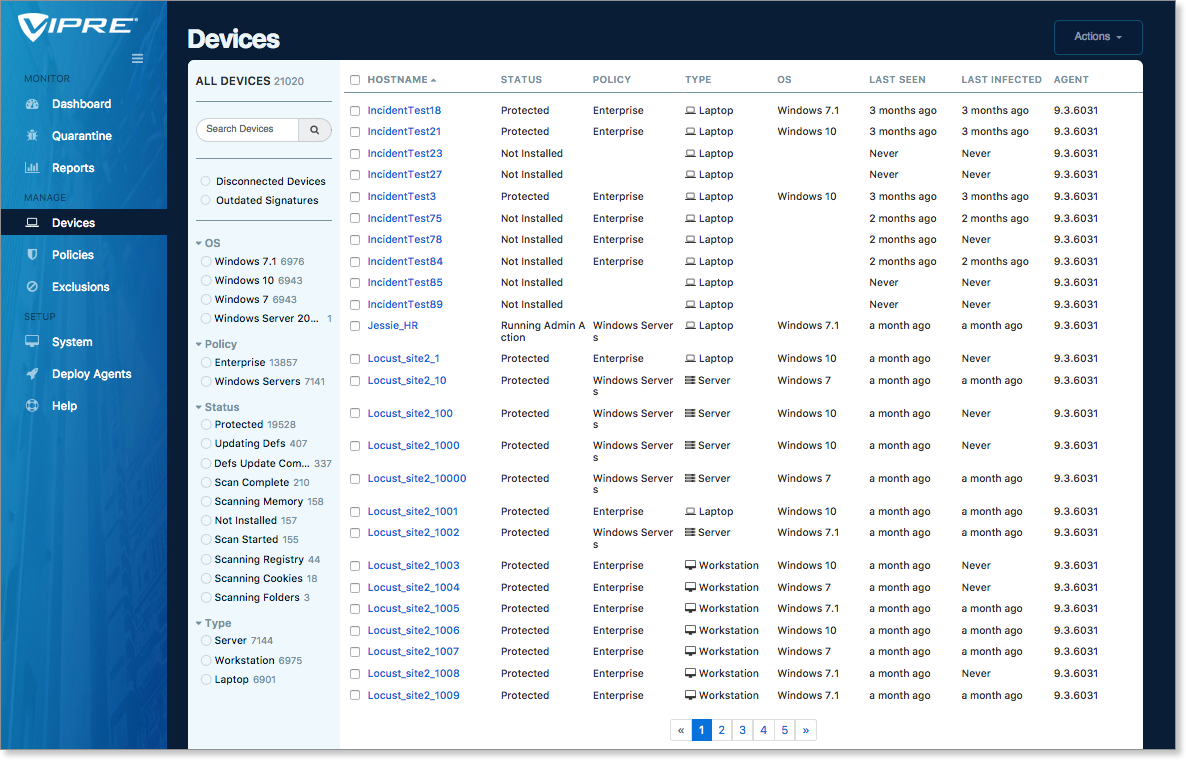
The Devices page shows you an overview of every device that has checked in with VIPRE Cloud. You can quickly scan the columns to learn many details on the behavior of your devices.
You can see the device name, whether it is protected, which policy is applied to it, what type of device it is, the Operating System version, etc.
Filtering devices
Because you can potentially have hundreds (or thousands) of devices on your site, it is often necessary to filter the list to limit the visible information. You can select filters to focus your view, and very quickly find devices that need action, are outdated, are disconnected, or have some other problem.
Exploring device details
Once you have located a device you'd like more information on, simply click the name of the device to drill down into it. From here, you're taken to the device details, shown on the Summary tab.
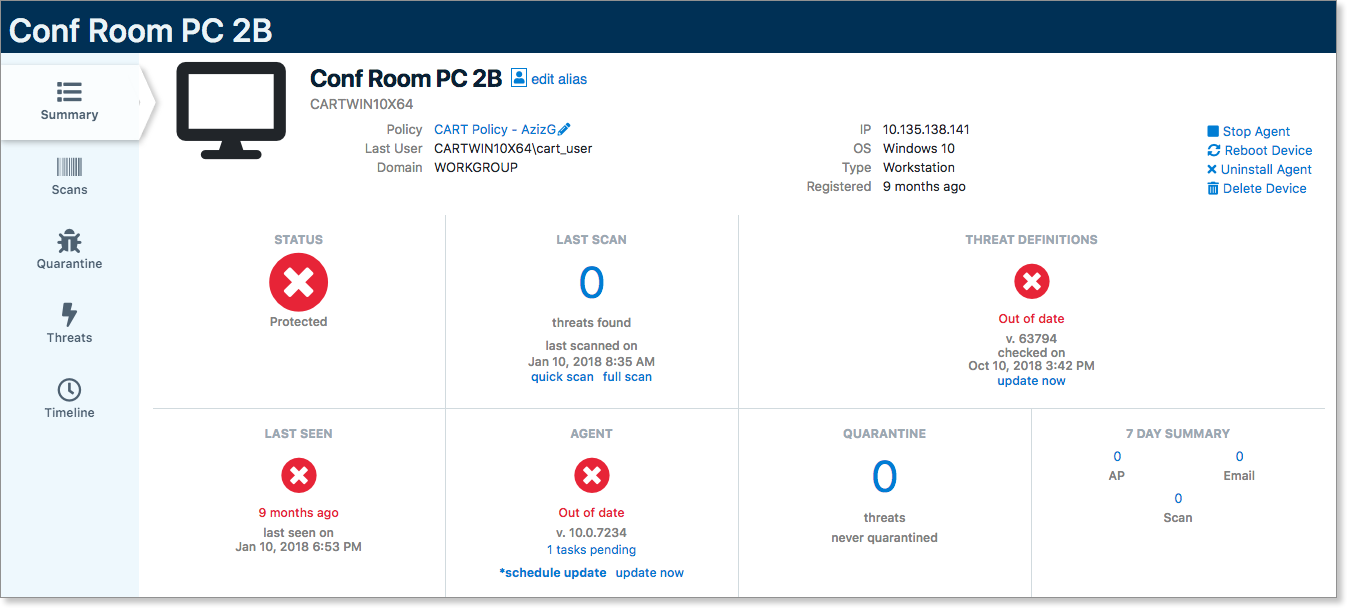
The device's summary screen is like a mini-dashboard for the selected device. The STATUS section in the top left shows an immediate all-in-one status of the device. Is it good to go, or does it need looking into?
The other sections of this screen provide further key information: Scan time, threat definitions, last time the device checked in, agent software version – all the top items you'll want to check when determining at a high level if a device is in performing properly.
Along the top, you have some network and admin-level items: Domain, IP address, OS. The quick-action links in the top right give you single-click common actions to perform on that device: Stop the agent, reboot the device, or uninstall the agent.
The tabs on the left show even more information for each category: Latest scan details, items in quarantine on this device, threats found, and a super-useful vertical timeline that shows the history of the device.
From this screen, you can also assign an alias to the device. Refer to Related Articles for more information on using aliases.