VIPRE's firewall is designed to protect your devices by policing incoming and outgoing connections. The firewall can be configured a few different ways to allow applications or block them, with or without notification on the screen. Advanced firewall rules can also be used to further protect your endpoints.
About Firewall Rules
Firewalls are generally a machine's first line of defense against unwanted intrusion, as they can completely block incoming and outgoing connections. Allowing certain connections is of course almost always necessary to use endpoint devices, but specifically restricting a device's network connections helps prevent network-based attacks and to prevent malware from reaching out to get further instruction. By properly configuring firewall settings, you can reduce the chances that a malicious program can access important information.
Firewalls may also be used to prevent people from using applications or visiting websites that the organization either deems as risky or simply does not want them to be using, such as applications for messaging or social media; “shady” websites, or other risk vectors.
The VIPRE firewall is a host-based solution running as part of the VIPRE agent software that protects each endpoint device. By making policy changes within the VIPRE Cloud console, you define how the firewall protects all agents under the selected policy.
Important
These firewall options do not apply to Mac agents.
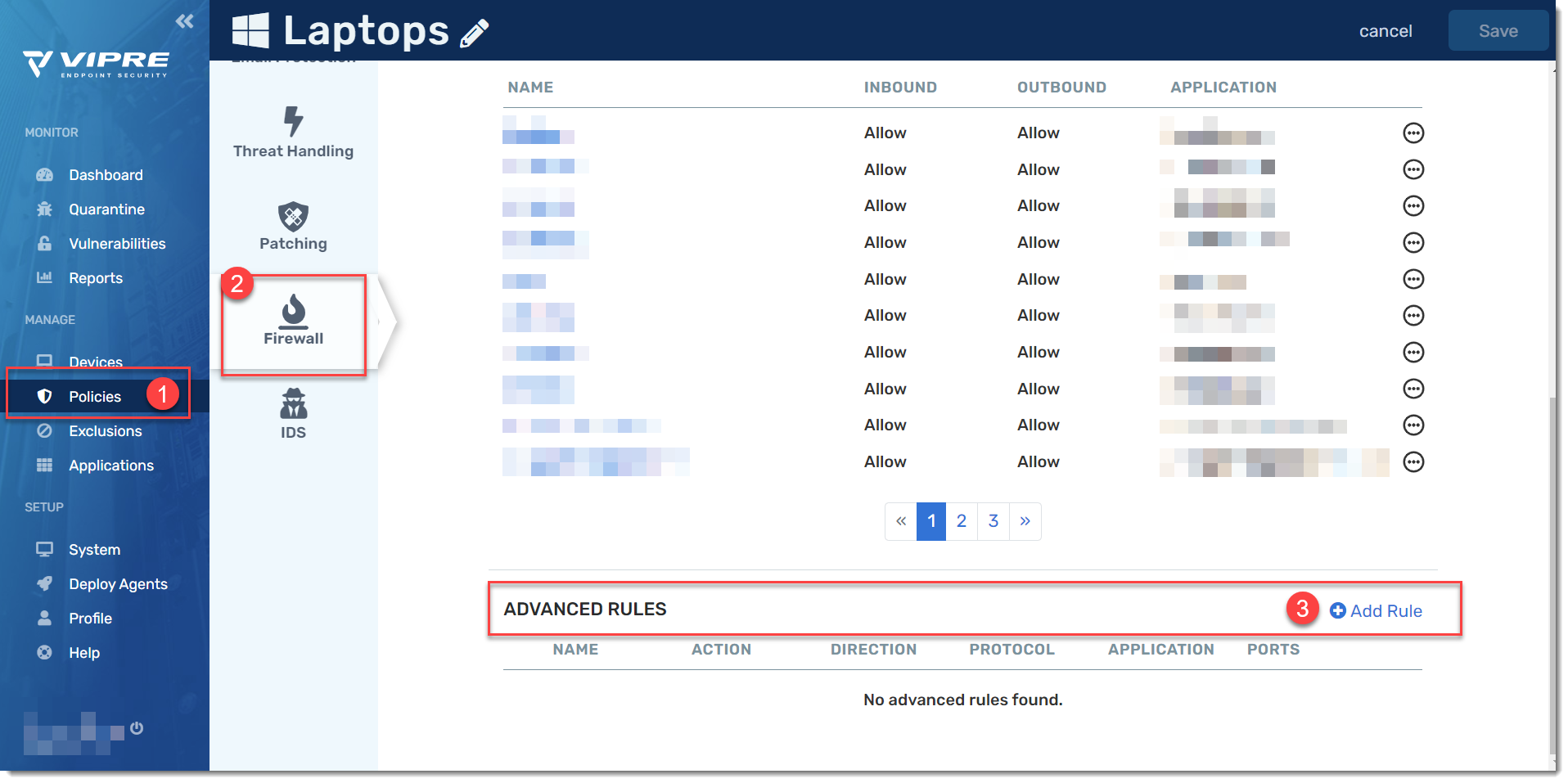
Add an Advanced Firewall Rule
Advanced Firewall rules are intended to provide additional control over an organization's application and network needs. Through advanced rules, the firewall system can be automated to let connections through that are likely to be mundane while stopping any connections that could be malicious in nature.
A firewall rule is comprised of two parts: an action that it takes and the event that it takes that action on.
Note: Once added, an advanced rule will impact all agents belonging to the given policy.
To create an advanced rule
- To view the policy details, select Policies in the Manage category from the left blue navigation menu, then click on the linked policy name
- On the light blue menu, scroll down and select Firewall
- Scroll down to the bottom of the page, under Advanced Rules, select Add Rule
- Customize your Advanced Rule (see below for details)
- Select Save when complete
Select the Action and Direction
Advanced rules begin with setting an action and direction.
Actions are set to either be "allow" or "block," depending on the rule desired. In general, many systems either allow everything by default and then block exclusions, or block everything by default and then allow exclusions. One is a more flexible system, while the other is a better secured one.
The potential actions for the rule are
- Allow. This allows connections through silently. This is designed for systems that the organization knows are safe and relies upon within their infrastructure.
- Allow with notification. This allows connections through but will notify the user on-screen that the connection is being made.
- Block. This automatically blocks connections silently. This is useful for connections that are known to be harmful.
- Block with notification. This will block connections and notify the user with a message on-screen. This is useful for connections of uncertain origin, in which the user may need to be apprised of its status.
Pop-up notifications on the endpoint device
Although you can set any of your advanced rules to notify the end-user on the endpoint device, this should be used very sparingly. When notifications are enabled, VIPRE will pop-up an alert (notify) for the end-user every time the rule is triggered. In a scenario where a machine is being hit with lots of traffic, this could generate a good deal of potential noise for the user.
We, therefore, recommend limiting the use of Block with notification and Allow with notification for uncommon events that should never happen.
Directions are either inbound, outbound, or both. Inbound connections are connections sending information to the agent. Outbound connections are sending information from the agent. It's possible there may be applications you want to receive information from but not send information out to.
Select the application and protocol
For fine-grained control, you are also able to select a specific application and/or a network protocol. This is optional.
Applications can be any application on the endpoint machine. You may want to allow internal company applications commonly used by employees or block applications that are known to be risky.
You can select whether specific applications will be allowed or blocked and whether the agent notifies the user when the firewall takes action. Both inbound and outbound connections can be controlled; as an example, you might block an application from sending any information out but not receiving any information.
When controlling an application, you will need to select the location of the executable on the agent machine.
Protocols include TCP, UDP, ICMP, or IGMP. You may want to block protocols your organization isn't using, to reduce their attack surface.