This release is for the following components of VIPRE Endpoint Security Server released on July 14, 2020:
- Management Console (VSS) version 12.0.2.1
- Server Agent version 12.0.7873
Update to this version of VIPRE Endpoint Server
There are some things to keep in mind when updating the Endpoint Server Console and Agents.
Step 1: Update VIPRE Console
Ensure the VIPRE Console is closed prior to updating.
- Download and run VIPRE Endpoint Security (Key starts with 443)
- Proceed with the installation prompts to complete the update
- If necessary, read up on what is required to update and how to troubleshoot
- Proceed to Step 2: Update the VIPRE Agents
Step 2: Update VIPRE Agents
There are three ways to update agents:
Automatic agent updates
- Open the policy properties
- Navigate to Updates > Software Updates
- Check the box and set the time to how often VIPRE should check for updates
Manual agent updates
- Open the VIPRE Business console and select Windows Policies
- Click on the Protected Computers tab
- Right-click the Agent(s) and select Agent Updates > Check for Agent Software Updates
Scheduled agent updates
- Open the VIPRE Business console and select Windows Policies
- Click on the Protected Computers tab
- Right-click the agent(s) and select Agent Updates > Schedule Agent Upgrade
- Select the time and date you wish to schedule updates for and click OK
What's New
Over the past few years, we've made many significant improvements to our core file- and process-based detection engines in the Windows agent to the point where we are now consistently scoring exceptionally well in independent antivirus (AV) testing (see AV-Comparatives, AV-Test, Virus Bulletin).
The one major subsystem that hasn't gotten as much attention is the network protection stack—firewall, intrusion detection systems (IDS), and web protection—which provides essential security against network-based attacks. The components built into VIPRE Endpoint Security Server v11 do provide reliable protection but are hard to maintain, difficult to extend, and have a few gaps, particularly in monitoring encrypted communications.
This has all changed with VIPRE Endpoint Security Server v12, in which we're introducing a major Update to the network protection stack.
DNS Protection
The most exciting new feature we've added is our brand-new DNS Protection. Built right into the VIPRE agent, this new feature helps prevent your users from ever visiting a known malicious website. This new layer of protection is something many of our customers have historically purchased from third-party DNS providers or as a separate product or add-on, but which we are now including as part of our base offering. Any time your users attempt to look up an internet domain name, VIPRE will perform a comprehensive series of checks leveraging our threat intelligence cloud service to ensure that that remote host is not a known malicious domain. If it is at all suspicious, we'll immediately redirect the user to a block page and tell them that there's an issue: the user's browser will never have a chance to download any content from a potentially malicious webpage.
Firewall Improvements
 The firewall is now faster and more efficient, providing a solid foundation for the other components. The firewall is designed to protect typical endpoints out of the box with just a few clicks to enable blocking but is easily configurable to allow special services if needed in your environment.
The firewall is now faster and more efficient, providing a solid foundation for the other components. The firewall is designed to protect typical endpoints out of the box with just a few clicks to enable blocking but is easily configurable to allow special services if needed in your environment.
Upgraded IDS
An entirely new Intrusion Detection System (IDS) now provides vastly expanded signature-based detection of common network attacks plus increased performance. Now hosting over 8000 (over 15 times more than v11!) individual detection rules, we've greatly expanded our ability to guard against the latest threats.
IDS Automatic Monitoring
The new IDS is also more intelligent and can automatically detect dozens of network protocols to provide deep introspection - no more manually specifying which ports to monitor. It won't matter if a service, or even malware, attempts to hide your users' activities by using custom ports. The new IDS decodes all network traffic, automatically identifies the appropriate protocols and services, and applies the appropriate IDS rules to that traffic.
Malicious URL Blocking

In many cases, blocking an entire site (like GitHub) might cause too much disruption, but there is some page or another resource on that site that delivers undesirable content. To solve this problem, VIPRE also scans entire URLs seen in HTTP traffic to ensure that your users don't hit pages that could get them in trouble. This service leverages our global threat intelligence network for up-to-the-minute information about bad URLs and informs your users if they attempt to click on a bad URL link.
Browser Extensions
 Two new agent-managed browser extensions—for Firefox and Chrome browsers—provide visibility into encrypted HTTPS web traffic and leverages the same URL blocking service mentioned above. The VIPRE agent pushes these into installed browsers automatically if enabled in your policy, and ensures your browsers stay protected.
Two new agent-managed browser extensions—for Firefox and Chrome browsers—provide visibility into encrypted HTTPS web traffic and leverages the same URL blocking service mentioned above. The VIPRE agent pushes these into installed browsers automatically if enabled in your policy, and ensures your browsers stay protected.
Malicious Content Blocking
 New Web Exploit Protection replaces our retired Edge Protection feature to find and block malicious embedded content within web pages. Malicious JavaScript code and other risky content is now scanned for automatically and, if found, results in the page being blocked. Effective against malvertising, watering hole attacks, and spoofed websites, Web Exploit Protection protects your users even if they are visiting a brand-new malicious web page.
New Web Exploit Protection replaces our retired Edge Protection feature to find and block malicious embedded content within web pages. Malicious JavaScript code and other risky content is now scanned for automatically and, if found, results in the page being blocked. Effective against malvertising, watering hole attacks, and spoofed websites, Web Exploit Protection protects your users even if they are visiting a brand-new malicious web page.
System Requirements
Management Console (VSS) |
OPERATING SYSTEMS
Notes: Embedded operating systems are not supported
HARDWARE
MISCELLANEOUS
|
|---|---|
VIPRE Agent for Windows |
OPERATING SYSTEMS
† Supported for legacy agent only, not available for Cloud †† VIPRE Advanced Active Protection is not supported on these Operating Systems
HARDWARE
SUPPORTED WEB BROWSERS FOR HTTPS URL PROTECTION
SUPPORTED EMAIL APPLICATIONS
|
VIPRE Agent for Mac |
OPERATING SYSTEMS
|
VIPRE Business Mobile Security (Agent) |
OPERATING SYSTEMS
|
Changes to Note
IMPORTANT: Change to VIPRE settings
The settings for Malicious URL Blocking have changed with this release.
-
Default enabled- The feature is now enabled, by default.
- VIPRE will block access to malicious web sites and pages in unencrypted (HTTP) and encrypted (HTTPS) traffic. To protect encrypted traffic, VIPRE requires a browser extension in order to see the decrypted content; as of this release, the Mozilla Firefox and Google Chrome browsers are supported.
-
Two settings to disable - To disable, uncheck both Verify HTTPS web browser traffic and Verify HTTP traffic.
- You can also disable HTTPS blocking for a specific browser only, which will uninstall the browser extension from that browser.
- Legacy agents, ports to filter - specifying ports to filter is now only required for legacy agents (prior to version 12.0.xx). The newer agent will auto-detect which ports carry HTTP traffic.
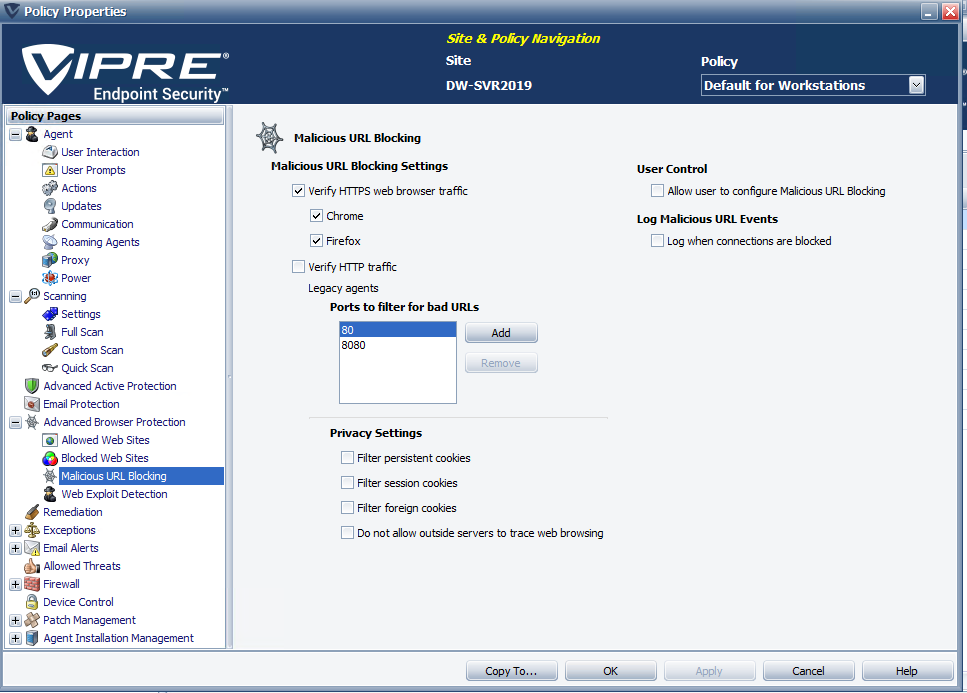
- Port Scans - No longer available in v12. It is still available in Agent v11 and lower, however.
- Web exploit protection restored - We have restored the ability to identify and block malicious web page content based on our new network stack.
- New IDS configuration and ruleset - Two different IDS rulesets are now provided, one for legacy pre-12 agents and new ruleset configuration for v12 agents. The new v12 ruleset now includes more than 5000 IDS rules.
Known Issues and Workarounds
This section lists issues that are known at the time of release. In some cases, these are bugs that we are working to resolve with a subsequent release. Other items may be due to causes outside of our control, such as bugs with other vendors' software. In all cases, we have tried to provide a workaround for you to consider, should you experience an issue.
If you have questions about a specific issue, please provide the issue ID (if applicable) when contacting our Technical Support team.
At this time, there are no new known issues with this release.
Previously Known Issues
Agents running Windows Server 2019 do not reboot when clicking "Reboot Now" on a VIPRE Reboot Required condition [VPBAGENT-3920]
This is a condition that occurs due to changes in Windows Server 2019 security settings.
Endpoint devices running Windows Server 2019 will not reboot when the "Reboot Now" button is selected unless the user account is added to a specific Windows Local Security Policy. The default "Administrators" group cannot restart the Agent using this method.
Workaround 1: Add the user to the "Shut down the system" policy
To add a user account to the "Shut down the system" policy
- On the Agent machine, open the Windows Local Security Policy
- Add the required user account to the "Local Policies" > "User Rights Assignment" > "Shut down the system" policy
- Sign Out and Sign In to the machine (or reboot) for the policy change to apply
The next time VIPRE requires a reboot, the modified user will be able to reboot the machine using the "Reboot Now" button.
Workaround 2: Restart the Agent manually
Instead of using the Reboot Now button, users can manually restart the Agent through the Windows Start menu.
Firewall trusted zones defined with IPv6 address ranges do not work [VBAGENT-3187]
The VIPRE Agent does not recognize IPv6 trusted zone ranges and treats any IPv6 traffic as non-trusted. Therefore, any firewall rules for non-trusted traffic will still apply.
There is no known workaround at this time.
Logging into a Citrix device with Active Protection enabled fails [VBAGENT-275]
This is a known conflict between VIPRE Active Protection and Citrix User Profile Management (UPM). Attempting to login to a Citrix device with both services enabled causes the login to hang and eventually fail.
Workaround: Temporarily disable Active Protection for Agents that need to access Citrix devices.
Microsoft Windows Defender continues to run even if policy has Disable selected
For policies applying to machines running Windows Server 2016 or higher, selecting "Disable Windows Defender" does not actually disable Windows Defender.
Workaround: You may manually disable Windows Defender on these machines. Refer to these articles for more information:
- Disabling Windows Defender Antivirus on Windows Server 2016
- Microsoft TechNet article: Windows Defender Overview for Windows Server
VIPRE Business or VIPRE Business Premium agents on version 9.3 or earlier that are scheduled to Upgrade to VIPRE Endpoint Security will not fully Upgrade on the initial install
VIPRE has added multiple driver updates that are included with this release. Depending on the version of the drivers on your system and which features are enabled in your policies (e.g. Device Control), installation may require two or more reboots to complete the agent Upgrade.
Workaround: Make sure any required reboots are completed. For the corresponding agent, check the Console > Agent Details > Agent Environment tab and verify the "Needs Reboot" column is not marked with an "X".
Color coding of agent version in console does not appear to be consistent for all out of date agents.
In the Protected Computers tab of the console, the agent version field is shaded orange for those agents that need to be updated to the latest agent software version. However, some agents that appear to be out-of-date are not shaded. Those agents include VIPRE Business or VIPRE Business Premium agents that do not have the highest build available. Agents that are not actively communicating are also not shaded but may be out of date.
Workaround: The agents will Update with the correct status upon the next communication.
You may note VIPRE Business or VIPRE Business Premium agents reporting incorrectly. We recommend these agents be upgraded to VIPRE Endpoint Security to match your VIPRE Endpoint Security 11 console. This will give you our best protection for these devices and correct the reporting issue.
If you are not currently licensed for VIPRE Endpoint Security, please contact your sales representative (+1 855-885-5566 or Contact Sales) for more information on how you can Upgrade.
When changing Active Protection settings within a VM environment, the changes take up to 15 minutes to apply
This is normal, as communication between the Console > VM takes some time to propagate.
When VIPRE scans an email archive, files are not quarantined properly
Workaround: Through your email client, perform a manual cleanup of the email archive containing the infected email. Once the infected email has been removed, re-scan the endpoint to confirm removal.
When managing over 500 agents, a full SQL database should be implemented
It is recommended that when managing over 500 agents, a full SQL database (versus SQLite) will provide the best performance.
See the following support article: Recommended SQL Server settings for a VIPRE Business Database
VIPRE Endpoint Security agents cannot run on Windows XP or Windows Server 2003
The software limitations of these older platforms do not provide the resources necessary for some more robust agent features. VIPRE Endpoint Security requires a minimum OS version of Windows Vista or Windows Server 2008.
Attempting to launch more than one instance of the administration Console (via terminal services) causes agent > Console communication to fail
This is a product design safeguard that prevents one administrator from overwriting a different administrator's settings without notification. Only one instance of the admin Console should be running at a time.
Push agent installations do not work if Simple File Sharing is enabled
Simple File Sharing prevents installation through the push option. You must manually create the MSI installer package and deploy the installer to the workstation.
See the following support article: Minimum Requirements for Agent Push Deployment
Without proper firewall configuration, agents are unable to contact the Console
An incorrectly configured firewall can prevent communication between the agent and the Console.
See the following support article: Minimum Requirements for Agent Push Deployment
Device Control policy changes may require an agent restart before they take effect
On Consoles upgraded to 9.6 or earlier, policy changes will not be applied until the agent is restarted.
Workaround: Manually restart the agent to apply policy changes.
To manually restart an agent
- Right-click on the agent in the grid
- Select Issue Remote Restart Command
The Database Migration Utility may crash if the SQL Database has any spaces in the database name
The Database Migration Utility for VIPRE 9.6 or earlier may crash during the migration process if your SQL Database has spaces in the name of the database.
Workaround: Resolution is under development. When created, database names should contain no spaces, no symbols, and no carriage returns.
Anti-Phishing does not work if Outlook is open during agent install
If Outlook is running when enabling Anti-Phishing in the VIPRE Console before pushing an agent installation, it will not function properly until Outlook is restarted.
Workaround 1: Shut down Outlook during agent installation when enabling Anti-Phishing
Workaround 2: Restart Outlook after agent install when enabling Anti-Phishing
Outdated Citrix drivers may cause BSOD on Windows 7 agents
Updating a Windows 7 agent to VIPRE Endpoint Security 9.6 or earlier can cause a blue screen state on systems with older versions of Citrix drivers on them.
Workaround: Updating the Citrix driver should resolve the issue.
On some systems, Windows Defender's Smart Screen blocks the agent installer
Select More Info from the Windows Defender popup and then select Run Anyway.
Bug Fixes
The following bugs have been resolved with this release.
Console
- VIPREBIS-6532 - Upgrades from Business Antivirus or Business Premium incorrectly have Device Control enabled in all policies
-
VIPREBIS-6754 - Upgrade script does not add new field (ISOLATED) to agent table
- VIPREBIS-6755, VIPREBIS-6782 - Inconsistent times are shown on Agent versus Console; some are UTC time
- VIPREBIS-6756 - Audit Trail may display no data in version 11 after upgrading from an older version of VIPRE
- VIPREBIS-6757, VIPREBIS-6633 - In some cases, the Threat and Health Summary Reports do not display correct data
- VIPREBIS-6766 - Custom reboot text is not displayed when issuing a remote reboot
- VIPREBIS-6856 - Supplemental software packages may display multiple device control versions after releasing a new version
- VIPREBIS-6878 - User administration is not working resolved with documentation Update
- VIPREBIS-6198 - Social picture links on weekly health summary do not do anything
- VIPREBIS-6110 - (Rebrand) VIPRE Business to show VIPRE Security instead of ThreatTrack Security
- VIPREBIS-1371 - Agent Quarantine tab > Send File for Analysis not creating toast notification
- VIPREBIS-4797 - Scan duration in the Scan History - Preview should be in format hh:mm:ss
Agent
- VPBAGENT-3306 - Device Control authorization code stops working over time
- VPBAGENT-4004 - Device Control does not correctly identify all device types
- VPBAGENT-4136 - Google Earth Pro patch breaks Google Earth
- VPBAGENT-4137 - Device Control is breaking the encrypted keyboard driver included with IBERIABANK TreasuryConnect Secure Browser
- VPBAGENT-4330 - Unprotected Popup after Update to 11.0.7627
- VPBAGENT-4486 - Incorrect identification of machine type for some systems
- VPBAGENT-4554, VPBAGENT-4810 - MSI repair breaks communication with VSS or VIPRE Cloud
- VPBAGENT-4576 - BSOD using Arcserve with agent 11.0.7628
- VPBAGENT-4644 - Computers are not booting after install of VIPRE
- VPBAGENT-4667 - Agents converting to the consumer version
- VPBAGENT-4810 - Agent sending hello call to Localhost after migration to Endpoint Cloud
- VPBAGENT-4838 - Logoff is slower on Windows 7 with Advanced Active Protection enabled
- VPBAGENT-4853 - Percent (%) Scan Complete is reported incorrectly
- VPBAGENT-4856 - Agent does not check for definition updates on startup
- VPBAGENT-5221 - BSOD may occur when Agent upgrades from 10.1.7631 VPE to 12.0.7795 VES
- VPBAGENT-5387 - Deep scans are not completing
-
VPBAGENT-5393 - Agent GUI displays inconsistent data for last defs Update
- VPBAGENT-5406 - Browser protection may interfere with some sites
- VPBAGENT-5596 - Agents may stop downloading definitions after a period of time
- VPBAGENT-6235 - Loss of connectivity and intermittent network issues on some server OS's
- VPBAGENT-6237 - Issues with network protection resiliency: Under certain conditions, such as networks with large amounts of non-TCP/UDP traffic, specific queues within the VIPRE network filter driver could overflow and cause excessive network latency - sometimes causing other network connections to fail.
- VPBAGENT-6243 - Unable to connect to Exchange server: Outlook and Exchange configured with RPC over HTTP or MAPI over HTTP may experience failed connections when malicious content scanning is turned on
- VPBAGENT-6249 - URL whitelist not honored: Under certain conditions, URL whitelist entries were not being honored by the URL and Content Filtering features
- VPBAGENT-6265 - BSOD when streaming multiple videos; heavy video streaming load may cause a crash in the network filter driver
- VPBAGENT-6335 - Play Store Help and Support URLs incorrect for browser extensions
- VPBAGENT-6350 - Agent locking access to ag-grid.com
- VPBAGENT-6351 - Internet connection may freeze when OpenVPN is run in full tunnel
- VBAGENT-6383 - idsrules2.def is not being copied & updated through incremental definitions updates