Vulnerabilities, in this case, refer to a list of publicly known security flaws called CVE (Common Vulnerabilities and Exposures) identifiers. This list shows you the severity of the vulnerability and which applications are affected by that vulnerability, among other bits of helpful information.
On the left-side panel, under Investigate, select Vulnerabilities
- You'll be presented with a list of CVE ID numbers organized in a sortable table; there are three views available on this screen: Ungrouped, Grouped by ID, and Grouped by Device
Ungrouped
At the top of the Ungrouped view, clicking on the number of days in the top left will allow you to choose a date range from as recently as the last 24 hours up until the last 180 days. Based on the date range chosen, the graph will show you how many vulnerabilities have come up or been closed per month. The Open Vulnerabilities table also updates based on the date range.
Information in the Ungrouped view can be exported as a CVS file by clicking the Export CSV button in the top right corner.
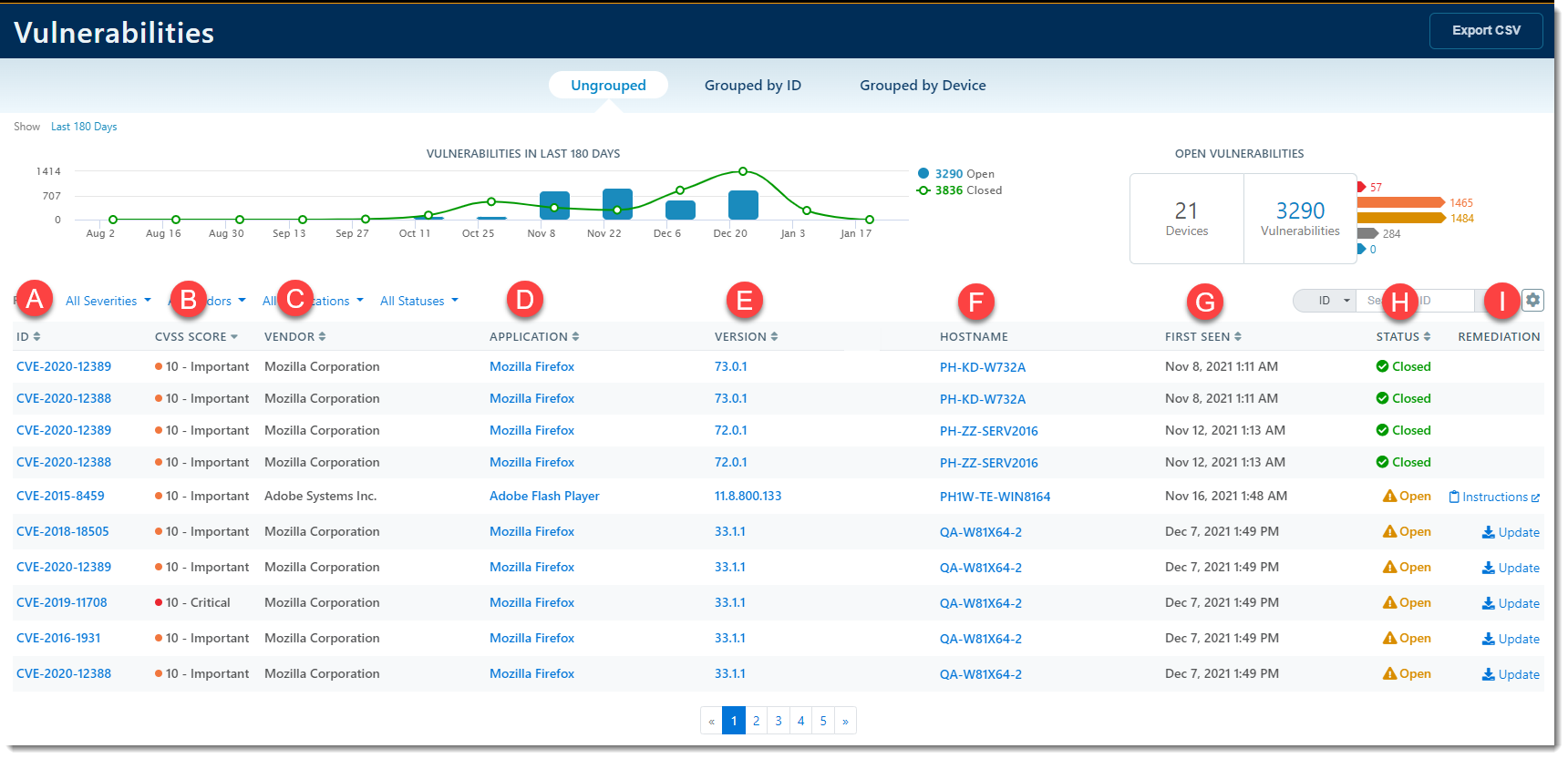
A - ID
CVE Identifiers, assigned by a CVE Numbering Authority (CNA); these are industry-standard identifiers and searchable on any search engine.
Clicking on a CVE ID will bring you to the details of that particular vulnerability. There are three views on the Vulnerability Details screen.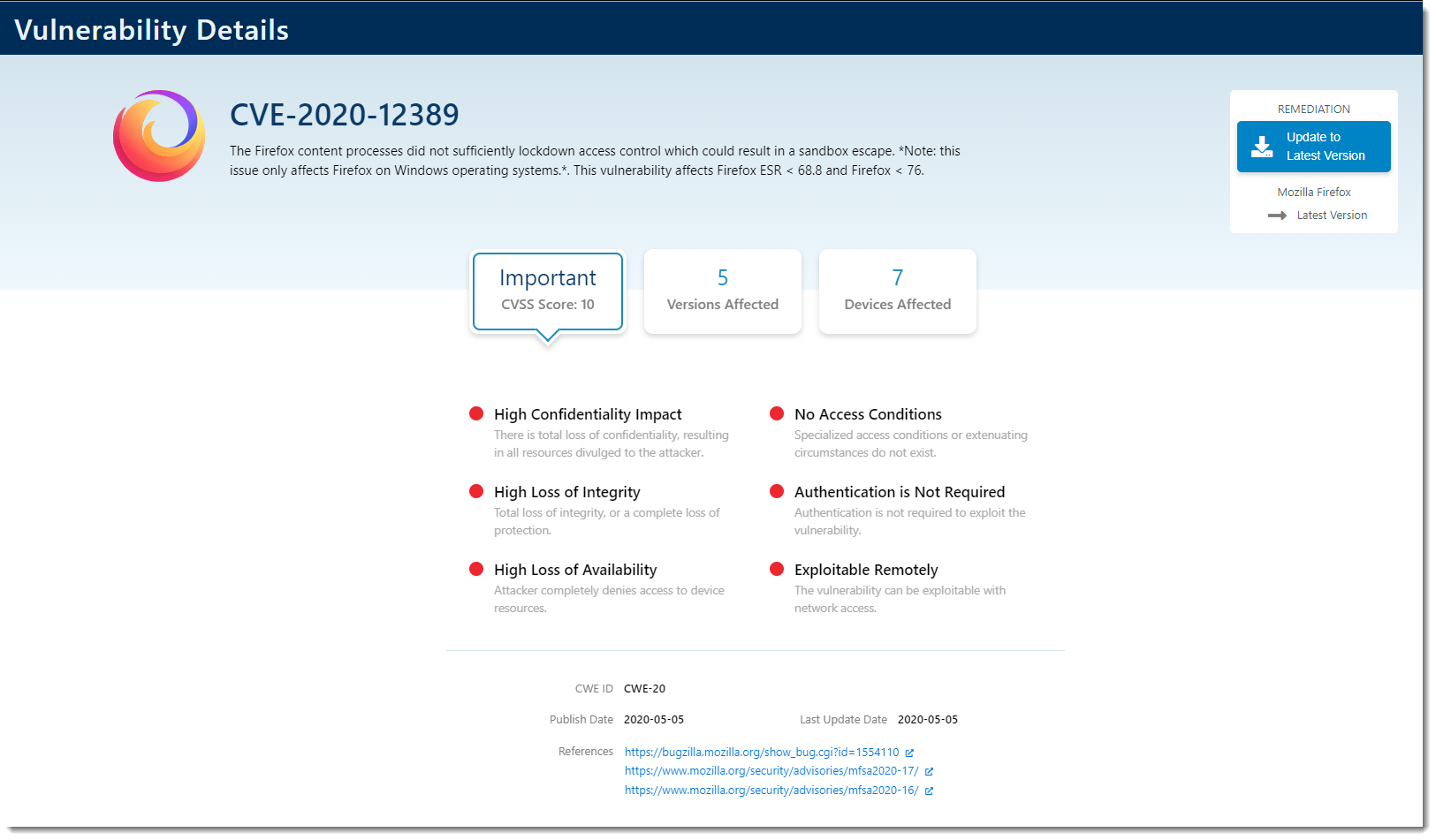 View 1: CVSS Score - This view shows you the reasons for the assigned CVSS Score.
View 1: CVSS Score - This view shows you the reasons for the assigned CVSS Score.
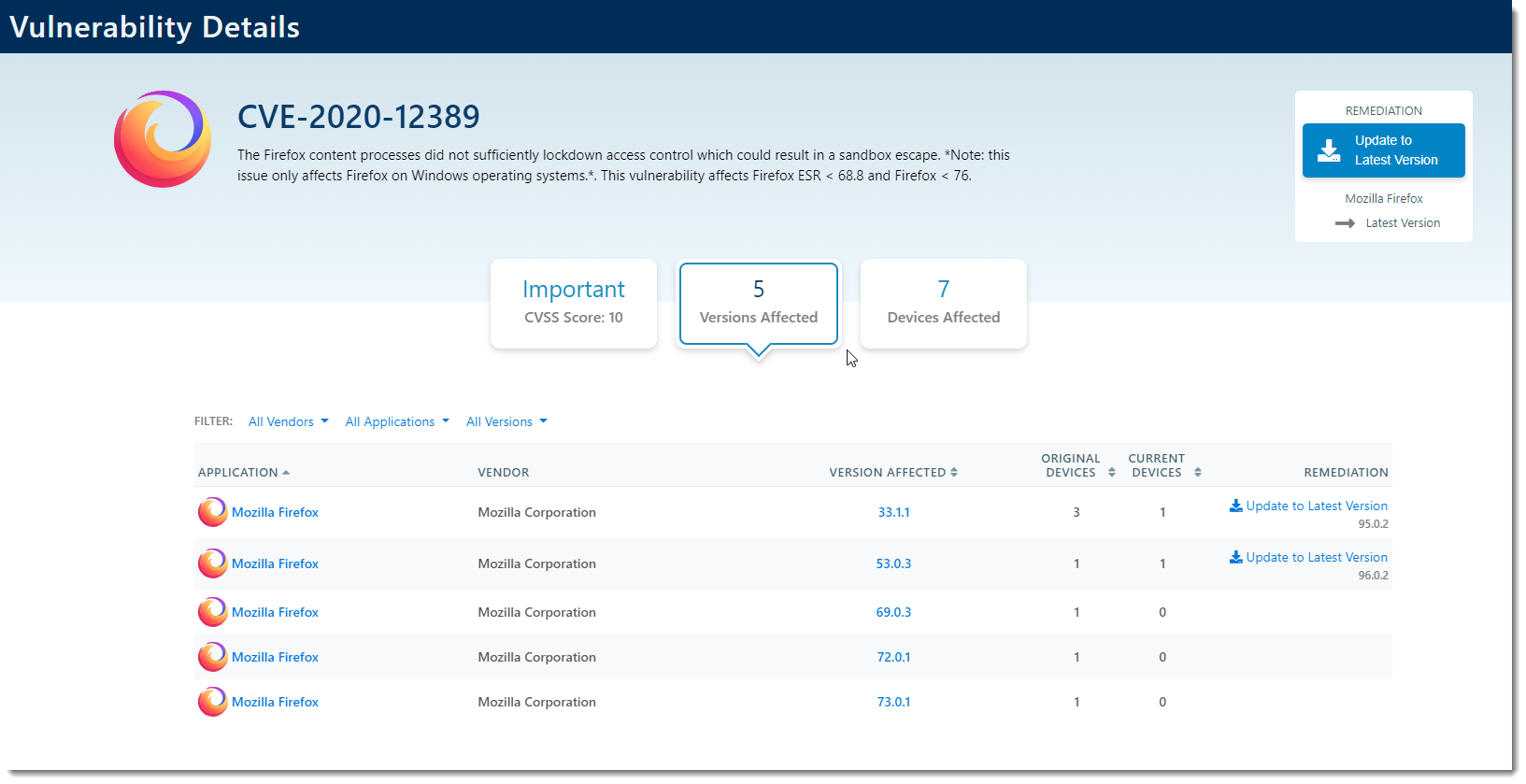 View 2: Versions Affected - This view shows you which applications are affected by the vulnerability, how many software versions are affected, and how many computers are affected, with the option to update individual versions, or all versions at the same time.
View 2: Versions Affected - This view shows you which applications are affected by the vulnerability, how many software versions are affected, and how many computers are affected, with the option to update individual versions, or all versions at the same time.
B - CVSS Score & C - Vendor
B - CVSS Score is the Common Vulnerability Scoring System. This column shows the severity of the identified vulnerability on a scale of 0-10 (with 0 being the lowest and 10 being the most critical). This column is sortable with no clickable links.
C - Vendor refers to the company which produces the application affected by the identified security flaw. This column is sortable with no clickable links.
D - Application
Application refers to the currently installed software applications being affected by the identified security flaw. Clicking on the name of the application will bring you to a screen providing more details.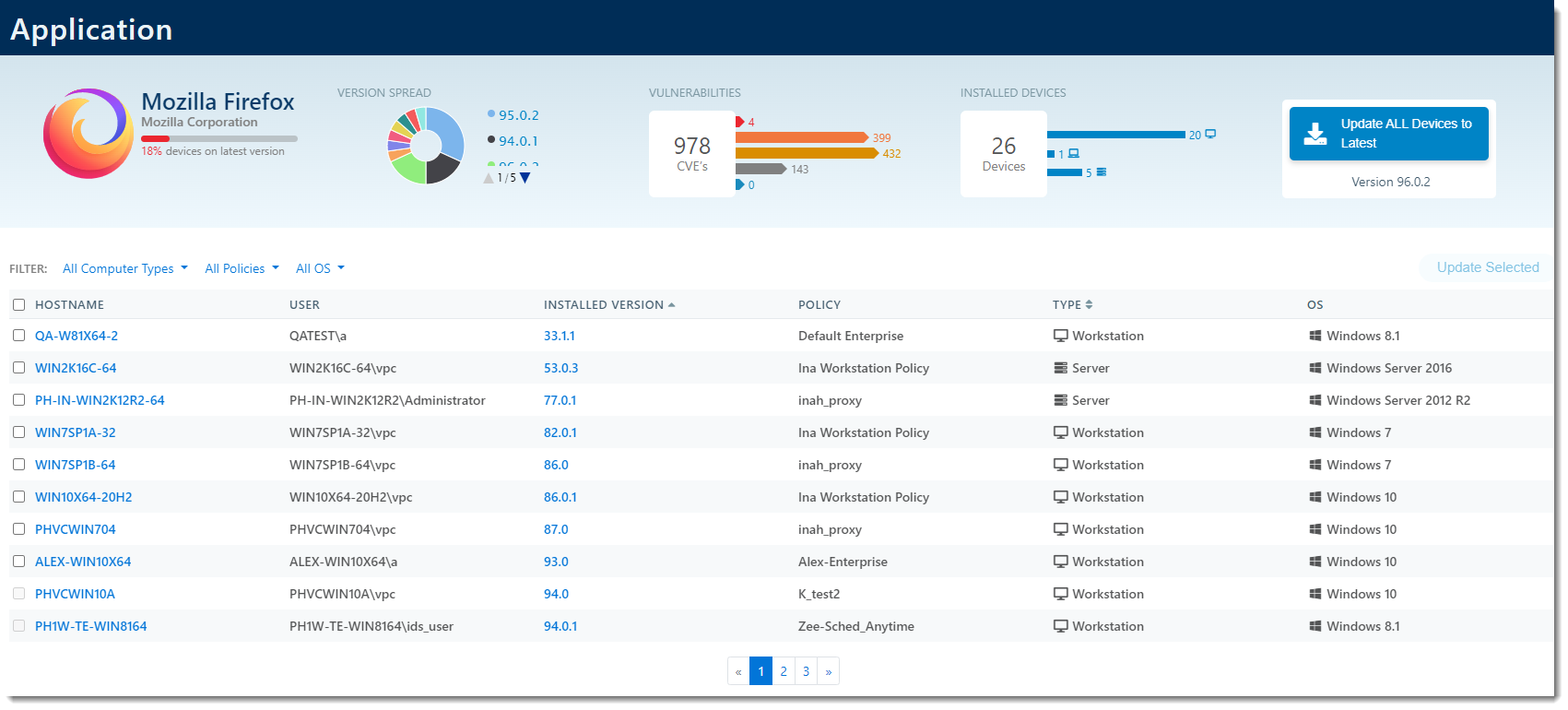
Details on the Application details screen include the hostname of the affected devices, the user on that device using that application, the currently installed version, the policy the device is assigned to, the type of device, and the operating system in use on the device.
E - Version
The currently installed version of the affected application; clicking on the version will bring you to a version details page.
The version details page has two views: Devices and Vulnerabilities
Devices will show the currently installed application version, how many devices have that version installed, the name of the devices, the users on those devices, the policy that device is assigned to, the type of workstation the device is, and the operating system running on that device. 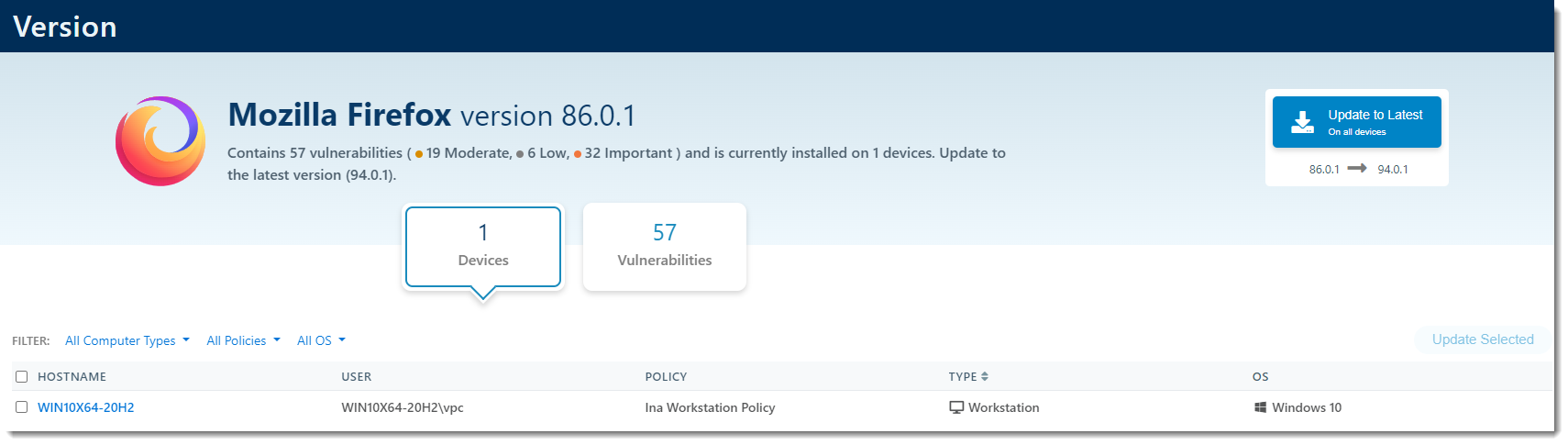
Vulnerabilities will show the number of vulnerabilities associated with that software version, the CVE identifier, the CVSS Score, the date the security flaw was published, how many devices are affected, and the ability to update individual CVD IDs.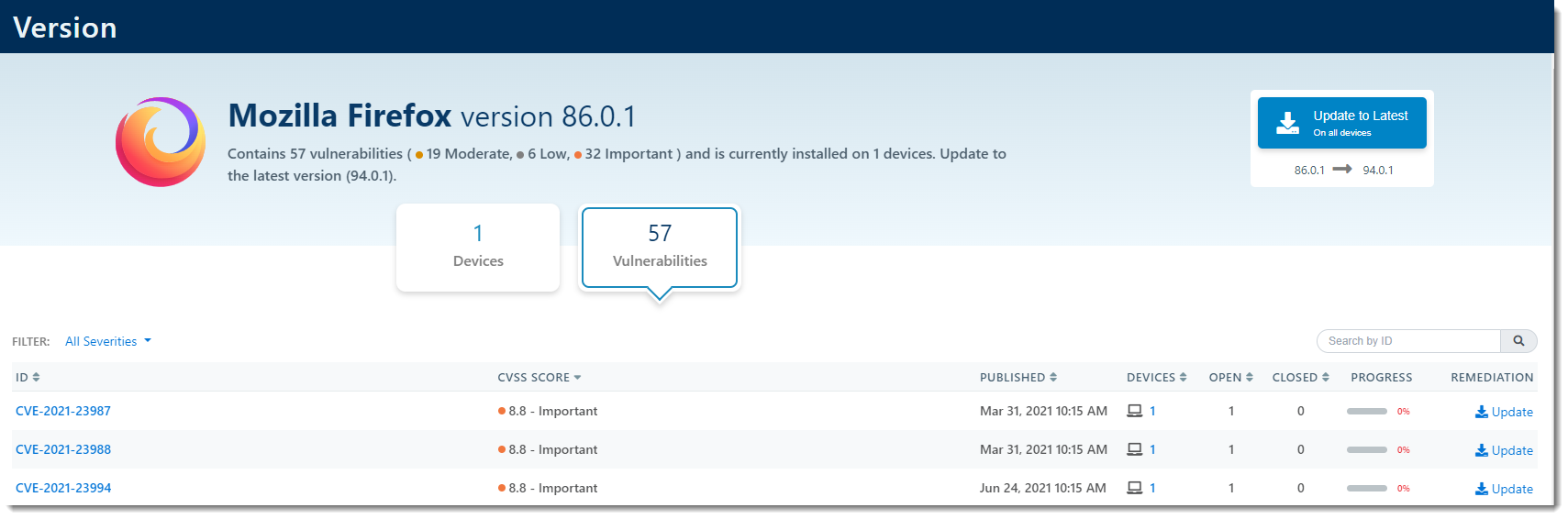
Update to the Latest Version
You can update to the latest version of the application from this screen in one of the following ways:
- From the Devices view, select the checkbox of the devices you'd like to update
- Click Update Selected above the table on the right side of the screen
or
- From the Vulnerabilities view, select Update in the Remediation column
or
- Click the Update to Latest on all Devices button in the top right corner of the screen
F - Hostname
Clicking on the hostname link will bring you to the device details screen.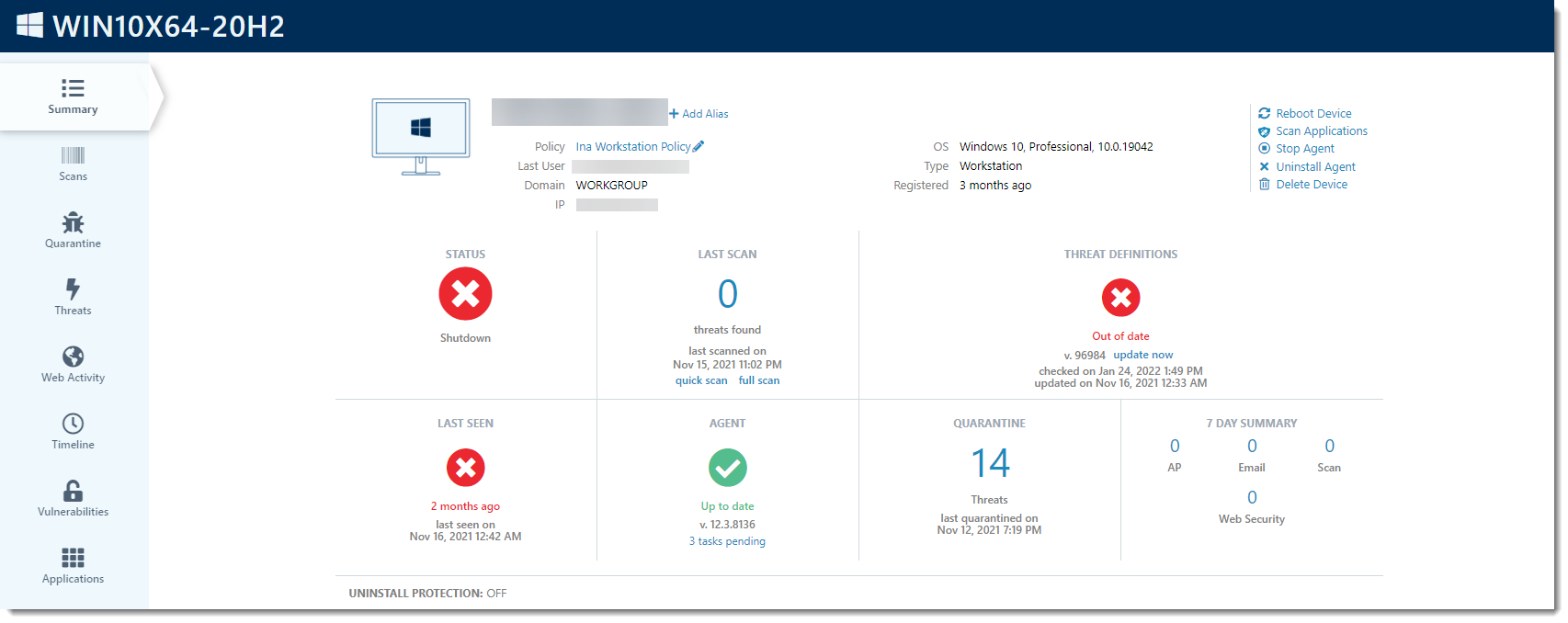
For more details, refer to Related Articles for an introduction to devices and agents.
G - First Seen & H - Status
G - First Seen indicates when the vulnerability was first reported
H - Status indicates the status of the vulnerability on a particular device
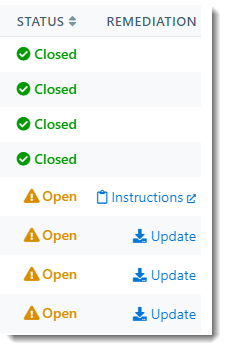
- Closed means the security flaw is no longer on the device
- Open means the security flaw is still affecting the device
I - Remediation
Remediation allows you to take action toward resolving the security flaw
- Update - Clicking Update will automatically update the application to the latest version
- Instructions - Clicking Instructions will bring you to the software developer's website with instructions on how to manually update the application
- Blank - A blank space in the Remediation column means there is no action to be taken as the application has already been updated to the latest version
Grouped by ID
Clicking Grouped by ID will show you a view that gives relevant information per CVE ID. For example, in the screenshot below, for each CVE ID, you can see specifically how many devices are being affected.
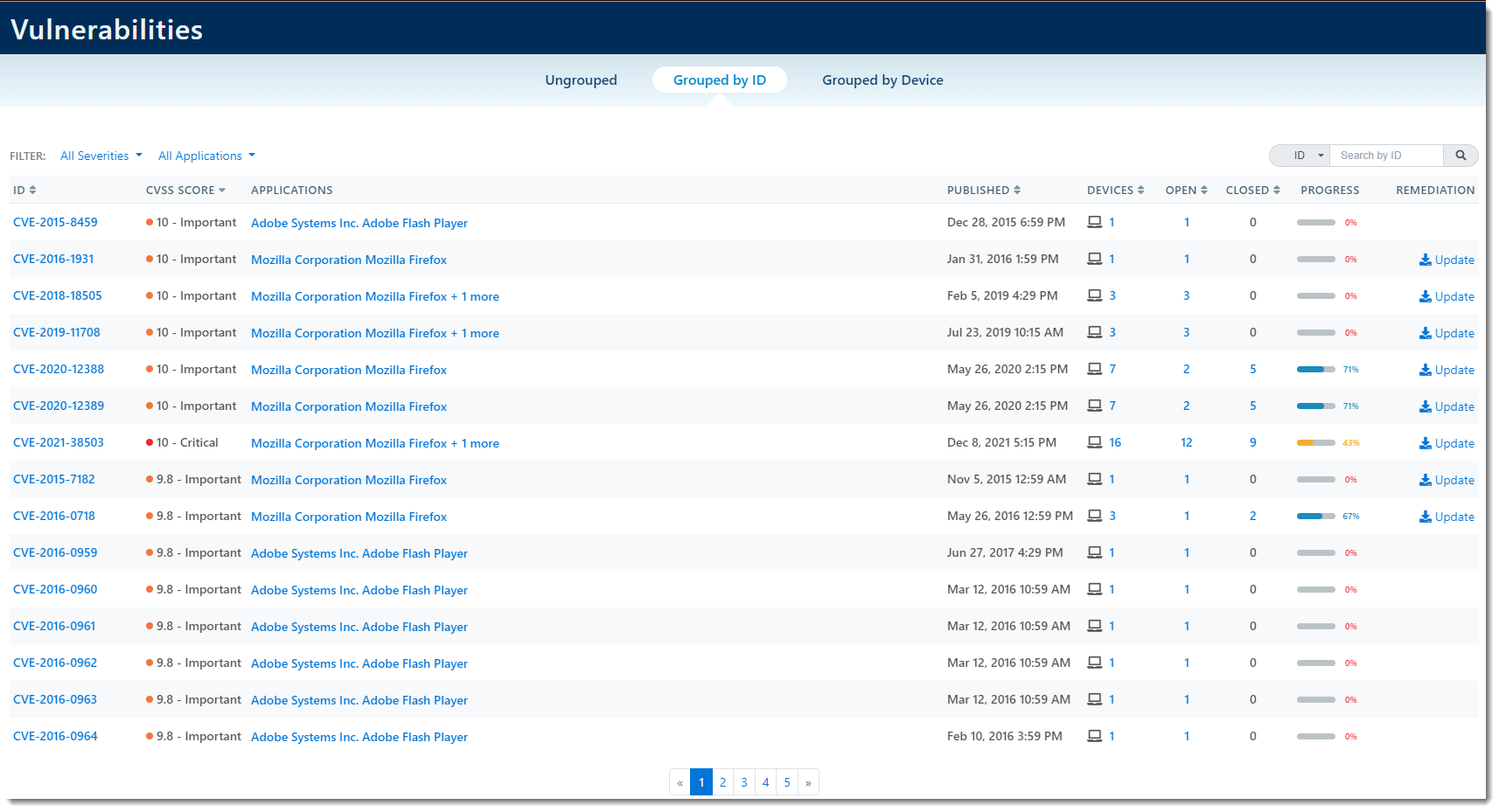
- Clicking on the CVE ID will bring you to the CVSS Score view of the Vulnerability Details screen (See A - ID above)
- Clicking on the Application will bring you to the Application details screen (See D - Application above)
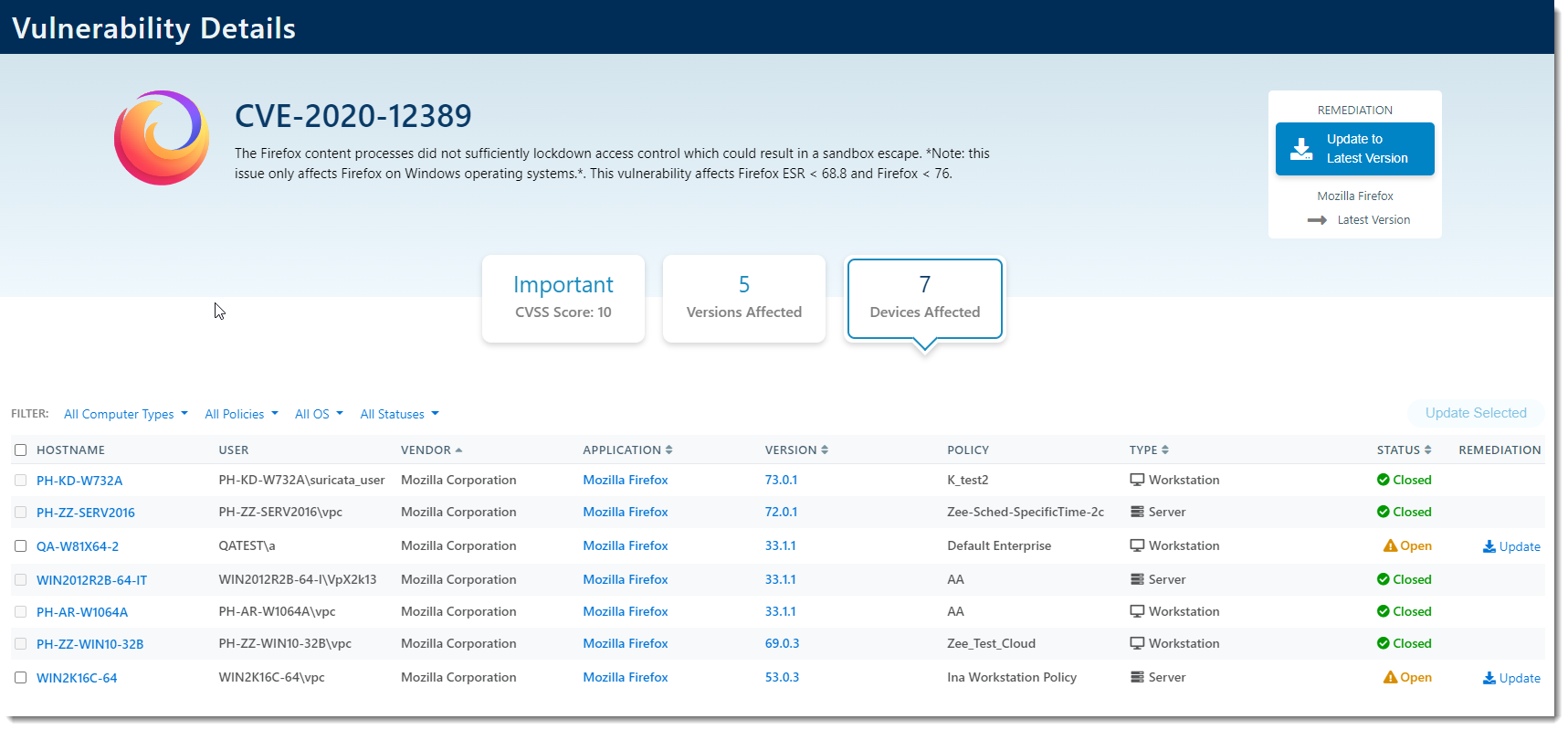
- Clicking on the number of Devices, the number of Open, or the number of Closed will bring you to the Devices Affected view of the Vulnerability Details screen (See A - ID above)
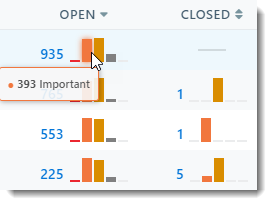
Grouped by Device
Clicking Grouped by Device will show you a view that gives relevant information per device/hostname. For example, in the screenshot below, for each hostname, you can see specifically how many open vulnerabilities are affecting them.
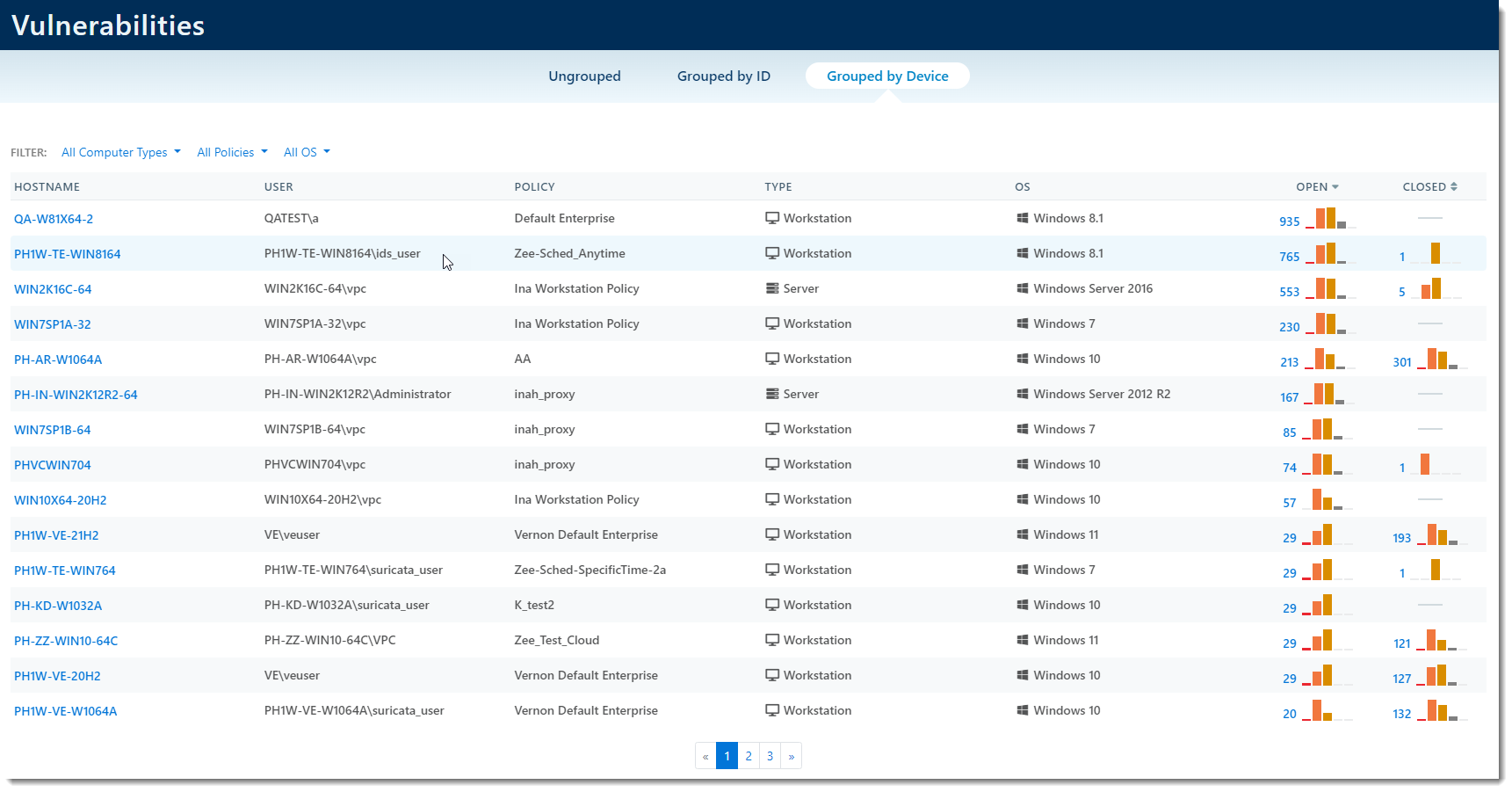
- Clicking on the Hostname will bring you to the device details screen (See F - Hostname above)
- In the Open and Closed columns, there are multiple options:
- Clicking on the number will bring you to vulnerability details for that specific device, showing you a list of all security flaws with the option to update the application
- On the graphs, hovering your mouse over each bar will break down the number of vulnerabilities by CVSS Score
- For example: In the screenshot below, the first row shows a total of 935 vulnerabilities; hovering your mouse over the orange bar shows that out of those 935 security flaws, 393 are categorized as Important