An event is generated when any type of activity, suspicious or otherwise, takes place on an agent device.
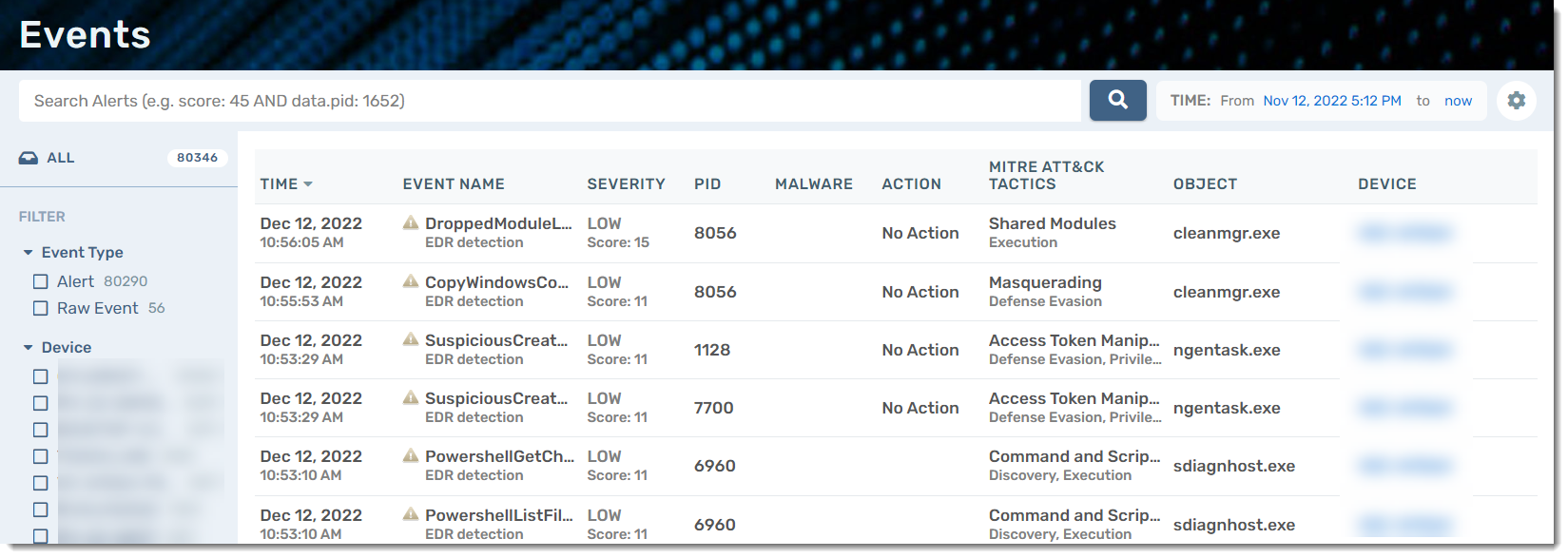
Find Events
The Events page has a search bar at the top; when you start typing, it will autofill certain item types you can search by. You can also choose a specific range of time from which to search. The Settings cog allows you to edit the information shown on the data table.
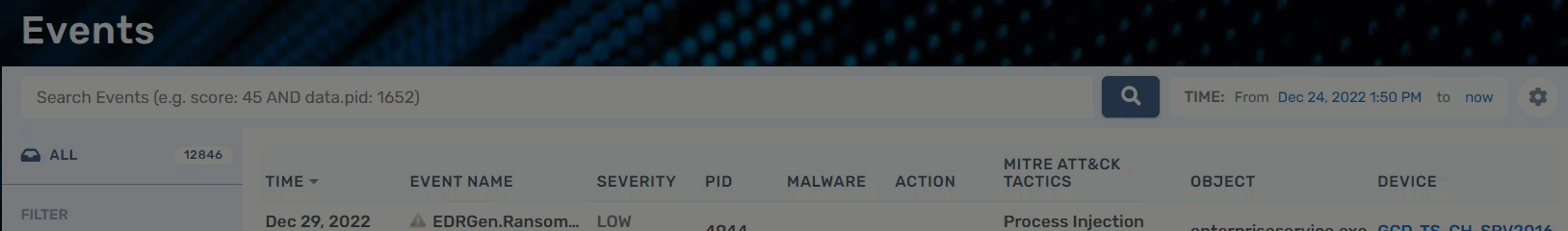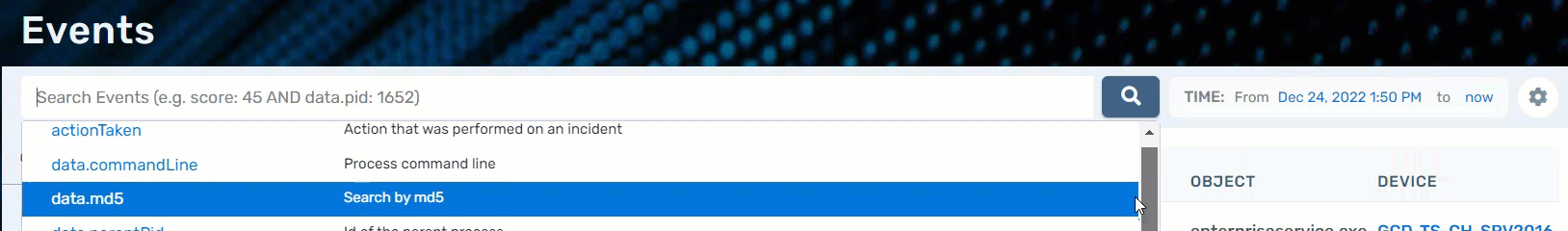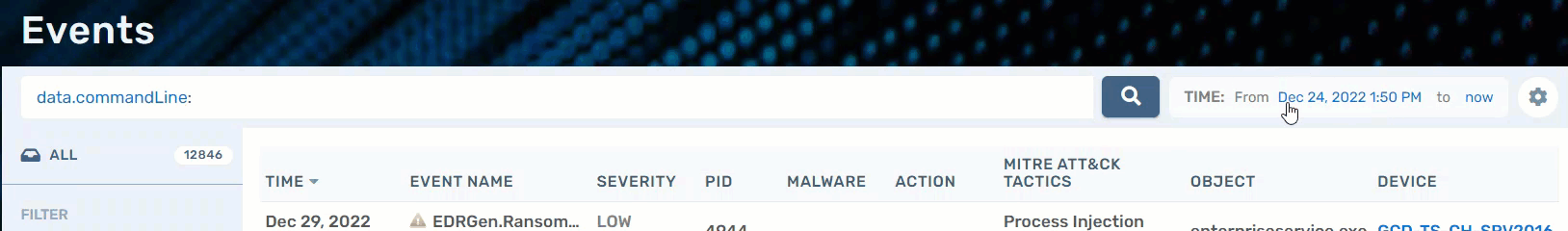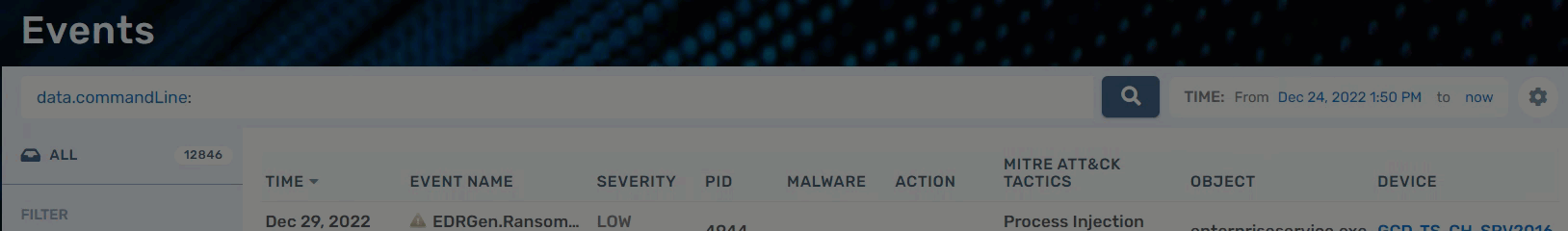
Please note, all available search options are not shown in the above picture example. Some search examples include:
- identity.name: <device name> AND
- identity.name: <device name> AND severity: HIGH
There is also an option to pivot by the values in the columns (e.g., PID or Event Name). If you hover your mouse over the values, you will see a + icon. Clicking on it will filter the list.
Filter Events
The Events page has several filters on the left light-blue menu to help you find specific events. You can filter Events by:
- Event Type
- Security Event is a type of alert/activity that is typically done only by malicious software but is not necessarily a threat
- Raw Event is any type of activity that could either be a potential threat or as benign as installing new, known-safe, software
- Device
- Event Name
- Severity
- Malware Family
- Mitre Att&ck Tactics
Events Table
| Header | Description |
|---|---|
| Time | When the event in question took place |
| Event Name | The name of the event |
| Severity | The severity of the event, including the severity score |
| PID | Internal process ID associated at the operating system level, which the VIPRE Agent extracts, along with process path, process name, etc., based on the type of event |
| Malware | Only applicable to security events; if the alert is trigged by known malware, it will be detected and populated here |
| Action | Only applicable to security events; refers to the remediation action that has been taken |
| Mitre Att&ck Tactics | The type of attack tactic used in the event |
| Object | The process associated with the event |
| Device | The agent device the event took place on |
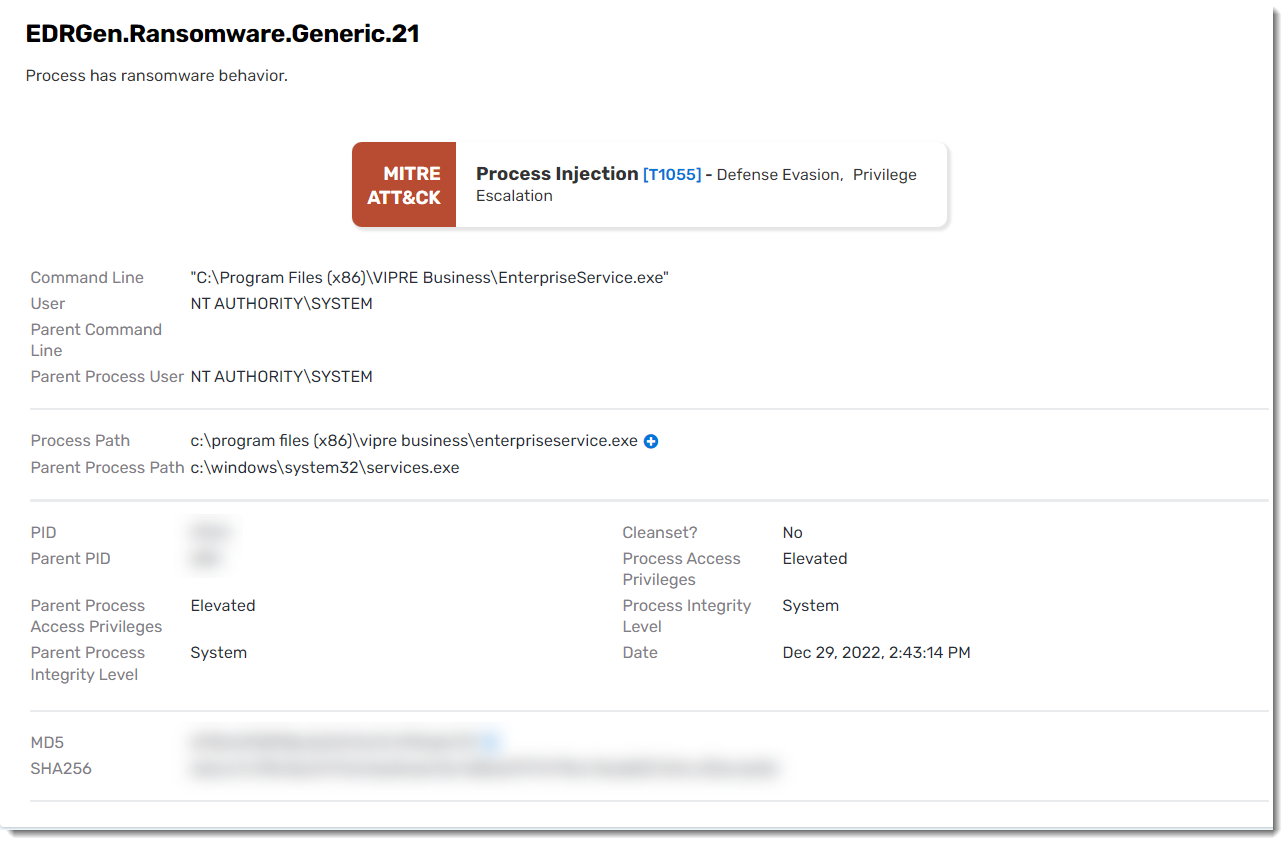
Event Details
Clicking on an event, will provide details about the event.