VIPRE Endpoint EDR+MDR uses a remote shell to connect to and manage individual endpoints directly from the web console to help with both investigations and routine endpoint maintenance.
Important
Remote Shell must be enabled in the policy settings under EDR+MDR Settings Group. View EDR+MDR - Policies for additional details.
The feature can be accessed in several ways:
- Within the context of an Incident, on the Incident Summary screen, select the Remote Shell button to invoke the remote shell
- While looking at a Device (Devices > click on a device name) select the Remote Shell shortcut command at the top right
For additional security, if you have enabled Two-Factor Authentication, you will be asked to authenticate again before the remote shell will connect to the device.
When selected, the Remote Shell will appear at the bottom of the screen and initiate a connection to the selected device. Because the shell uses the built-in agent communications channel, as long as the agent can connect to the VIPRE Cloud console, you should be able to establish a remote shell session with the device.
The Remote Shell provides a constrained set of commands that you can run against an endpoint; for security reasons, it is not a general-purpose shell under which you can run any arbitrary script or command (there is a Policy setting that controls how limited the command set is). You can use the Remote Shell to examine and manage the disk, registry, processes, and memory. You can also examine the local Event Log, and upload files back to the VIPRE console for later review, to attach to the Incident, or for later sandbox analysis.
Using Remote Shell
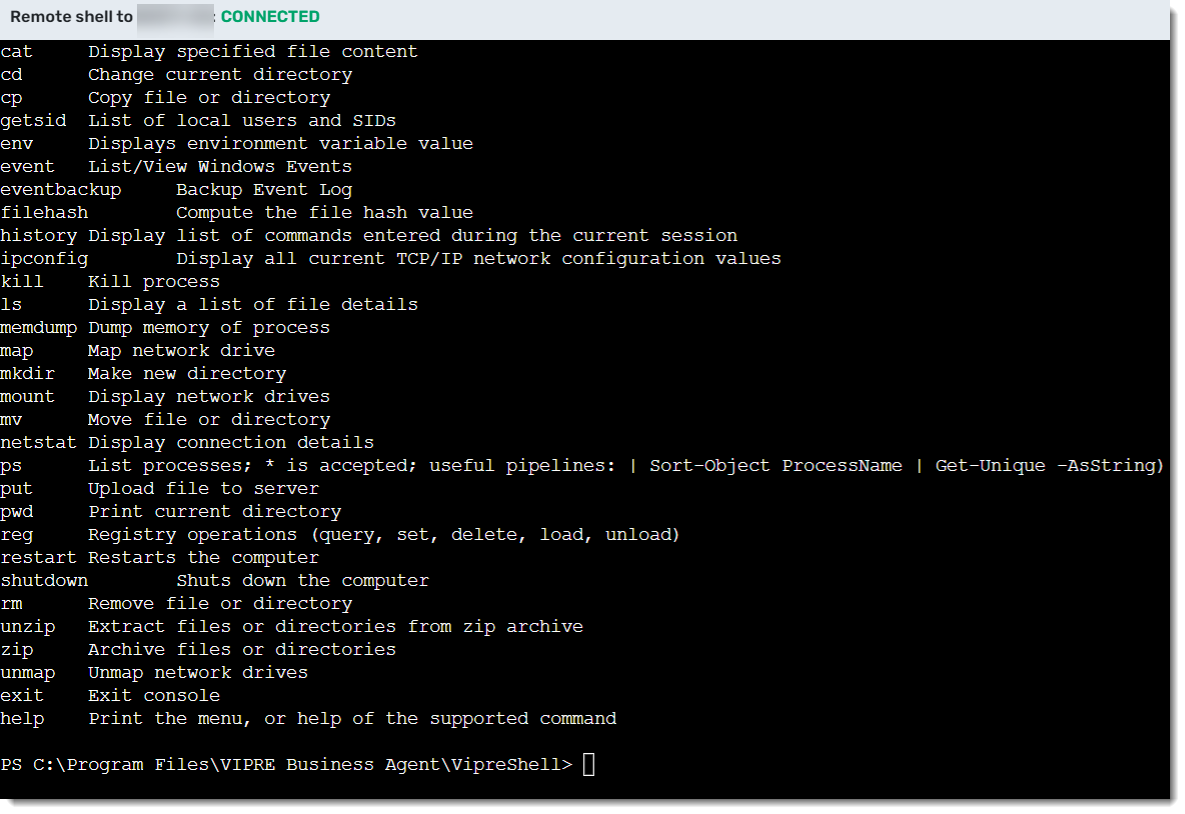
- In your EDR+MDR site, navigate to Manage > Devices to identify an active machine and click on the device name
- Under the Summary tab, on the top-left corner of the screen, select Remote Shell
- A CLI will open at the bottom of the screen (see screenshot above)
- Type 'help' to view a list of all applicable commands with a brief description of what they do
- Use the various commands to look at files, processes, registry keys, etc.
- When done, type 'exit' to disconnect from your current remote session
View all Attempted Remote Shell Sessions
- Navigate to the Monitor > Reports menu entry
- Choose the 'Shell History Report' (the last entry on this list)
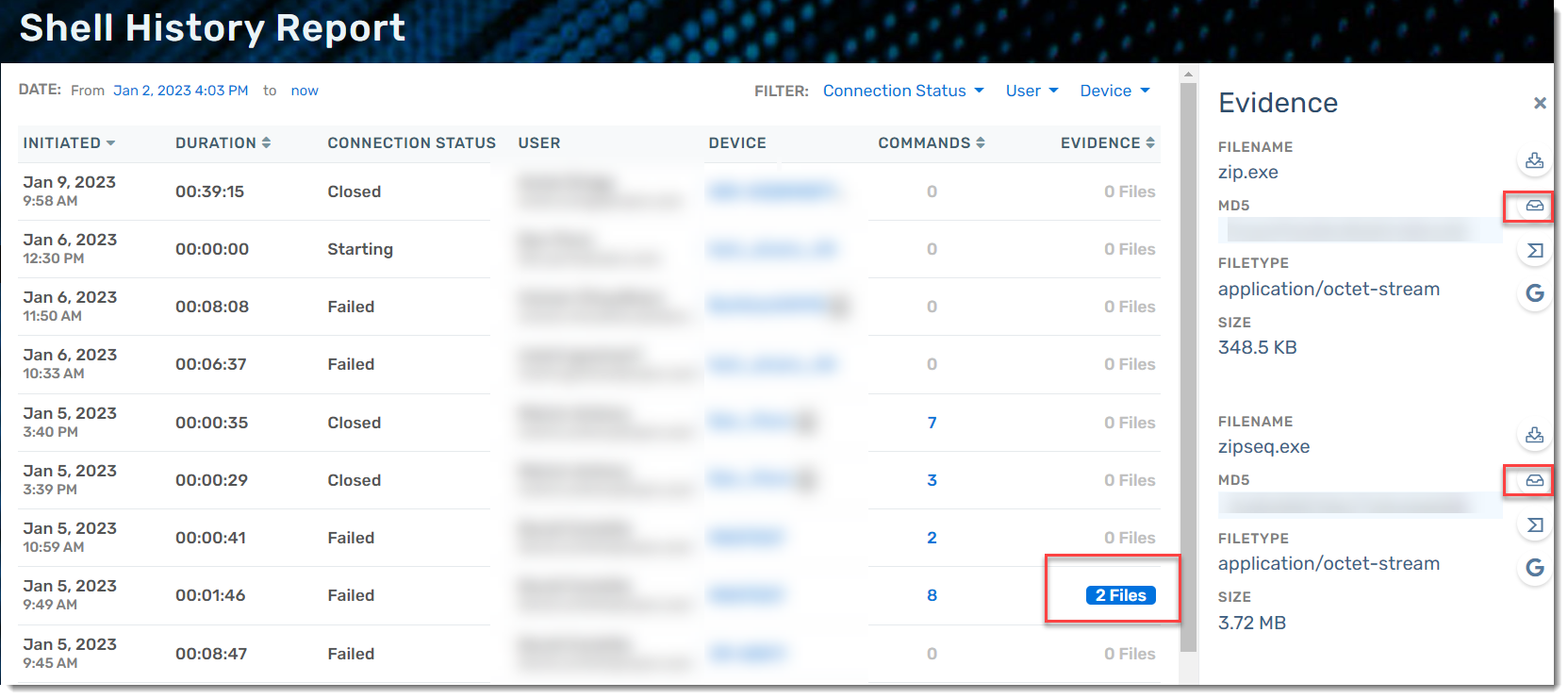
- You will see a full listing of all attempted Remote Shell sessions along with a summary of who, when, and what commands were executed
- If any files were saved as 'evidence', it will show on this list
- In the Evidence column, if any files were collected, the number will show up here as a clickable link
- Click on the desired session files to see details, including file name, encryption, file type, and size
- There are several options once you're in this view
- If any files were saved as 'evidence', it will show on this list
VIPRE Remote Shell Commands
| Command | Description |
|---|---|
cat |
Display specified file content |
cd |
Change current directory |
cp |
Copy file or directory |
getsid |
List of local users and SIDs |
env |
Display environment variable value |
event |
List/View Windows Events |
eventbackup |
Backup the Event Log |
filehash |
Compute the file hash value |
history |
Display list of commands entered during the current session |
ipconfig |
Display all current TCP/IP network configuration values |
kill |
Kill process |
ls |
Display a list of file details. |
memdump |
Dump memory of process |
map |
Map network drive |
mkdir |
Make new directory |
mount |
Display network drives |
mv |
Move file or directory |
netstat |
Display connection details |
ps |
List processes; * is accepted; useful pipelines: | Sort-Object ProcessName | Get-Unique -AsString) |
put |
Upload a file to VIPRE Cloud |
pwd |
Print current directory |
reg query |
Query registry subkey or values |
reg set |
Update or create registry value/key |
reg delete |
Delete registry key or value |
reg load |
Load registry hive data |
reg unload |
Unload registry hive |
rm |
Remove file or directory |
zip |
Archive files or directories |
unmap |
Unmap network drives |
unzip |
Extract files or directories from zip archive |
. |
Run PowerShell script |
exit |
Exit console |
help |
Print the menu, or help of the supported command |
shutdown |
Shuts down the computer. |
restart |
Restarts the computer. |