Microsoft Entra ID (Active Directory) is a cloud-based identity and access management service that we've integrated with VIPRE Email Security Cloud allowing Email Cloud to sync user and group accounts that belong to your managed domain.
Important
Only one directory service can be active and enabled at a time. For example, you can use either Azure or LDAP but not both. Enabling one directory service will disable the other. You will be prompted before saving the new configuration.
When switching from one directory service to the other, previously synced users no longer in the current directory service sync will be considered user conflicts. These users can be found in the User Conflict Tab and are marked for deletion as directed in the Delete User After setting.
There are two main parts to set up the Entra ID integration with Email Security Cloud.
Part 1 - Configure Entra ID Integration
Follow the steps below to configure Entra ID to integrate with VIPRE Email Security Cloud. These steps all take place in Entra ID and assume you already have a Microsoft Azure account.
Step 1 - New App Registration
- Navigate to portal.azure.com and log in with your Microsoft Azure account credentials
- On the left-side menu, under Manage, select App registrations
- Click New Registration and name your registration
- Any name will work but it's recommended to use a name that identifies what app you're registering (e.g., in this case, VIPRE Email Cloud)
- Click Single tenant
- Skip the redirect URI and click Register
Step 2 - API Permissions
- On the left-side menu, under Manage, select API Permissions
- Select Add a permission
- Select Microsoft Graph
- This is the API that the Email Cloud portal uses to communicate with Azure
- Select API Permission type Application
- Select the following Application Permissions
- Directory > Directory.Read.All
- Group > Group.Read.All
- GroupMember > GroupMember.Read.All
- User > User.Read.All
- Click Add Permissions
- Look for the row that shows User.Read, click the ellipses (...) on the right, and select Remove Permission
- Click Grant admin consent for <your.tenant.name.here>

Step 3 - Certificates & Secrets
- In the breadcrumb trail, select the API name
 Example showing where to locate the tenant and API names. Your tenant name, and API name, won't match this image.
Example showing where to locate the tenant and API names. Your tenant name, and API name, won't match this image.
- On the left-side menu, select Certificates & secrets
- Under Client secrets, click New client secret and fill in the following information:
- Description - This can be whatever you want
- Expires - No matter which timeframe you choose, it's important to set a reminder for yourself to both create a new client secret, and save the new client secret into the Azure Connect tab (step 5 below), before expiry. Failure to do so could break the sync between Email Cloud and Entra ID.
- Click Add
Step 4 - Gather Necessary Info for VIPRE Email Cloud
- Open a new text file on your computer and copy/paste the following information from the Microsoft Entra ID portal into the blank text file:
- Under Client secrets, copy the Value and paste it into your blank text file

- In the breadcrumb trail, select the API, copy the Application (client) ID and paste it into your text file
- From the same page, copy the Directory (tenant) ID and paste it into your text file

- Under Client secrets, copy the Value and paste it into your blank text file
Part 2 - Enable and Sync Entra ID
In part two, we'll take what we did in the Entra ID portal and configure it to sync with VIPRE Email Security Cloud.
Step 5 - Connect
- In a separate browser tab, navigate to your Email Cloud admin portal and log in
- On the left-side menu, click Service Settings, then select Directory Services
- On the main page, select Entra ID

- Place checkmark next to Enable Azure Sync
- Copy the Directory (tenant) ID) from your text file and paste it into the Tenant Domain field
- Copy the Application (client) ID from your text file and paste it into the Client ID field
- Copy the Client secret from your text file and paste it into the Client Secret field
- Select a Sync Frequency from the dropdown menu
- The default sync frequency is 6 hours
- Select an amount of time to Delete Users After from the dropdown menu; see the User Conflicts section below for more details
- The default is 7 days
- Click the checkbox if you want to include disabled/deactivated user accounts in your sync
- This is unchecked by default
- If you want to include Custom Filters, enter those in the text field here
- Custom Filters are only applied to syncs of users. Groups are not included.
- For full details, including supported custom filters and examples of queries, visit Custom Filters for use with Entra ID Sync to open a new browser tab
- Click Save in the bottom right
- Click Test in the bottom left to verify the connection
- If successful, a green message will appear in the top-right "Azure Connection test was passed"
- If unsuccessful, a red message will appear in the top-right "Azure Connection test failed"
- Verify the Tenant Domain, Client ID, and Client Secret were copied correctly from the Azure portal
- Click Sync Now
- A green message will appear in the top-right "Azure sync has successfully started"
Once the sync has completed, you will be able to see all of your users by clicking Users in the left-side menu. Looking in the Source column, you will be able to tell which users were added via Azure.
 VIPRE Email Security Cloud - Users
VIPRE Email Security Cloud - Users
Congratulations! You have successfully configured Entra ID to sync with VIPRE Email Security Cloud! Continue reading below to learn how to further manage your Entra ID integration
Managing Entra ID in Email Cloud
Exceptions
The Exceptions tab is where you can select any name from the User List that you want to exclude from the Entra ID sync with VIPRE Email Cloud. This means any exceptions will also be excluded from any custom filters you set up on the Connect tab.
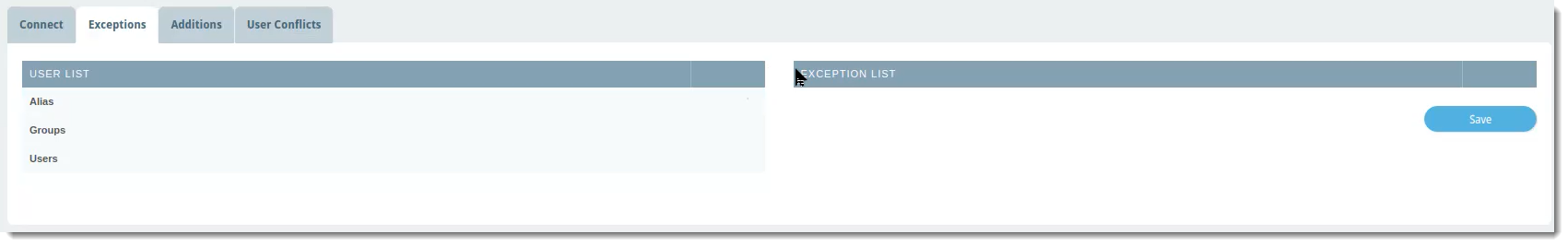 VIPRE Email Security Cloud - Entra ID Sync Exceptions
VIPRE Email Security Cloud - Entra ID Sync Exceptions
To exclude a user, group, or alias from the Entra ID sync:
- In the User List column, which shows a complete view of your directory server, locate the row with the name of the user, group, or alias you want to exclude
- Click the blue arrow in the same row as the name to add that name to the Exception List
- Click Save
Additions
The Additions tab allows you to manually add users to include in the Entra ID sync. For example, this would be useful for adding any new employees that may need to be added in between syncs.
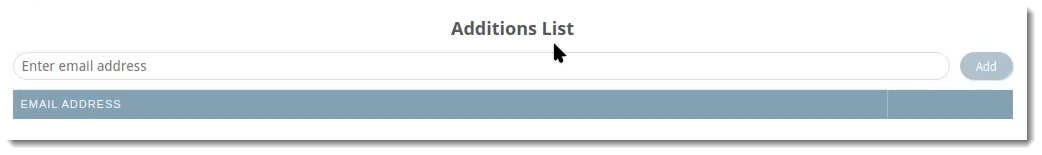 VIPRE Email Security Cloud - Entra ID Sync Additions
VIPRE Email Security Cloud - Entra ID Sync Additions
To include an additional user to your Entra ID sync:
- Type the email address of the user you want to include
- Click Add
Users added to your Entra ID sync via this method will be listed on this tab. They will also show up in the list under Users in the left-side menu with the source as Azure.
User Conflicts
The User Conflicts tab will show users that previously synced in the portal but are no longer in the directory server.
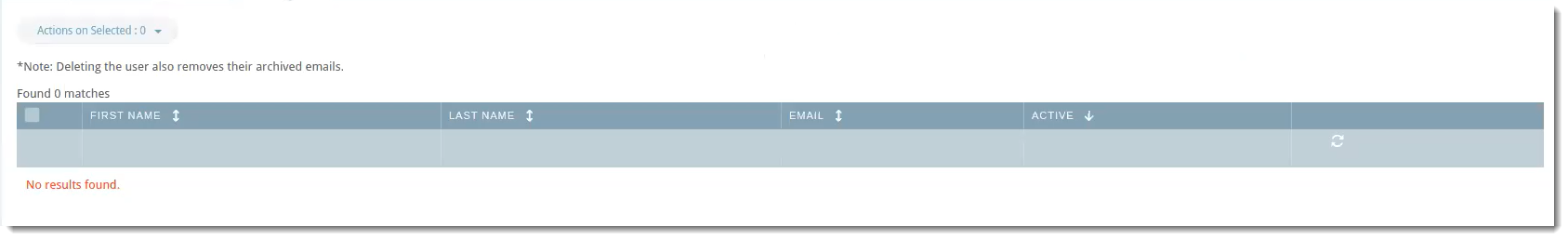 VIPRE Email Security Cloud - Entra ID Sync User Conflicts
VIPRE Email Security Cloud - Entra ID Sync User Conflicts
Possible actions within this tab are: Delete, Ignore, Export, Deactivate
Example Use-Case
You notice there two users showing in User Conflicts. Let's say that when you were first setting up Entra ID sync, under the Connect tab, you set Delete Users After to 7 days. You're fine with one of the users being deleted because the employee no longer works for your company. The other user, however, is on maternity leave and will be coming back in 12 weeks.
- Click the checkbox next to the user and select your desired action.
In the example above, you could use Ignore so that the user will not be deleted after 7 days.