TLS (Transport Layer Security) is a cryptographic protocol that provides end-to-end security of data sent between applications over the Internet. TLS encrypts data sent over the Internet to ensure that eavesdroppers and hackers cannot see what you transmit, which is particularly useful for private and sensitive information.
TLS Stages
We support TLS, which is contained in two stages, whether inbound or outbound:
-
Private Leg refers to mail sent between our mail servers and your own. It enforces TLS on the connection to us, as seen from the inbound routing page. If TLS is enforced for the private leg, then the customer MUST have a valid TLS certificate. If TLS is not enforced, mail flow will be affected, and the customer will not be able to receive inbound or send outbound emails.
-
Public Leg refers to emails sent from our servers to external servers or vice versa. These domains MUST have a TLS connection, or emails will be rejected.
Opportunistic TLS means that if a server has a TLS certificate, TLS will be used. After the handshake, we will show a green padlock under TLS in the Message Logs screen for private and public legs. TLS is opportunistic by default, so if a server does not have a TLS certificate, the email will still be delivered, just without TLS.
TLS Settings
The TLS settings within the VIPRE Email Security portal can be managed under Policies in the left-side menu.
This screen is separated into two stages – Public and Private Leg, both of which can be modified. This screen allows you to require TLS encryption for certain mail routes. Mail not transmitted over TLS-encrypted connections will be rejected in the presence of these rules. Depending on the settings, you can reject emails if they do not support TLS connections on the public or private leg.
Public Leg
To create a new rule:
- Navigate to the VIPRE Email Security Cloud web console
- On the left-side menu, click Policies, then select Enforce TLS
- Under Public Leg, type a domain in the textbox
- Click the checkbox next to Inbound to require TLS for messages sent from this domain and/or Outbound to require TLS for messages sent to this domain
- Click Add
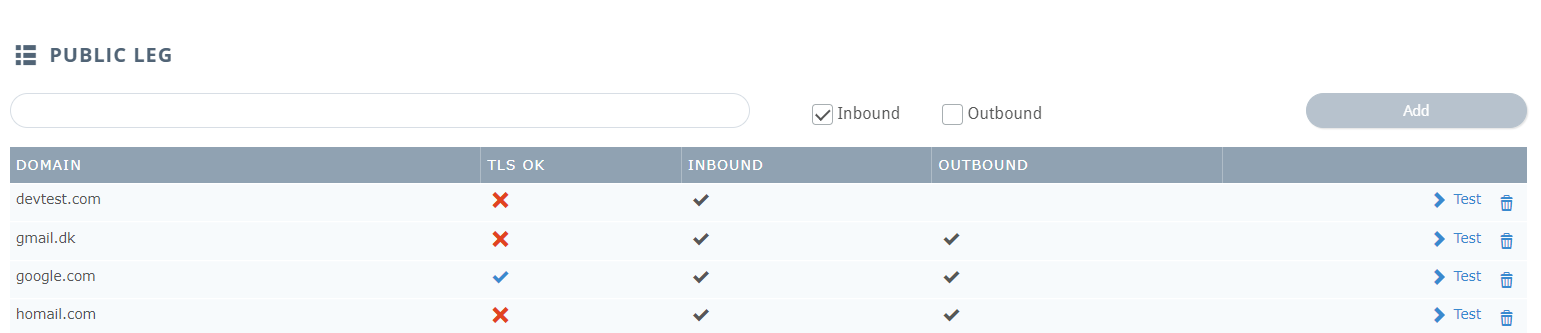
The TLS OK column shows whether a TLS-secured connection can be established between our servers and all of this domain's mail servers. To see a detailed breakdown of the test results, click the icon (either a blue check or a red x) in this column. To try the test again, use the Test link for that domain.
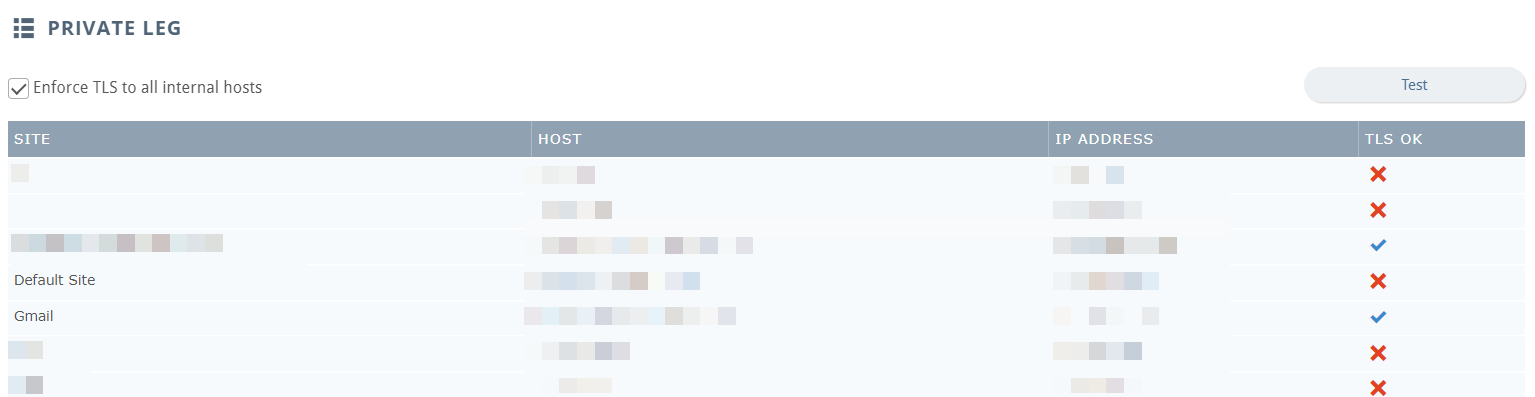
Private Leg
To enforce TLS on these connections, use the Enforce TLS to all internal hosts checkbox. A table of your mail servers indicates which hosts can establish TLS-secured connections to our servers. To try these tests again, use the Test button.
There are several websites available for TLS lookup on a domain, including:
-
https://www.checktls.com/TestReceiver
-
https://www.ncsc.gov.uk/guidance/using-tls-to-protect-data
-
https://www.ncsc.gov.uk/information/mailcheck
VIPRE has TLS built in for the public leg. It is opportunistic and will be used on the public leg if the sender also has a verified TLS certificate.
Sometimes, a third party must implement a specific domain-to-domain connection to support end-to-end encryption. They will need our VIPRE certificate details to create the end-to-end encryption with another third-party domain to support a TLS connection.
Our certificate details are available for our customers' administrators and will be shared with our support team upon request.
TLS ADVANCED POLICY
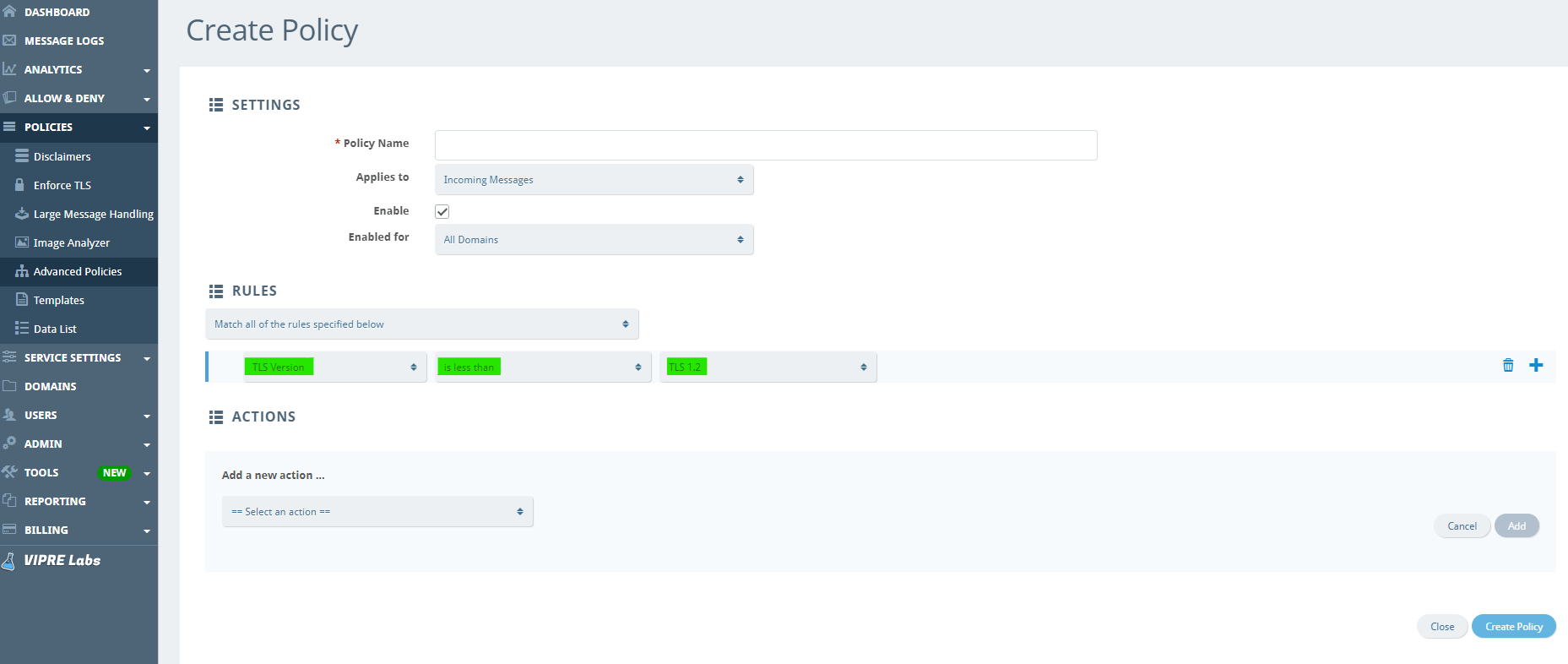
In Advanced Policies, you can also create a custom policy to enforce TLS1.2; it can be customized for both inbound and outbound emails.
With this, you may, for example, have TLS enforced on all emails and instead add the exclusions you want to allow with less than TLS 1.2. An example of how that would look can be seen below. You would then add an exclusion rule pointing to a data list.
MTA-STS
MTA-STS (Mail Transfer Agent Strict Transport Security) is a way to protect TLS encryption on emails from downgrade attacks. Basically, this is a higher level of protection, protecting the already protected end-to-end encryption.
The objectives of MTA-STS are to:
- Make it harder for an attacker to get emails sent to an alternative location
- Make sure that TLS encryption is always used to prevent attackers from downgrading email encryption on emails to clear text
Further information on how to set up the MTA-STS policy, align it with the MX records, and all the protection it delivers to prevent vulnerabilities can be found here on NCSC.gov.uk MTA-STS.
Troubleshooting
CERTIFICATE MISMATCH
A TLS check may give a Certificate Mismatch if a customer uses legacy MX records. A certificate mismatch does not mean there is a problem with the TLS connection but that the lookup checks the MX records towards our certificate and thinks it doesn't match. Updating the MX records to our most recent format found HERE will resolve the certificate mismatch for you.
If you require additional assistance, contact our Support team.