Remote Browser Isolation (RBI) allows users to review a potentially malicious link in a safe environment without the risk of exposing the user's computer or network.
Important
Remote Browser Isolation requires the Advanced Threat Protection package. If you do not already subscribe to VIPRE Email ATP, contact your account manager or our Sales team.
Meet Remote Browser Isolation
The following video introduces Remote Browser Isolation and demonstrates how it works.
Now that we've seen what RBI looks like and what it does, continue reading to learn about how to use it.
Step 1: Accessing Remote Browser Isolation
There are several ways to access RBI, which we'll detail here:
- Email Security Cloud Tools
- Analytics > Link Click Analysis
- Analytics > Threat Explorer
Email Security Cloud Tools
Scenario: You have a list of URLs that you obtained outside of Email Security Cloud and would like to review them in the safe environment of a remote browser.
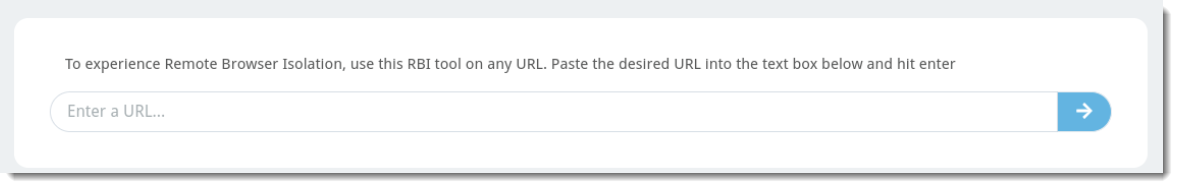
- Navigate to Tools within the Email Security Cloud web console and select Remote Browser Isolation
- Enter a URL in the text box and press the blue arrow
Analytics > Link Click Analysis
Scenario: You're already working in the Link Click Analysis dashboard to determine which email address sends your organization the highest number of malicious links. You see one URL you aren't sure about and would like to review it without risking the safety of the computer you're using.
- Select the specific threat to open details and click Launch Remote Browser
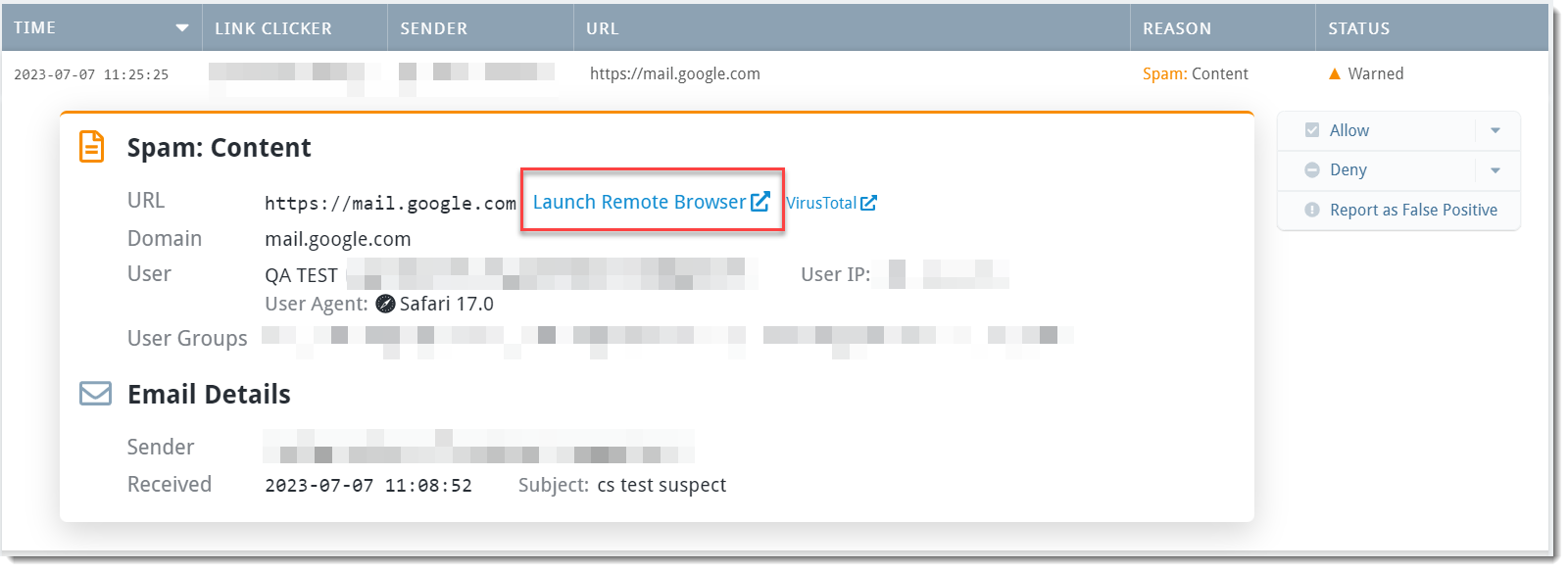
See Email Analytics for more details on what Link Click Analysis is and how to use it.
Analytics > Threat Explorer
Scenario: You're already working within the Threat Explorer tool to determine which user groups receive the most spam emails and want to investigate one particular email a little closer.
- Select the specific threat to open details and click Launch Remote Browser
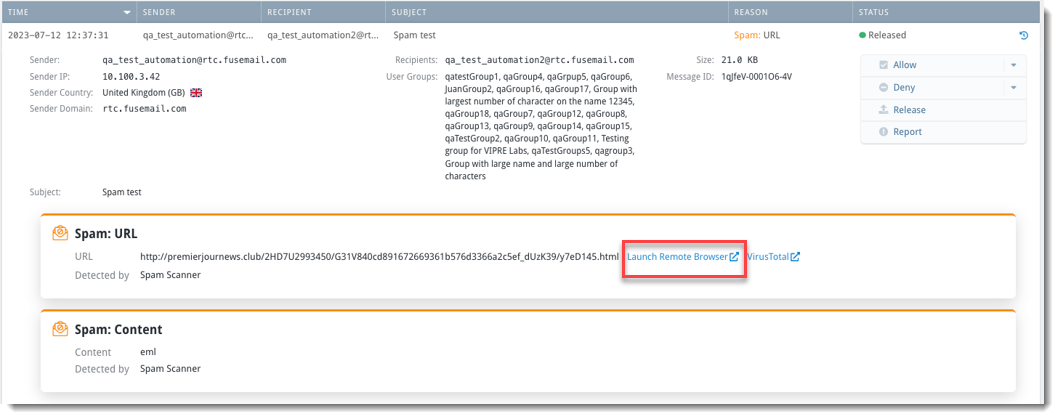
See Email Analytics for more details on Threat Explorer and how to use it.
Step 2: Reviewing the URL within a Remote Browser
Regardless of your path, all of the above RBI access points will lead you to the same place. The website you have chosen will open in a new browser tab, and you should see a page that looks similar to this:
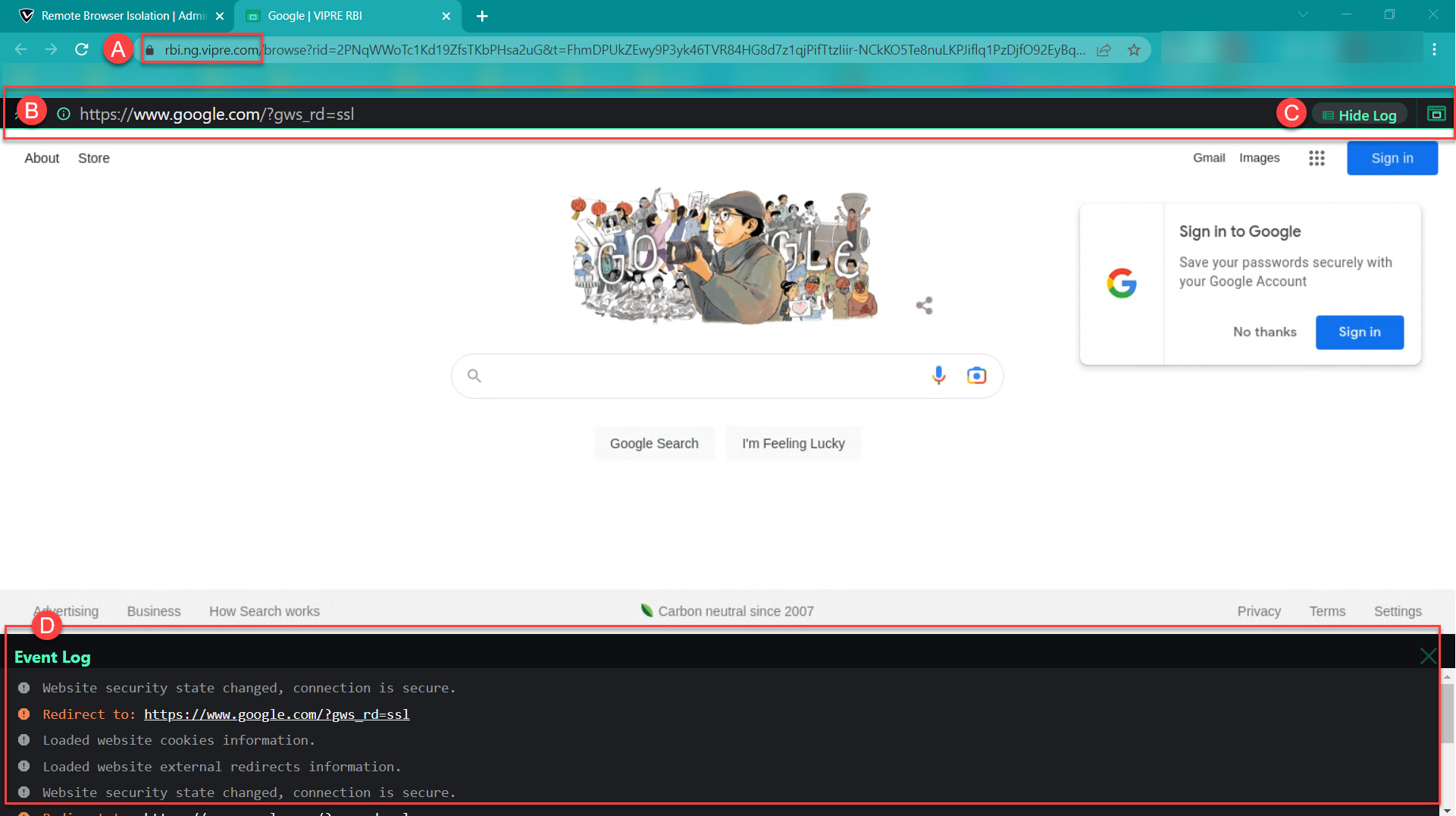
- You will notice the URL in the browser’s address bar indicates it is part of VIPRE’s RBI feature
- Here, you will see the original URL that you put into the RBI field within the Email Security web console
- To show the event log click Show Log; when the event log is visible, it will say Hide Log
- At the bottom of your browser window is the Event Log
- The Event Log provides details such as what was loaded along with the webpage being viewed (e.g., cookies, scripts, redirects, etc.), which can be extremely helpful in determining the potential threat level.
Once you’ve finished reviewing the website remotely, you can close the browser tab or window to close the RBI session; otherwise, the RBI session is terminated automatically after 30 seconds of inactivity.
If you do not already subscribe to VIPRE Email ATP, contact your account manager or our Sales team.