Product release information for VIPRE Agent for Windows version 13.0.8352 on April 6, 2023.
What's New
Updates
April 6, 2023: VIPRE Agent for Windows v13.0.8352 is now generally available.
March 23, 2023: Custom build for VIPRE Agent for Windows version 13.0.8352 is released.
In the last several months, we've made many significant backend changes allowing VIPRE to continue communicating with the latest version of Microsoft Windows Security Center. As a result, it's important to note the following changes to our system requirements list.
- Windows 10 RS5 (32- & 64-bit) - Version 1809 must install Oct 2018 update; newer versions must install 9C (September 21, 2021) update
- Windows 7 SP1 non-ESU (32- & 64-bit) - no longer supported
- Windows 7 SP1 ESU - Must install May 2021 update
- All other supported versions of Windows that are older than Windows 10 need to install 10B (October 12, 2021) update
See the System Requirements section below for a complete list of all system requirements.
Although this new agent has been tested carefully under a wide variety of conditions, out of an abundance of caution, we recognize that additional field testing is desirable before a significant launch. For this reason, we are asking YOU to please help us by deploying this new custom-built agent to test systems in your environment. This helps ensure that no problems will occur with the final release and that you will not experience any disruption to your production networks.
VIPRE Recommends
For new VIPRE Agent installs, Windows must be updated to the appropriate versions before attempting to install the VIPRE Agent.
If VIPRE Agent is already installed, we recommend verifying that the Windows upgrade media contains the required updates before upgrading Windows. For example, let's say your computer is running Windows 7 with the ESU update installed. Once the latest VIPRE agent is installed running on Window 7 and the version of Windows they are upgrading to should either have it out of the box or slipstreamed into the upgrade media
Special Instructions
Manage Agent Software Updates
VIPRE Endpoint Security provides flexible control over how agent software updates are delivered to your environment via the VIPRE Cloud web console. You can choose a fully automated hands-off approach, a gated manual approval process, or a hybrid of both.
What are agent software updates?
Agent software updates are packages pushed to each of your endpoint devices. These updates can range from minor patches to full version releases with new functionality. VIPRE Security releases agent software updates as needed, from every few months to a few times a year.
Software Updates vs Definitions
Definitions are used by the VIPRE Cloud agent to identify and remediate malware and are automatically updated multiple times per day, whereas software updates are updates to the agent software and can be gated by VIPRE Cloud before being pushed to your endpoint devices. This gated process gives you the ability to review the available update first, and either a) immediately approve for production, or b) try in a test environment first and then approve for production.
Production vs Test Environments
We understand that administrators often prefer to test software updates in a secluded environment before deploying the changes to their production devices. The VIPRE Cloud agent software update process is built around this potential need for a test environment vs. a production environment.
The Update Process
Scenario: VIPRE Cloud Agent version 1.2 currently exists on your production devices, but as the VIPRE Cloud Administrator, you've received an email notification that an update to VIPRE Cloud Agent version 2.1 has been released.
At this point, you have two options: deploy it to your test environment or skip the test process and deploy to your production environment.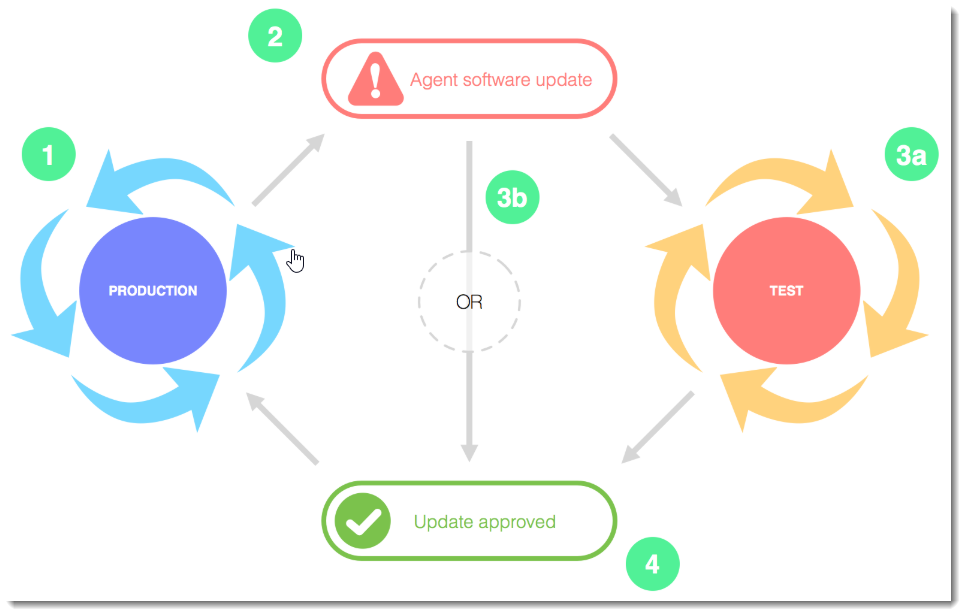
VIPRE Recommends
Use policies to separate your production devices from your test devices. By creating a specific "Test Policy" for a small group of non-critical devices (e.g., IT workstations or a test server), you can safely deploy new agent versions to this group without affecting your broader network.
How Updated Agent Software Gets to Endpoints
The agent update consists of two parts: Approval and Deployment.
Part 1: Approval
Admins choose whether to manually approve the new software or auto-approve it for use in production via VIPRE Cloud's Update Agent settings.
- Notify (aka Manual Approval): VIPRE Cloud displays a notification on the SETUP > Deploy Agents page each time an agent software update is available; before any devices can receive the updated agent software, you must click Approve Version in the console
 |

|
- Auto Approve: VIPRE Cloud automatically approves the new agent version as soon as it is released; depending on how you've configured your policies, the updated software could then be automatically deployed on your devices
To configure your Update Agent settings:
- From within the VIPRE Cloud web console, navigate to SETUP > System > Settings
- Scroll down to Update Agent, then select Auto approve or Notify
- Click Update Settings in the top right corner

Part 2: Deployment
Admins can configure whether to enable automatic installation of the updated VIPRE Cloud Agent on endpoints via policy settings, located in MANAGE > Policies > [Your Policy Name] > Agent > Updates & Communication.

- When Software Updates is selected, devices in this policy will automatically download and install the update as soon as it is approved
- If not selected, devices in this policy will not receive updated agent software until manually updated
Setting the Right Amount of Control
There are two sets of options that work together to control the amount of automation used to deploy agent software updates.
- The option Auto approve or Notify first (manual approval) is set in System > Settings > Update Agent.
- The option to control the deployment of automatic updates to all, some, or none of your agents is set in Policy > Agent > Updates & Communication.
| Goal | System Setting - Update Agent | Policy Setting - Automatically update VIPRE agent software |
|---|---|---|
| Fully automated: New agent software is approved and deployed to all devices immediately upon release | Auto Approve | Enabled |
| Gated: Nothing happens until you click "Approve Version" in the console; once you do, all devices update immediately | Notify | Enabled |
|
Full manual control: Nothing happens until you click "Approve Version" and devices won't update until you either:
|
Notify | Disabled |
| Staged: New agent version is approved and ready for use, but devices in this policy will remain on their current agent version until you manually install the updated agent | Auto Approve | Disabled |
Troubleshooting & FAQ
Troubleshooting the most common issues typically starts with verifying that you are using the latest version of the VIPRE Cloud Agent on your endpoints.
Verify Agent Version
From within the VIPRE Cloud web console, you can check the Agent column in the Devices list

Review the Latest Release Notes
When updating the VIPRE Cloud Agent, always review the most recent release notes. If you encounter unexpected behavior, such as missing features or performance issues, the release notes provide critical information on Known Issues and Workarounds, as well as any Special Instructions for manual actions, such as enabling a new feature within a policy, to ensure the agent functions as intended.
I've approved the updated VIPRE Cloud Agent version. Why are my devices are still showing the older version?
Check the policy those devices are assigned to to ensure Automatically update VIPRE agent software is enabled. If it is not enabled, and you want your devices to automatically install updated agent software, enable this setting.
If it is enabled, check the device status by ensuring your endpoints have an active heartbeat with the console to receive the update command promptly by going to MANAGE > Devices
Example:
| This screenshot shows an endpoint that hasn’t been seen in approximately one week and is running the previous version of the Linux agent. This endpoint likely is not online and would not be able to receive the Update Devices command. |  |
| This screenshot shows an endpoint with an active heartbeat and is running the previous version of the Linux agent. This endpoint should be able to receive the Update Devices command. |  |
| This screenshot shows an endpoint with an active heartbeat and the updated version of the Linux agent. |  |
System Requirements
| Component | System Requirements |
|---|---|
| Endpoint Cloud Web-based Console |
Web Browsers
|
| VIPRE Update Proxy |
|
| VIPRE Agent for Windows |
Operating Systems
Hardware
Miscellaneous
Supported Web Browsers for HTTPS URL Protection
|
Bugs Fixed in this Release
- VPBAGENT-40303: Windows stop error was appearing randomly when a previous version of the VIPRE Agent was running during Windows Easy Transfer file transfers
- VPBAGENT-8545: Previous version of VIPRE Agent was sometimes failing installation
- VPBAGENT-40907: Drivers were left after uninstalling Agent
- VPBAGENT-40862: Agent upgrades were creating duplicate AV/FW provider keys
- VPBAGENT-40848: Agent delayed updating definitions until after the agent upgrade was completed
- VPBAGENT-40845: There was an extra VIPRE folder in the programdata directory
- VPBAGENT-40822: Offline package failed to apply
- VPBAGENT-40794: PMAgent log was not being created after the initial service start up
- VPBAGENT-40689: Custom Agent install directory was not being maintained after an agent upgrade
- VPBAGENT-40417: Agent was reporting that definitions still needed to be updated even after having already updated them
- VPBAGENT-40232: Persistent VIPRE Cloud Agent installation failures were occurring
- VPBAGENT-7483: The ‘sbhips’ service was stopping after agent upgrade
- VPBAGENT-3187: IPv6 trusted zones were not working
Known Issues
| Ticket Number | Description/Workaround |
|---|---|
| VPBAGENT-40793 |
VIPRE Agent for Windows crashes unexpectedly during VTE (VIPRE Threat Engine) package update on Windows Server 2008 r2. No workaround needed; service restarts automatically after 1-2 minutes. |
| VPBAGENT-40121 |
When using Google Chrome, if Malicious URL Blocking is enabled, remediation of malicious files is not complete and files may remain in the Downloads directory. Workaround: VIPRE's layered security will continue to protect you. Ensure that you have Advanced Active Protection enabled. |