This guide to VIPRE Email Security Cloud Add-ons will walk you through each add-on, explaining what it does and how to use it.
What does each add-on do?
Start by selecting a topic below to learn more about that particular add-on.
Attachment Sandboxing
Attachment Sandboxing uses advanced sandbox technology to quarantine harmful email attachments that can evade other antivirus or anti-spam software. It can even identify brand-new malware and viruses. And Attachment Sandboxing does all this before the email even reaches your inbox.
How does Sandboxing affect me?
Attachment Sandboxing, like other VIPRE Email Security software, acts in the background to protect you. In a perfect world, no one would ever try to send you a harmful file. However, we know better. Harmful files are transferred as attachments through email all the time, including viruses, Trojans, adware, and other forms of malware. Some of these are caught by signature-based checks, particularly if they are files that have been seen before by other people. Sandboxing scans new, unknown email attachments, flags newly identified harmful items and delivers this information in your Email Security Quarantine Report.
What happens to my emails when Sandboxing checks them?
If an email does not contain any attachments or only non-supported attachments, it is delivered to you immediately (after all the standard Email Security checks, such as anti-spam).
If an email message contains supported attachment types, each attachment is extracted from the email and "detonated" (i.e., executed) within an isolated sandbox virtual machine. Advanced AI technology analyzes the attachment's behavior. This process does take some time, and processing time may depend on how many of your peers have also recently received emails with attachments.
If the attachments are clean, you’ll receive your original email with the attachments, as usual.
If an email message contains attachments that are identified as potential malware by Sandboxing, those items are sent to quarantine just like other undesired content. You'll find these items on your Quarantine Report, which shows all suspect emails and potentially malicious file attachments. If you do not receive a Quarantine Report, check with your administrator.
In the special case where an email with attachments takes a very long time to process, you may receive a "pre-notification" email that consists of the original email with attachments stripped off of it. This notification is intended to alert you to a pending message from the sender that is "in queue". You may be able to respond based solely on the email content without the attachments, or you can wait for the final result of the Attachment Sandboxing scan. If the attachments are clean, Attachment Sandboxing re-delivers the original email with all attachments intact.
As part of this process, you may see that your email has:
- A subject beginning with [SANDBOX]
- Its original attachments removed, with a text list of attachment filenames instead
- A warning at the bottom
What's the difference between a suspect and a malicious attachment?
Attachment Sandboxing uses advanced sandbox technology to test files within a virtual environment and see if they attempt to perform harmful activities or otherwise act suspiciously. The behavior of the attachment under test is compared to the past observed behavior of millions of known malware samples and known benign samples. This comparison is a statistical analysis that necessarily involves a similarity rating within a range.
- A suspect attachment is one that has exhibited odd (but not immediately harmful) behavior. It may have attempted to take action without permission, like open a web page or launch other programs, or it may have performed other suspicious activities that have similarly been observed in other malware. Not all suspect files are bad, but they have performed actions that are typically unexpected in well-behaving software.
- A malicious attachment is one that either contains other known malware or attempts to perform malware-like actions. It clearly attempted to infect or damage a user's PC to some degree during testing or clearly exhibits behavior very similar to other malware.
Malicious attachments are quarantined and cannot be released due to the risk they pose; suspect attachments are also quarantined but may be released on your personal recognizance (if your admin has granted permission). We do NOT recommend releasing suspect attachments unless you know and trust the sender or have proper protections in place for the testing of the attachment.
Warnings generated by Attachment Sandboxing
If a delay is detected while Attachment Sandboxing is processing one of your emails, you may receive a notification message consisting of the content of the original email with attachments removed.
These warnings are described below for your reference.
- Attachments have been temporarily removed
- Multiple attachments that could not be checked
"This email contains one or more attachments that have been temporarily removed while we check them for malicious code."
The full text of the message is
This email contains one or more attachments that have been temporarily removed while we check them for malicious code. We will redeliver the email with any original attachments once processing is complete.
Please exercise caution if you choose to release this email before it is checked.
What does this mean?
Attachment Sandboxing is currently analyzing files that were sent to you. Your email message is intact, but Attachment Sandboxing has pulled out the attachments to test them. There could be a delay while these files are tested.
Email release link and portal
If your administrator has enabled it, you will also have a link at the bottom of your email to release the original message and attachments and receive them immediately.
Clicking the link takes you to the Email Security portal, where you have a few options. See the table below.
| Portal Text | What This Means | Actions |
|---|---|---|
| "This email contains one or more attachments that have not yet been checked for malicious code. Please exercise caution. Are you sure you wish to release this email? |
The email has not yet been checked. The attachment status is unknown. | You may release the unprocessed message and its attachments to your inbox. Exercise caution, however, as the attachments have not been verified as clean! |
| "Email has already been delivered to your inbox. You can not re-release it again. Please check your inbox." | The email has been checked. No risks were found. | None. The email has already been delivered to you. |
| "At least one attachment in this email was found to be suspicious. To release this email, please log in to the portal and release this email from your quarantined messages. Please exercise caution when releasing this email." | The message attachments are suspect in nature. | Processing has completed for this message, so you may no longer release it from this unprocessed state. You may, however, release the suspect message from quarantine if your administrator allows it. |
| "This email contains one or more attachments with malicious code. You cannot release this email." | The message attachments are malicious in nature. | None. Messages with malicious attachments cannot be released except by administrators. |
"This email contains multiple attachments which could not be checked for malicious code."
The full text of the message is
This email contains multiple attachments which could not be checked for malicious code. Please exercise caution when opening any attachments to this message.
What does this mean?
For some reason, Attachment Sandboxing was unable to fully analyze the files attached to your email. The attachments have, therefore, not been checked by Attachment Sandboxing, and (like any unchecked attachment) could be malicious — exercise caution when opening them.
Encryption
VIPRE Email Security Encryption enables administrators to automatically encrypt emails.
You can locate VIPRE Email Security Encryption on the left-side menu under Service Settings > Encryption.
This screen includes four pre-existing policies that have been created to enable users to quickly start using the service. These policies are disabled by default.
When enabled, the four predefined policies will trigger encryption when:
- An email body contains any of the following information which the user can choose from the checkboxes:
- Credit Card Number
- Social Security Number - US
- Social Insurance Number - Canada
- Danish Personal Number
- Swedish Personal Number
- Norwegian Personal Number
- The sensitivity of a Microsoft Outlook email is set to confidential
- The email sender pre-pends an email's subject line with the word “[Encrypt]” (not case-sensitive)
- This enables the end user to selectively encrypt an email that contains sensitive information but is not covered by any of the policies
- An email sent by an end-user contains at least one domain or address listed in the text box
- You can add specific domains or addresses for your organization in the text box below the policy in the web console
The recipient will receive a notification email with a link to read and respond to the encrypted email through a secure portal. First-time recipients will have to set up an account by inputting their email address and a password of their choice. They will receive an email to confirm their email address, after which they can start using the secure portal to read and respond to the encrypted email securely.
You can also brand these encrypted emails with your organization's logo.
Link Isolation
Link Isolation
VIPRE Email Security Link Isolation is like URL sandboxing for your email. When a user clicks on a URL within an email, the email is then scanned again and Link Isolation analyzes the URL. Rescanning the link at the time the user clicks on it, even if it happens days or months after receiving the email, provides stronger protection against zero-day threats.
Link Isolation's Workflow
An email comes in that contains a link, and your employee clicks on the link.
- VIPRE receives the URL analysis request
- The link analysis service then simulates a session using the same browser and client type as the requestor
- During the simulation, VIPRE investigates the behavior of the site and:
- Analyzes the site's behavior
- Provides the analysis results, determining whether the site is malicious, suspicious, or unknown and classification
- Collects screenshot of the website's appearance, features, and a "sanitized", safe version of the site that can be replayed in the user's browser
- If the URL is deemed suspicious, the user sees a message indicating restricted access to the site with either a warning message before proceeding or a complete block
Important
Your experience with Link Isolation is dependent on the options you choose here. Review all of the options below carefully to determine the best plan of action for your organization before implementation.
The scanning and analysis processes for Link Isolation can take up to approximately 20-30 seconds. During that time, important steps are taking place - some of these steps include loading the URL into the cloud browser, waiting for all embedded scripts to fully execute, and putting the page through a series of tests.
You can fine-tune the system by ensuring all sites/domains that are used frequently by your organization and are known to be safe have been added to the Allowed IPs/Domains tab.
Refer to Related Articles for details on how to configure Link Isolation.
End User: What to Expect
After Link Isolation is enabled, when an end user clicks a URL within an email, they will experience the following based on the Click through action chosen on the URL Filter Configuration tab and any customizations made to the templates (see Step 3 - Templates above):
| Warn and Allow | Block |
|---|---|
|
If you have chosen the click-through action of “Warn and Allow” you'll see a page similar to this. |
If you have chosen the click-through action of "Block" you'll see a page similar to this. |
|
At the bottom of the page, you'll see a small screenshot of the URL in question with options to:
 |
On the right side of the page, you'll see an embedded video called Phishing Defense Best Practices, which can be played from the Block page, PIP (picture-in-picture), or full-screen. 
At the bottom of the page, you'll see a small screenshot of the URL in question with options to:
 |
How do I use the add-ons?
Next, let's learn how to set up and configure each add-on.
Configure Attachment Sandboxing
Configure Attachment Sandboxing
Attachment Sandboxing uses advanced sandbox technology to quarantine harmful email attachments that can evade other antivirus or anti-spam software.
Attachment Sandboxing Settings
To get to Attachment Sandboxing settings:
- Click on Service Settings
- Select Sandboxing

-
Use Attachment Sandboxing default policy - If enabled, this default policy sandboxes all of the following attachment types:
- .com, .doc, .docm, .docx, .dot, .dotm, .dotx, .exe, .htm, .html, .pot, .potx, .pps, .ppsx, .ppt, .pptx, .rar, .rtf, .xls, .xlsb, .xlsm, .xlsx, .xlt, .xltm, .xltx, .zip
- .jpeg, .jpg, .pdf, .png (which are also scanned for QR codes that are converted to a URL, which is then checked for malicious behaviors)
Important
If you prefer to use a custom policy, this default policy must be disabled. Refer to Related Articles for details on how to create and enable custom Sandboxing policies.
-
Allow users to release emails - If enabled, messages to the end user also contain a link to the release delayed emails before the result from the sandbox is known; copies of attachments will still be analyzed; if the sandbox finds malicious attachments before this release link is used, the email cannot be released
- If disabled, messages to the end user will not contain a release link
- Send delay notifications - If enabled, notifications about delayed mail will be sent
Configure Encryption
Configure Encryption
VIPRE Email Security Encryption enables your system administrators to encrypt emails automatically.
Encryption Settings
To get to the Encryption settings:
- Click on Service Settings
- Select Encryption
Settings

- General - This is enabled by default; click the checkbox to disable or reenable the encryption of replies sent from the encryption portal
-
Policy Description- All of the following policies are disabled by default; includes four pre-defined policies that will trigger encryption under the following circumstances:
- The email body contains any of the following information:
- Credit card number
- US Social Security Number
- Canadian Social Insurance Number
- Danish Personal Number
- Swedish Personal Number
- Norwegian Personal Number
- The sensitivity of an Outlook email is sent to confidential
- The subject line of an email is pre-pended with "[encrypt]" (not case-sensitive)
- An outgoing email sent to a self-created list of addresses or domains
- To add email addresses or domains for outgoing encryption, enter the address in the text field and select the + plus sign
- The email body contains any of the following information:
Click Save at the bottom to commit all changes.
Important
You can create additional custom policies:
- Click on Policies then Advanced Policies
- Select For Outbound Mail
- Click Create Policy in the top right corner
- Under Settings, name your policy
- Under Rules, add your desired rules
- Under Actions, select Encryption [STOP] and click Add
- Click Create Policy
Branding
The Branding tab allows you to add your organization's identity to outgoing Encryption notifications.
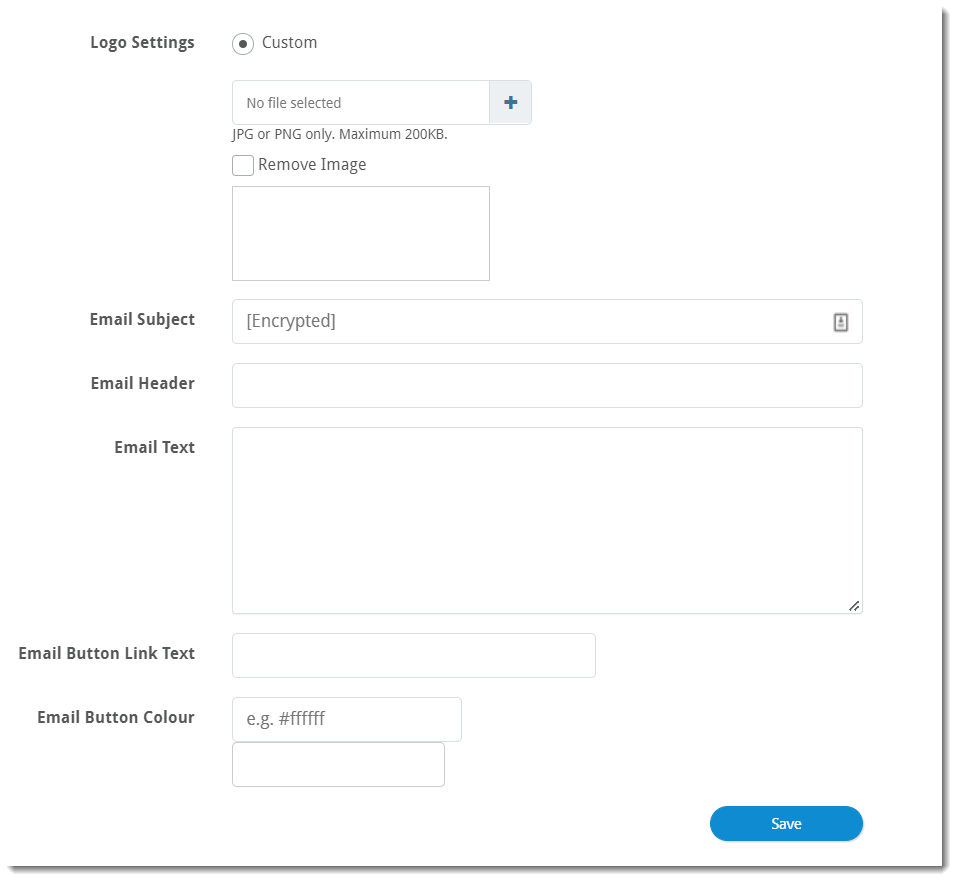
-
Logo Settings- Upload your organization's custom logo by clicking the blue plus sign; supported file types are .jpg and .png, and the maximum file size is 200KB
- You can also remove your logo by placing a checkmark next to Remove Image
- Email Subject - By default, emails that start with the subject line "[Encrypt]" will be encrypted automatically
- Email Header - Customize text included after the Sender's email address
- Email Text - Customize any text you want to add to the email body below the Email Button
- Email Button Link Text - Customize the text of the button
- Email Button Colour - Customize the color of the aforementioned button

Sending and Receiving an Encrypted Email
To send an encrypted email, end users need to know how your organization's Email Security Cloud administrator has configured the encryption policy to be triggered.
This trigger mechanism (called the Policy Description) might be based on:
- Inclusion of sensitive information
- Outlook email sensitivity level
- Pre-pending the subject line with [Encrypt]
- The receiving email address or domain
The receiving party will get a notification email. This email's appearance and subject will depend on how your organization's Email Security Cloud administrator has configured the Encryption service. It will contain a button or link that the recipient can click to read and reply to the encrypted email.
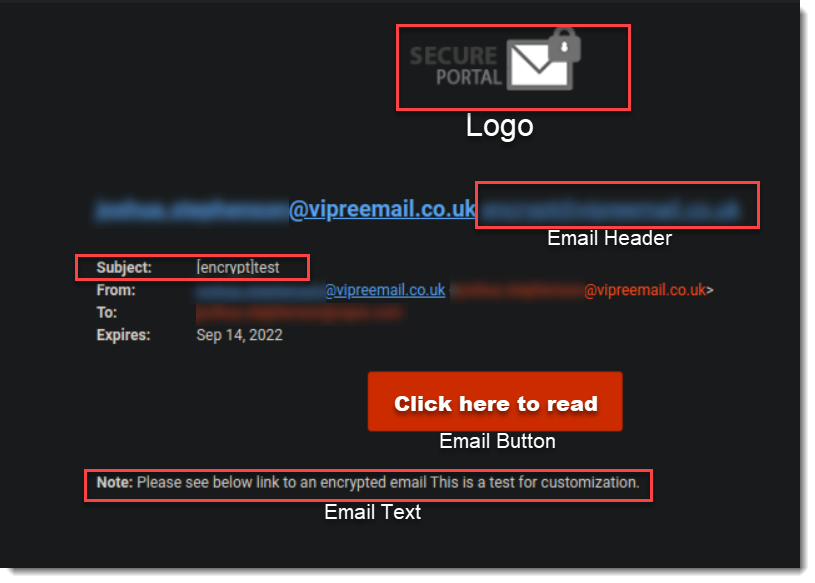
Configure Link Isolation
Configure Link Isolation
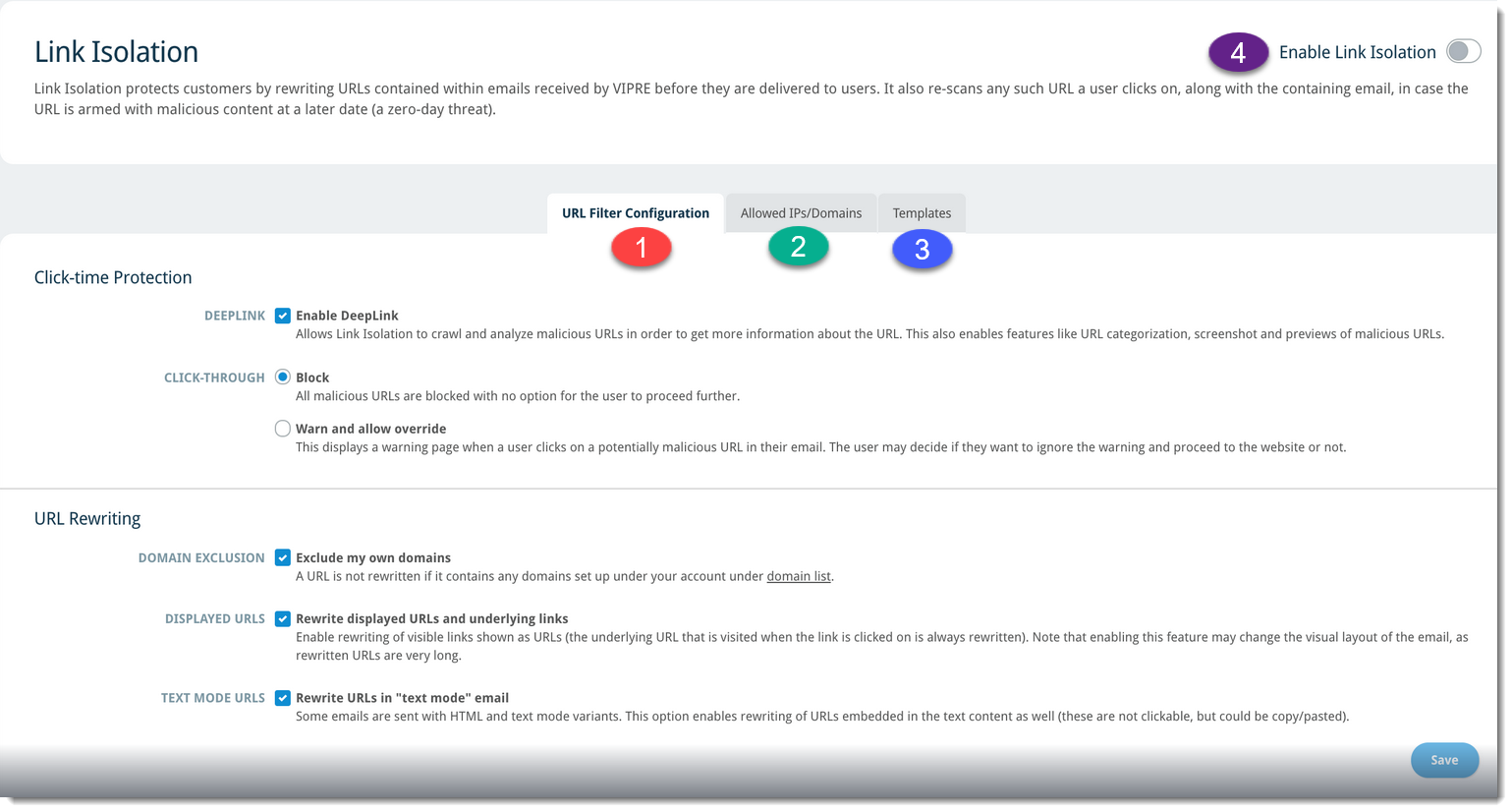
To configure the VIPRE Email Security Cloud Link Isolation add-on, complete the following steps:
- From your Email Security Cloud admin portal, click on Service Settings in the left-side menu
- Select Link Isolation, then select a tab below to learn about the settings for that option
URL Filter Configuration
- On the URL Filter Configuration tab, select from the following options:
- Click-time Protection
- Enable Deeplink: This option allows Link Isolation to perform deep, cloud-based scanning to analyze malicious URLs and obtain more information; also enables URL categorization and screenshots/previews of malicious URLs
- Click-Through > Block: Blocks all potentially malicious URLs that have been clicked in the email; unable to proceed
- Click-Through > Warn and allow override: Displays a warning when potentially malicious URLs have been clicked in the email; gives the option to ignore the warning and proceed to the website
- URL Rewriting
- Exclude my own domains: URLs containing any of the domains you've added to your account will not be rewritten
- Rewrite displayed URLs and underlying links: Visible links shown as URLs will be rewritten; this may alter the appearance of the email as rewritten URLs can be quite long
- Rewrite URLs in text mode email: Rewrites URLs both in HTML and text mode; this may alter the appearance of the email as rewritten URLs can be quite long
- Click-time Protection
- Click Save
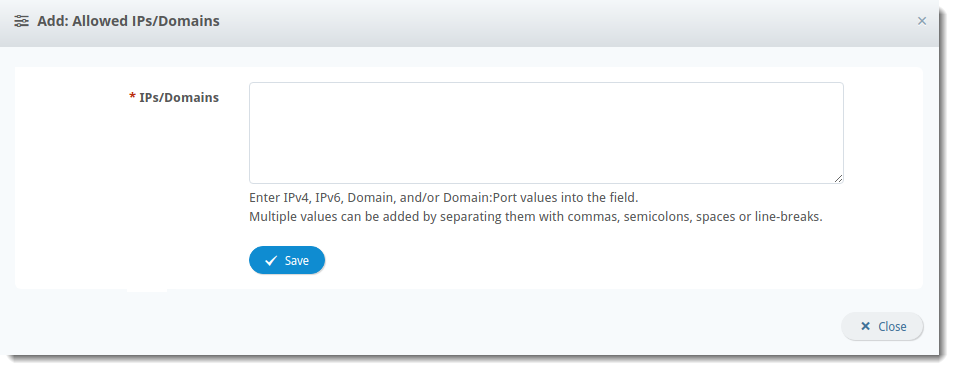
Allowed IPs/Domains
- Click on the + plus sign on the left side of the screen
- Type the IP address or domain in the text box - when adding multiples, supported separators are commas, semicolons, and space
- Any trusted IP address or domain can be added to this list as Link Isolation does not rewrite IP addresses or Domains on this list
- VIPRE recommends only adding trusted domains, like domains associated with your organization, to the Allowed IPs/Domains list
- Click Save
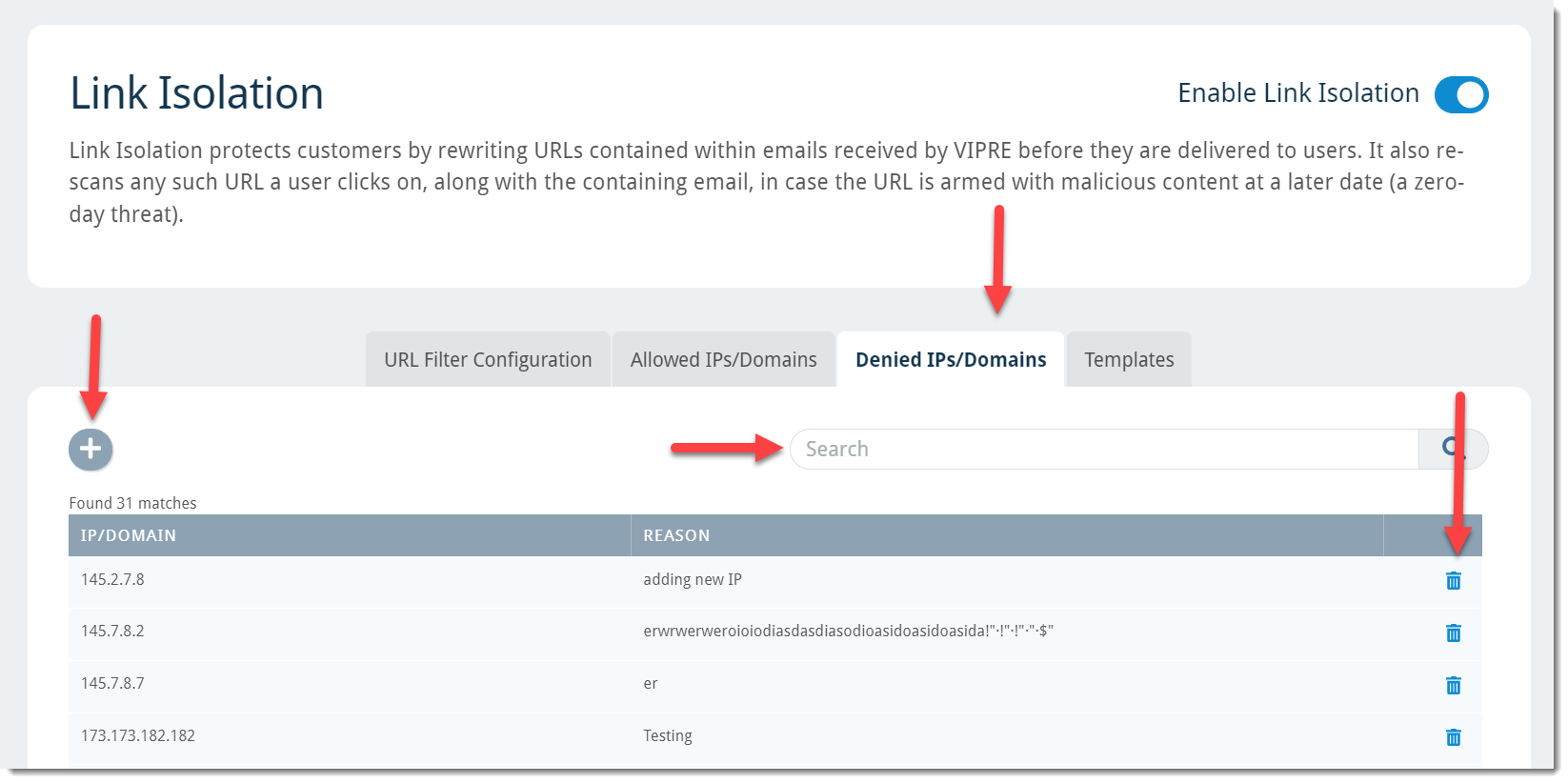
Denied IPs/Domains
To add an IP address or domain that you want to deny:
- Click on the + plus sign on the left side of the screen
- Type the IP address or domain in the text box
- Any untrusted IP address or domain can be added to this list
- Click Save
To search for a previously denied IP address or domain:
- Type the IP address or domain in the search box and press Enter
To delete a previously denied IP address or domain:
- Locate the desired IP address or domain and click the trash icon on the right side of the screen
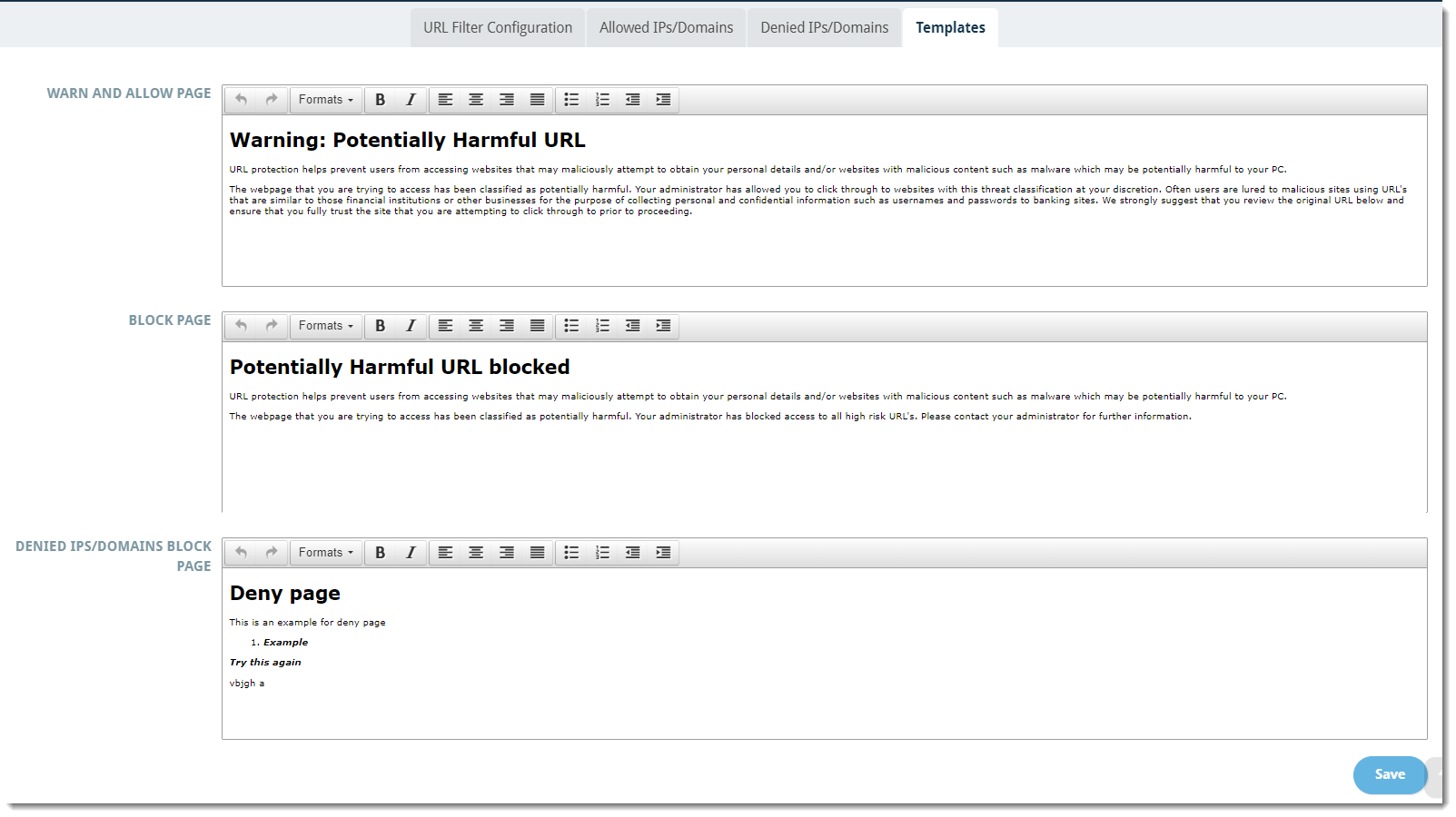
Templates
- This allows you to customize the message that your users see:
- When they click on the malicious URL based on whether you chose to Warn and Allow or Block Page under URL Filter Configuration
- When attempting to access an IP address or domain that has been denied
- Click Save
Enable Link Isolation
Once you've gone through the configuration options detailed in the tabs above, you're ready to enable Link Isolation.
- Scroll to the top of the screen and click the toggle next to Enable Link Isolation in the top-left corner
Congratulations! Link Isolation is now configured and enabled.

