Product release information for VIPRE Cloud Agent for Windows 13.2.8636, released on 2024 August 7, revised on 2024 August 9.
What's New
We have released a new custom build of the VIPRE Cloud Agent with the following updates:
Device Control
The VIPRE Cloud Agent for Windows now supports Device Control, including Mobile Device support.
EDR/ESC - Device Control
Device Control for Windows endpoints allows for the administration of external devices interacting with agents. This option is useful for limiting how users may transmit sensitive information to third-party devices, as well as protecting the endpoint from potential third-party threats.
Important
Device Control requires VIPRE Cloud Agent version 13.2 or higher.
- Review the latest release notes to find the most recent version of the VIPRE Cloud Agent for Windows
- Download and install latest VIPRE Cloud Agent for Windows
Introducing Device Control
Endpoint Security - Device Control Comparison
The table below compares Device Control between VIPRE Endpoint Security Server and VIPRE Cloud Endpoint products.
| Device Control | EDR, EDR+MDR, and Endpoint Security Cloud |
|---|---|
| CD/DVD Drives | ✅ |
| Removable Drives (e.g., USB drives) | ✅ |
| Mobile Devices | ✅ |
| Floppy Drives | ❌ |
Important
Device Control is a powerful feature that requires low-level access to device drivers. Because of this integration, Device Control can be incompatible with certain device drivers, particularly older versions. We recommend testing Device Control carefully on target systems before production deployment.
Configure Device Control
Use the steps below to configure different aspects of Device Control.
Enable Device Control
- From within the VIPRE Cloud console, on the left-side blue menu, under MANAGE, select Policies
- Choose your desired Windows policy
- Under the Agent tab, scroll down and click the checkbox to enable Device Control
- Select Save at the top
Device Control is now enabled in your policy. Remember that policy changes can take up to two minutes to update on your agent endpoints.
Device Control Exclusions
Create a new custom exclusion list or select an existing custom exclusion list.
- Click +Add Exclusion at the top-right corner of the screen
- Select Device
-
Choose to exclude device by Type or Specific Type
-
If you've chosen Type:
- Select the desired category (CD/DVD or Removable drives)
- Select the desired Bus (Any, ATA IDE, Firewire, SCSI, USB, PCMCIA)
-
If you've chosen Specific Type:
- Select the desired category (CD/DVD or Removable drives)
- Add value to Hardware ID (see example in text box)
- Add value to Serial ID (see example in text box)
-
If you've chosen Type:
Hardware ID and Serial ID details can be copied from the Device Control Report and pasted here to add an exclusion for a specific device. This is helpful, for example, when you've set a broad Device Control policy to block all removable drives but still require at least one particular endpoint to access a specific USB flash drive.
- Click Add
You can also add exclusions from the Device Control report. Continue reading below to learn more.
Device Control Reports
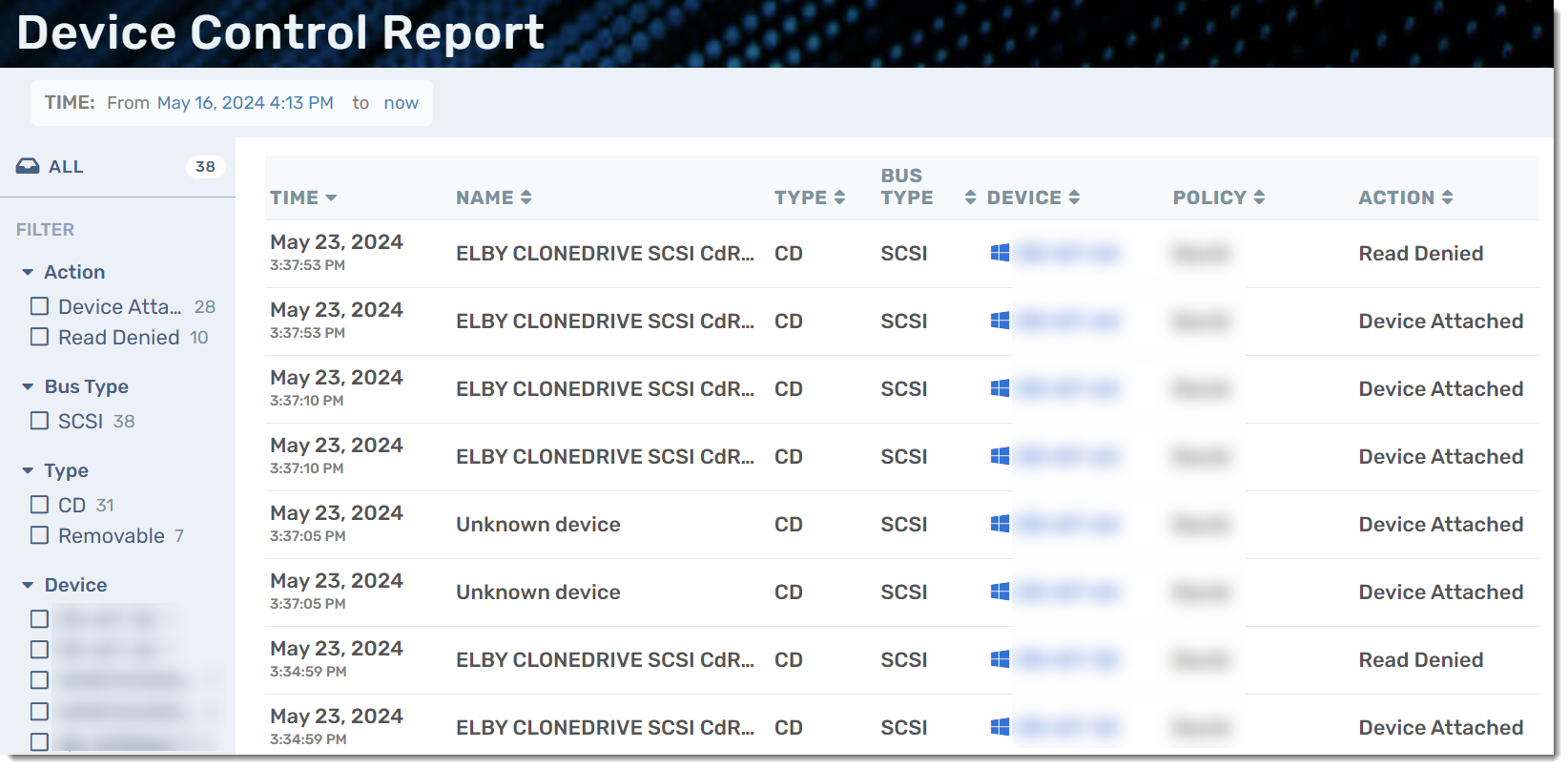
To add exclusions from the Device Control Report, select a specific event and click Add to Exclusion.
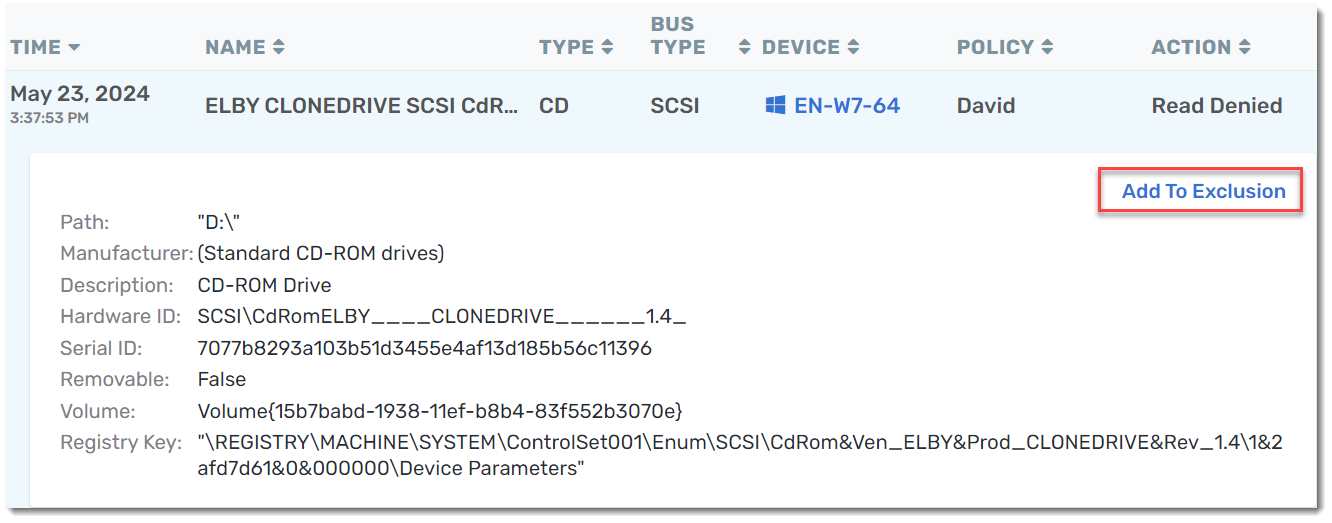
This will bring up the option to add the exclusion to an existing Exclusion Group or to create a new list. Once you select your desired exclusion list, you'll notice that Category, Hardware ID, and Serial ID are automatically filled in based on the device in the event you selected in the Device Control Report.
Review the auto-filled information and click Add when ready.
Other updates include:
- We have made a number of improvements to the VIPRE Cloud Agent to harden its operation, ensure that unexpected network events don’t cause the agent to fail to load
- VIPRE Cloud Agent is now digitally signed using a VIPRE Security certificate so that end users are no longer being prompted for missing signatures
- Remote Shell now supports copy-and-paste using CTRL+Shift+C to Copy and CTRL+
Shift+V to Paste- CTRL+C and CTRL+V are not supported within the VIPRE Remote Shell
- Various additional performance improvements
VIPRE Recommends
Keeping all software in your environment as up-to-date as possible is critical. New software releases often fix issues with older product versions that, unless addressed, could leave you vulnerable. As such, VIPRE recommends updating to the most recent version as soon as possible.
You can check the current status of older product versions on the VIPRE Product Lifecycle Matrix to learn when support for specific product versions may end.
System Requirements
Fixed in this Release
- VPBAGENT-42197: Firewall/Web/DNS functionality was not working after a fresh Agent install
- VPBAGENT-42206: Threats were being quarantined even if chosen action was Remove
- VPBAGENT-42119: VIPREShell package wasn’t downloading after Agent install
- VPBAGENT-41721: When VIPRE install attempt was made with an incompatible software detected, it wasn’t actually installed after machine reboot
- VPBAGENT-41620: A combination of Domain Exclusions was causing Malicious URL Blocking for HTTPS to produce two VIPRE URL Inspectors per lookup but was not automatically closing them.
- VPBAGENT-41499: Some VIPRE Cloud Agents were not updating software versions after being approved
- VPBAGENT-40389: VIPRE Cloud Agent was causing SBAMSvc.exe to crash repeatedly
- VPBAGENT-41863: VIPRE Cloud Agent was causing sbwfw.sys to crash, resulting in a BSOD error - this was an issue when the network protection features were active and a malformed IPv6 packet was received
- VPBAGENT-42069: Post-install reboot loop occurring with definitions update failure with “SDK requires reboot” error
- VPBAGENT-41923: Firewall might show in Error status on Server 2016
Known Issues and Workarounds
This section lists issues that are known at the time of release. In some cases, these are bugs that we are working to resolve with a subsequent release. Other items may be due to causes outside our control, such as bugs with other vendors' software. In all cases, we have tried to provide a workaround for you to consider should you experience an issue.
If you have questions about a specific issue, please provide the ticket number below (if applicable) when contacting our Technical Support team.
Current Version
| Ticket Number | Description |
|---|---|
| VPBAGENT-41719 |
VIPRE Cloud Agent might cause BSOD errors when stopping the Agent.
While we work on testing the fix, temporarily disabling Exploit Protection while stopping or upgrading agents should prevent the BSOD. Exploit Protection can be enabled again after the agent is stopped. |
| VPBAGENT-41934 | Optical Drive could appear to be missing when performing a custom scan |
| VPBAGENT-42014 |
After migrating VIPRE Agents, gfibto.sys might cause a BSOD boot loop with the Fortinet client installed.
This is related to incompatible software removal when the Fortinet Firewall is installed.
Workaround: Disable the policy option: Agent > Incompatible Software > Handling > I understand that it may cause problems, but do not remove incompatible software for me. I will handle this on my own.
The Fortinet versions are identified as: FortiClient 4.0.2.0057 FortiClient 4.2.0.250 FortiClient 5.4.2.0860 FortiClient 5.6.6 |
| VPBAGENT-42068 |
SBAMSvc might cause VIPRE Agent BSOD error on Server 2019 Datacenter virtual machine
We have had one reported case of this incident with Windows Server 2019 with Agent version 13.1. |
| VPBAGENT-41586 | VIPRE Agent generating popup messages for URL Filtering Extension installation |
| VPBAGENT-41435 |
Recurring sbwfw.sys crash on Server 2019 Datacenter Virtual Machine with billions of network connections
Issue occurred with Agent version 13.0. It has not been reproduced with Agent version 13.2 and there is a low probability of it occurring. |
| VPBAGENT-42304 |
Device Control: Permission Denied error when attempting to mount CD/DVD when the CD/DVD device class is set to monitor, and removable drives and/or mobile device storage is set to blocked
Workaround: Ignore the error, as access for the CD/DVD is not actually blocked |
| VPBAGENT-42306 | Device Control: Mobile device storage option does not block iTunes sync |